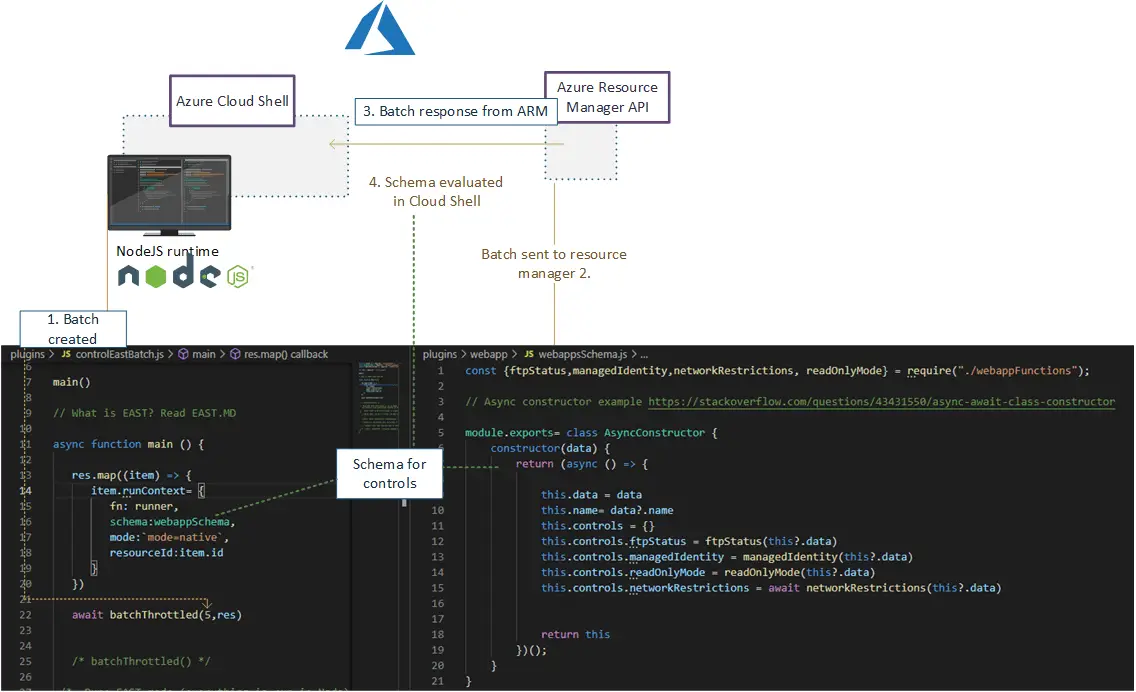
Extensible Azure Security Tool
Extensible Azure Security Tool (Later referred as E.A.S.T) is a tool for assessing Azure and to some extent Azure AD security controls. The primary use case of EAST is Security data collection for evaluation in Azure Assessments. This information (JSON content) can then be used in various reporting tools, which we use to further correlate and investigate the data.

Controls
EAST provides three categories of controls: Basic, Advanced, and Composite
The machine-readable control looks like this, regardless of the type (Basic/advanced/composite):
Basic
Basic controls include checks on the initial ARM object for simple “toggle on/off”- boolean settings of said service.
Example: Azure Container Registry adminUser
| Portal | EAST |
|---|---|
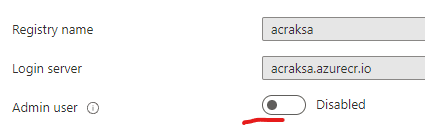 |
if (item.properties?.adminUserEnabled == false ){returnObject.isHealthy = true } |
Advanced
Advanced controls include checks beyond the initial ARM object. Often invoking new requests to get further information about the resource in scope and its relation to other services.
Example: Role Assignments
Besides checking the role assignments of subscription, an additional check is performed via Azure AD Conditional Access Reporting for MFA, and that privileged accounts are not only protected by passwords (SPN’s with client secrets)
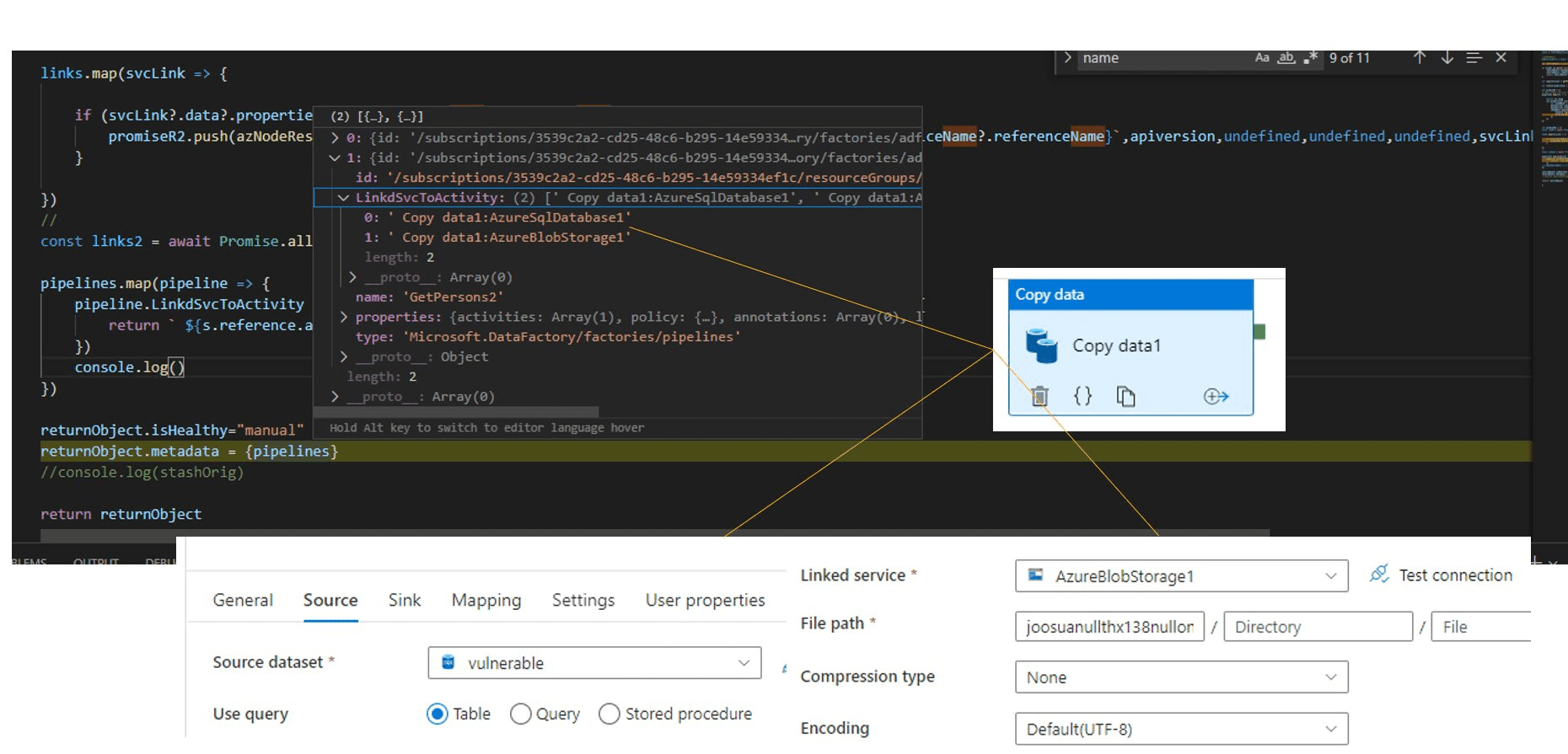
Example: Azure Data Factory
Azure Data Factory pipeline mapping combines pipelines -> activities -> and data targets together and then checks for secrets leaked on the logs via a run history of the said activities.
Composite
Composite controls combine two or more control results from pipeline, in order to form one, or more new controls. Using composites solves two use cases for EAST
- You cant guarantee an order of control results being returned in the pipeline
- You need to return more than one control result from a single check
Example: composite_resolve_alerts
- Get alerts from Microsoft Cloud Defender on subscription check
- Form new controls per resourceProvider for alerts
Reporting
EAST is not focused to provide automated report generation, as it provides mostly JSON files with control and evaluation status. The idea is to use separate tooling to create reports, which are fairly trivial to automate via markdown creation scripts and tools such as Pandoc
- While the focus is not on reporting, this repo includes example automation for report creation with pandoc to ease the reading of the results in a single document format.
Install & Use
Copyright (c) 2021 Joosua Santasalo