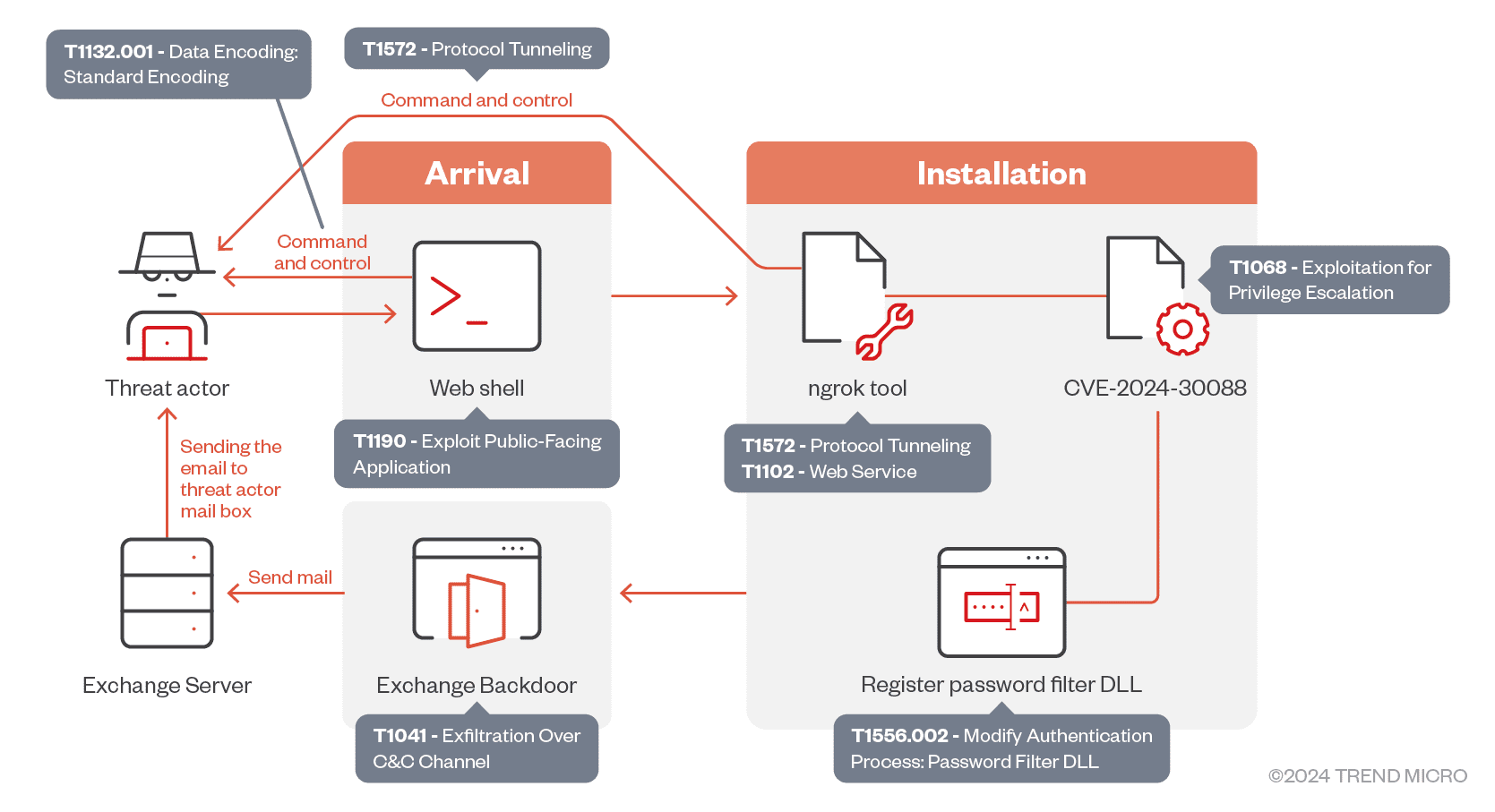
Attack chain | Image: Trend Micro
Trend Micro researchers have uncovered a series of advanced cyberattacks carried out by the threat group Earth Simnavaz, also known as APT34 or OilRig. This Iranian-linked cyber espionage group has been actively targeting governmental entities and critical infrastructure in the United Arab Emirates (UAE) and the broader Gulf region, leveraging sophisticated techniques to gain unauthorized access and exfiltrate sensitive information.
The report highlights a significant rise in cyberattacks attributed to Earth Simnavaz, with the group primarily focusing on the energy sector—notably organizations involved in oil and gas. According to the researchers, “Earth Simnavaz is focused on abusing vulnerabilities in key infrastructure of geopolitically sensitive regions”. The group aims to establish a persistent foothold in compromised environments, allowing them to weaponize these entities for future attacks.
One of the key tactics used by Earth Simnavaz involves deploying a sophisticated backdoor through Microsoft Exchange servers. This backdoor is designed to exfiltrate sensitive credentials, including account passwords, which are then relayed to the attackers. The report notes, “This new backdoor facilitates the exfiltration of sensitive credentials, including accounts and passwords, through on-premises Microsoft Exchange servers”.
Additionally, the group has been observed exploiting CVE-2024-30088, a vulnerability in the Windows Kernel, for privilege escalation. By integrating this vulnerability into its toolkit, Earth Simnavaz ensures its attacks remain effective while maintaining stealth.
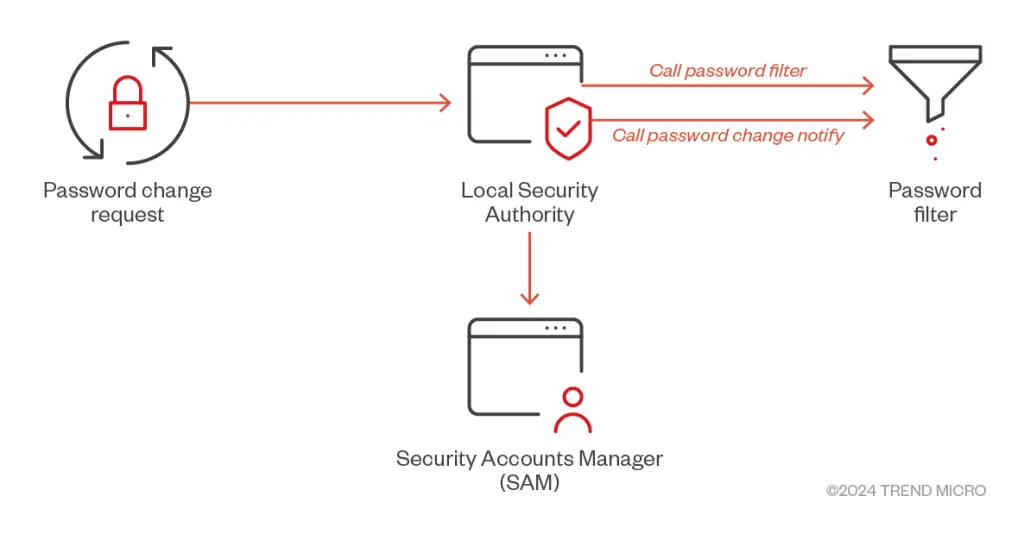
Earth Simnavaz has further refined its credential theft capabilities by abusing password filter policies. This method allows attackers to intercept and harvest plaintext passwords from compromised domain controllers or local machines. As detailed in the report, the threat actors can “capture and harvest every password from compromised machines, even after they have been modified“. This level of access grants them long-term control over targeted systems.
In the latest campaign, Earth Simnavaz has upgraded its toolkit to include ngrok, a legitimate remote monitoring and management (RMM) tool that allows attackers to create secure tunnels from local machines to the internet. Although legitimate, ngrok has been exploited to bypass firewalls and network security controls, enabling Earth Simnavaz to establish command-and-control (C2) communication with compromised servers without being detected.
Once inside the network, Earth Simnavaz also leveraged web shells to gain control over vulnerable systems. These web shells allow attackers to execute PowerShell commands, upload and download files, and ultimately spread their malware further within the network.
The activities of Earth Simnavaz highlight the growing cyber threat posed by state-sponsored groups in the Middle East. The report emphasizes that “Geopolitical tensions likely play a significant role in this surge, and government sectors in the Middle East and Gulf region should take these threats seriously”. The group’s primary objectives appear to be espionage and the theft of sensitive governmental information, which could have far-reaching consequences for national security and economic stability in the region.
Related Posts:
- Earth Lusca: China-Linked Espionage Group Targets Taiwan, Exploits Geopolitical Tensions
- Earth Preta’s Cyber Arsenal Expands: New Malware and Strategies Target APAC Governments
- Earth Baku APT Group Expands Global Reach with Advanced Techniques
- New KTLVdoor Backdoor Discovered in Multiplatform Intrusion Campaign Linked to Earth Lusca