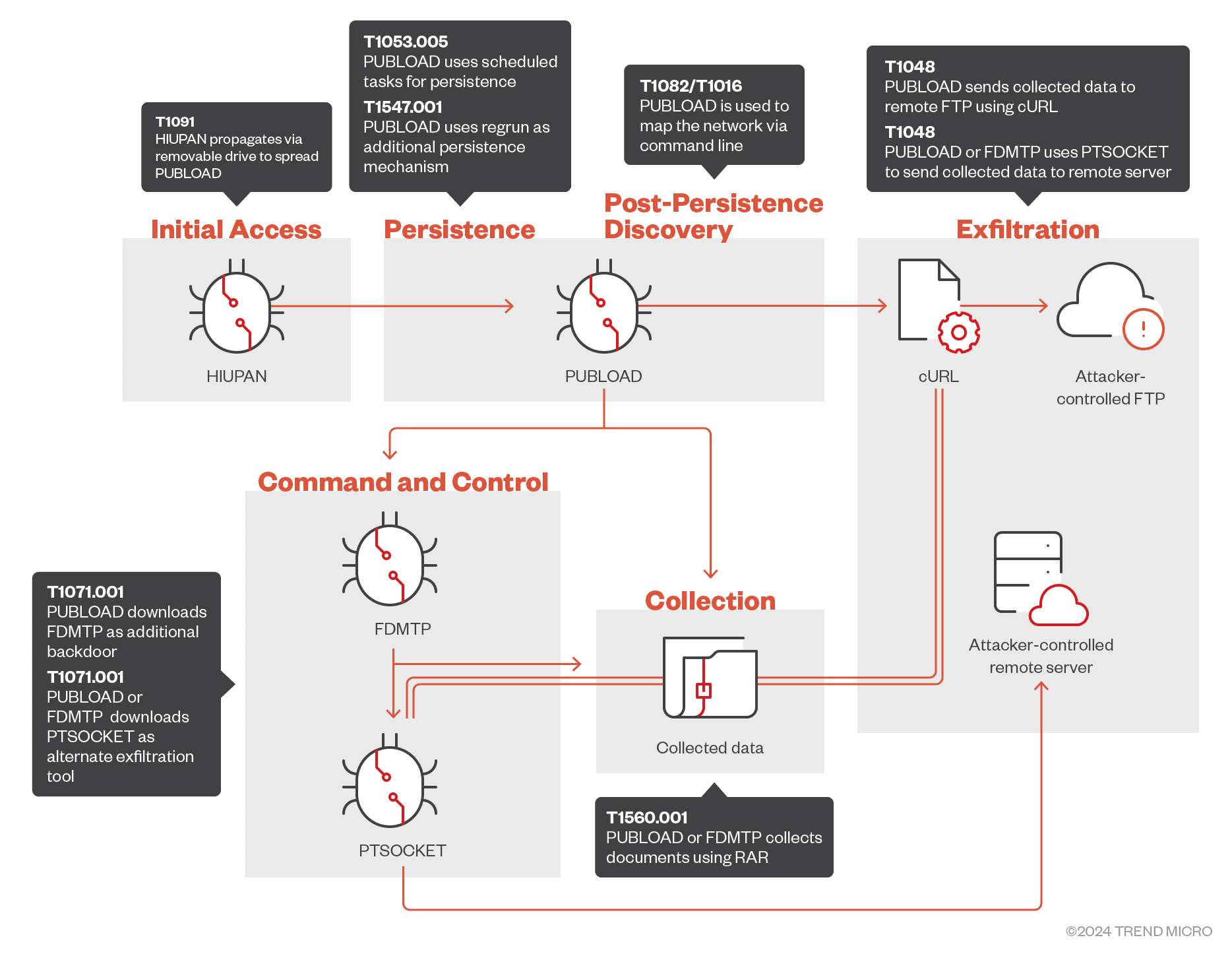
Attack chain | Image: Trend Micro
A new report from Trend Micro has revealed that Earth Preta, the notorious cyber espionage group, has significantly evolved its tactics and malware arsenal, posing a heightened threat to government entities across the Asia-Pacific (APAC) region.
One of the most notable changes in Earth Preta’s latest campaign is their use of a worm-based attack facilitated by a modified version of the HIUPAN worm. This variant now propagates via removable drives, serving as the entry point for PUBLOAD, the group’s primary control tool. HIUPAN automatically copies itself onto any plugged-in removable media, hiding its malicious files and baiting unsuspecting users into triggering its payload.
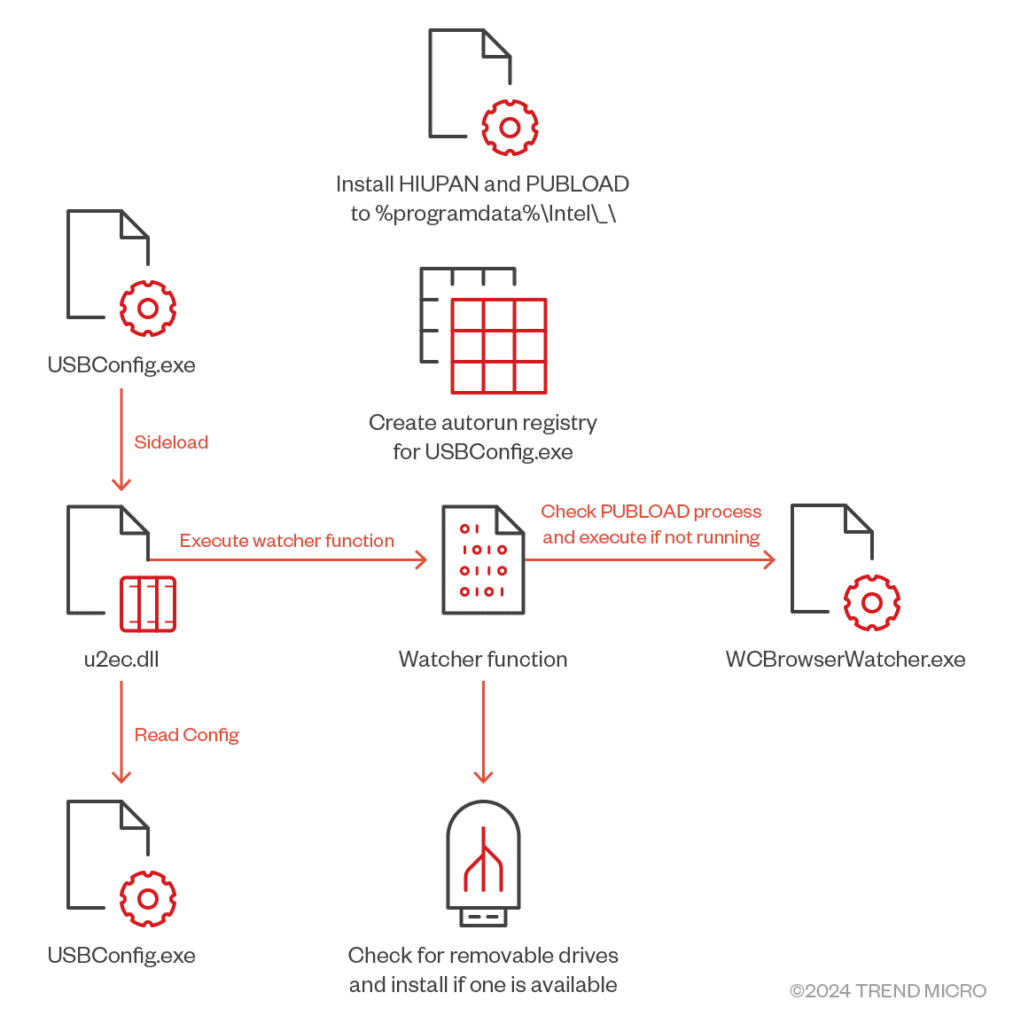
Unlike its predecessors, this new HIUPAN variant is easier to configure due to its external configuration file, enabling the worm to spread files listed in the configuration while maintaining persistence. The worm’s watchdog function checks for hot-pluggable drives, ensuring its continued spread and delivering the PUBLOAD malware across networks.
PUBLOAD plays a critical role in Earth Preta’s operations, executing commands for network discovery and data collection. It utilizes standard command-line tools, such as whoami and ipconfig, to gather network details and establish control. It also delivers additional malware components into the compromised systems, including FDMTP and PTSOCKET, which further expand Earth Preta’s control and exfiltration options.
- FDMTP: A newly discovered downloader that utilizes TouchSocket-based Duplex Message Transport Protocol (DMTP) for downloading and executing additional malware.
- PTSOCKET: A custom-built tool designed for multi-threaded file transfers, used to exfiltrate sensitive data from the compromised systems.
Earth Preta’s data exfiltration operations center around the use of RAR for compressing and archiving sensitive files before transmitting them to attacker-controlled servers. While previously exfiltration was handled via traditional FTP using tools like cURL, Earth Preta has integrated PTSOCKET as an alternative for stealthier file transfer operations. This dual method allows Earth Preta to remain flexible in its approach, maintaining a high level of evasion from detection systems.
Earth Preta has also shown significant improvements in its spear-phishing methods, rapidly evolving its delivery mechanisms. Recent campaigns, which began in June, involve emails containing .url attachments that deploy DOWNBAIT. This signed downloader and loader tool executes a chain of infection that culminates in the installation of CBROVER and PLUGX, sophisticated backdoors that facilitate data collection via tools like FILESAC.
Earth Preta’s campaigns are highly focused on specific government sectors, including foreign affairs, law enforcement, and military agencies. The decoy documents and malware samples used in these campaigns predominantly revolve around politically sensitive topics within the APAC region. Recent attacks have targeted entities in countries such as Myanmar, the Philippines, Vietnam, Singapore, Cambodia, and Taiwan, suggesting Earth Preta’s strategic focus on destabilizing or gathering intelligence from key geopolitical players in the region.
As Earth Preta continues to evolve its malware arsenal and attack strategies, organizations, particularly those in government sectors, must remain vigilant. The combination of worm-based propagation, multi-stage spear-phishing attacks, and advanced data exfiltration tools such as PUBLOAD, FDMTP, and PTSOCKET underscore the importance of adopting robust cybersecurity defenses.
Continuous monitoring for anomalous file transfers, regular updates to endpoint security systems, and heightened awareness of spear-phishing tactics are essential to mitigating the risks posed by Earth Preta’s evolving campaigns. With their demonstrated ability to adapt to new defenses, Earth Preta remains a formidable and ongoing threat to the APAC region.
Related Posts:
- Earth Preta’s Targeted Asian Campaigns: The DOPLUGS Malware Threat
- Government Agencies in APAC Targeted by Fake PDF Login Phishing Emails
- Veeam Users Beware: PoC Exploit for Critical CVE-2024-29849 Flaw Released
- Earth Lusca: China-Linked Espionage Group Targets Taiwan, Exploits Geopolitical Tensions
- Financial Institutions in Asia and Middle East Hit by Evolving JSOutProx Malware Campaign