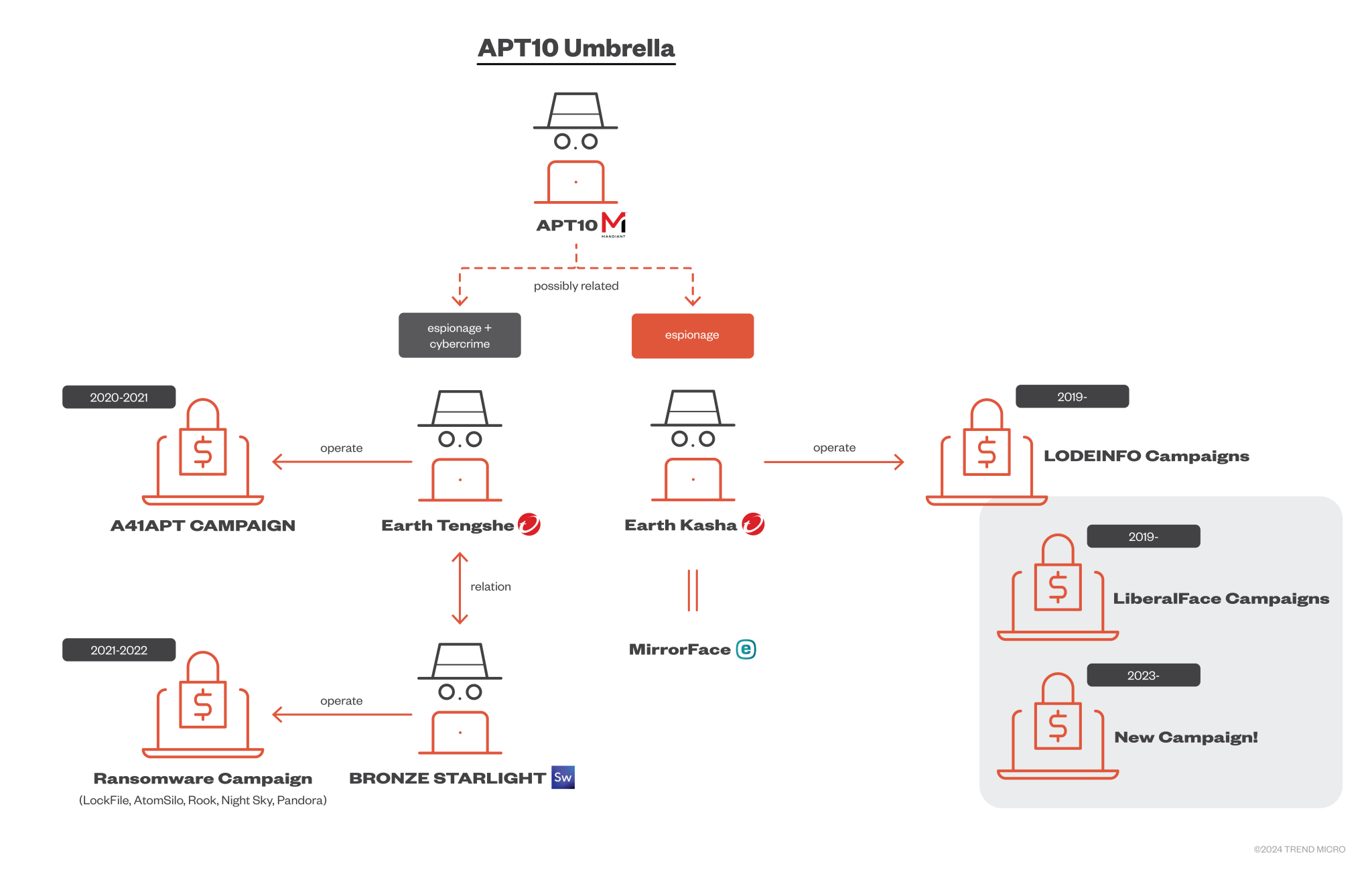
An overview of relationships of Earth Kasha | Image: Trend Micro
In a detailed report by Trend Micro, the emergence of a new LODEINFO malware campaign has been linked to Earth Kasha, a threat group operating within what the researchers term the APT10 Umbrella. This campaign reflects significant updates to Earth Kasha’s tactics, targeting government agencies and high-tech industries across Japan, Taiwan, and India.
LODEINFO, Earth Kasha’s custom backdoor, has been in use since 2019. The malware has undergone multiple updates, with its latest versions (v0.6.9 through v0.7.3) introducing advanced features such as enhanced credential theft and persistent footholds within compromised systems. According to the report, “LODEINFO is a backdoor exclusively used by Earth Kasha since 2019, serving as their primary backdoor. In this new campaign, however, it is just one option among several, showing its adaptability.”
The new campaign marks a shift in Earth Kasha’s target profile. While Japan remains a key focus, high-profile organizations in Taiwan and India have also been attacked. Exploited vulnerabilities include:
- Array AG (CVE-2023-28461)
- Proself (CVE-2023-45727)
- FortiOS/FortiProxy (CVE-2023-27997)
These vulnerabilities are abused to gain initial access, a notable evolution from the group’s previous reliance on spear-phishing emails. As noted in the report, “Earth Kasha has also employed different Tactics, Techniques, and Procedures (TTPs) in the Initial Access phase, which now exploits public-facing applications such as SSL-VPN and file storage services.”
Once inside a network, Earth Kasha deploys a variety of tools, including Cobalt Strike, MirrorStealer, and the newly identified NOOPDOOR backdoor. Their post-exploitation activities focus on data theft and persistence. Commands like vssadmin are used to copy registry hives, enabling the theft of credential data from Active Directory servers.
“Earth Kasha successfully compromised domain admin in most cases. After compromising domain admin, they deployed backdoors (LODEINFO or NOOPDOOR) to several machines by copying components over SMB and abusing schetasks.exe or sc.exe to achieve lateral movement.”
The report acknowledges the speculation surrounding Earth Kasha’s connection to APT10 but stops short of confirming it: “While some vendors suspect that the actor using LODEINFO might be APT10, we don’t have enough evidence to fully support this speculation. Currently, we view APT10 and Earth Kasha as different entities, although they might be related.”
Related Posts:
- APT10’s Latest Weapon: Unveiling the LODEINFO Malware Menace
- Cuckoo Spear Threat Alert: APT10 Targets Japan’s Critical Infrastructure
- Chinese APT Groups Continue to Leverage Open-Source and Custom Reconnaissance Tools in Cyber Espionage Campaigns
- JPCERT/CC Warns: MirrorFace LODEINFO & NOOPDOOR Malware Targeting Industry
- Earth Preta’s Cyber Arsenal Expands: New Malware and Strategies Target APAC Governments