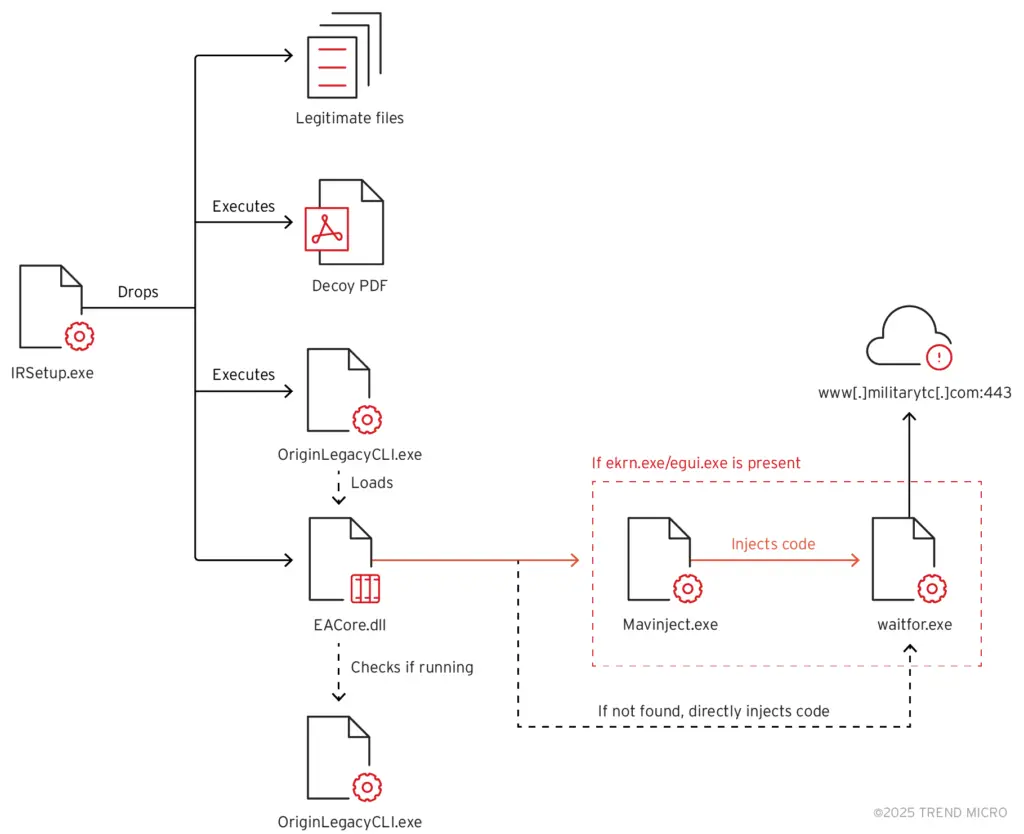
Earth Preta’s kill chain | Source: Trend Micro
Researchers from Trend Micro’s Threat Hunting team have discovered a new campaign by the advanced persistent threat (APT) group Earth Preta, also known as Mustang Panda, that utilizes legitimate and malicious components to evade detection.
The attack involves dropping multiple files, including a decoy PDF to distract the victim while the malicious payload is deployed in the background. The decoy PDF, designed to target Thailand-based users, asks for the reader’s cooperation in creating a whitelist of phone numbers to aid in the development of an anti-crime platform.
Earth Preta’s malware, a variant of the TONESHELL backdoor, is sideloaded with a legitimate Electronic Arts application and communicates with a command-and-control server for data exfiltration. The malware also employs the Microsoft Application Virtualization Injector (MAVInject.exe) to inject its payload into waitfor.exe when an ESET antivirus application is detected running.
“This injects Earth Preta’s payload into a Windows utility that’s used to sending or waiting for signals between networked computers., waitfor.exe, when an ESET antivirus application is detected running,” the researchers explained.
Additionally, Earth Preta APT group utilizes Setup Factory, an installer builder for Windows software, to drop and execute the payload. “This enables them to evade detection and maintain persistence in compromised systems,” the researchers added.
Trend Micro’s Threat Hunting team has been tracking Earth Preta’s activities since 2022 and has observed over 200 victims, primarily government entities in the Asia-Pacific region. The group favors phishing in their campaigns and has been known to use various malware variants, including DOPLUGS.
Cybersecurity professionals and organizations, particularly those using ESET antivirus applications, should be vigilant and take necessary precautions to protect themselves from Earth Preta’s evolving threats.
Related Posts:
- Earth Preta’s Cyber Arsenal Expands: New Malware and Strategies Target APAC Governments
- Earth Preta’s Targeted Asian Campaigns: The DOPLUGS Malware Threat
- ToneShell Backdoor Targets IISS Defence Summit Attendees in Latest Espionage Campaign
- Earth Estries’ Evolving Toolkit: A Deep Dive into Their Advanced Techniques
- CVE-2024-21887 and More: How Earth Estries APT Group Exploits VPNs & Servers