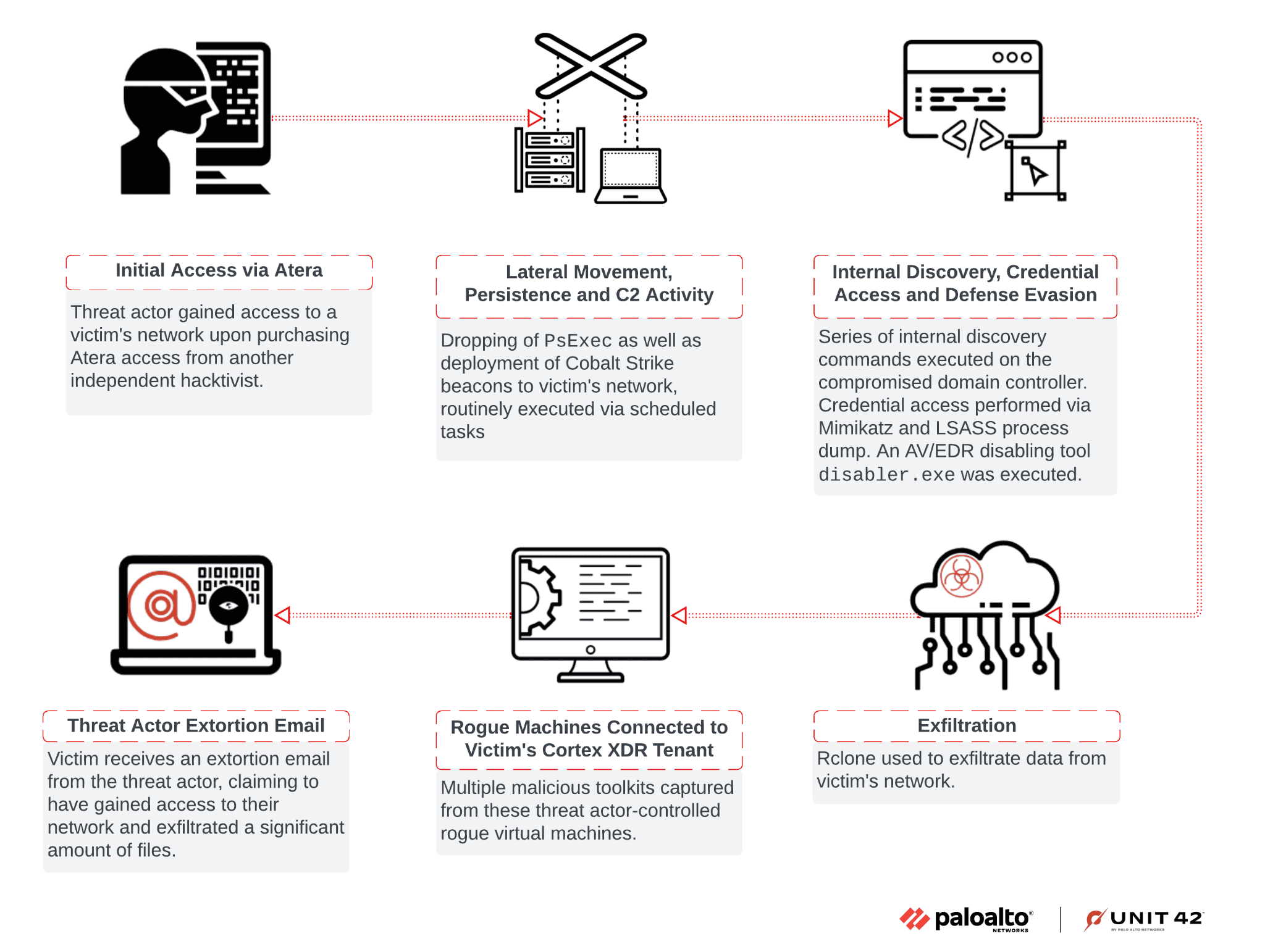
A high-level chain of events in the attack investigated by Unit 42
Unit 42 researchers recently uncovered the toolkit of an extortionist during an investigation where a threat actor attempted to evade endpoint detection and response (EDR) protections. The investigation revealed not only the tactics used by the attacker to bypass these defenses but also led to a critical discovery of the identity of one of the actors behind the attacks.
The attack centered on an EDR evasion tool called “disabler.exe,” which was part of a broader extortion scheme. Unit 42 explained, “Through the investigation process, we encountered two endpoints involved in the attack that were unknown to the client environment.” These rogue systems were initially intended for testing a bring-your-own-vulnerable-driver (BYOVD) attack, aimed at bypassing the Cortex XDR agent installed on the client network.
The threat actor behind this attack employed an advanced EDR evasion technique known as BYOVD. This method uses a compromised driver to disable key security functions, effectively allowing attackers to slip past defenses. “The particular tool, named disabler.exe, appears to use the publicly available source code from EDRSandBlast with small modifications,” the report highlighted.
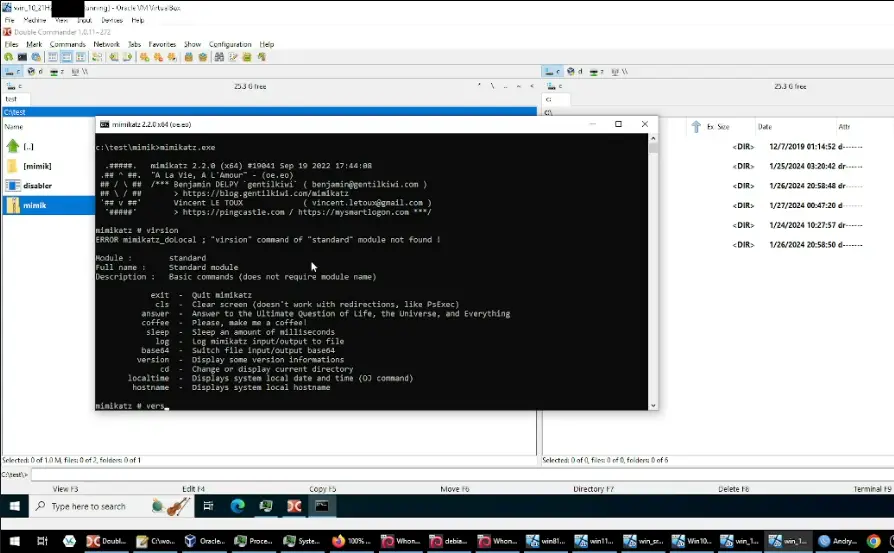
What makes this discovery particularly intriguing is how the threat actor inadvertently allowed investigators to view their toolkit in action. By connecting their virtual system to the client’s network, the attacker unintentionally gave Unit 42 access to their rogue endpoints. This connectivity provided valuable visibility into the attacker’s toolkit, offering insight into various tools, files, and even the attacker’s personal and professional background.
Among the files discovered on the rogue system were several copies of the EDR bypass tool along with video demonstrations showing its effectiveness. The recordings showcased how “disabler.exe” bypassed different EDR agents, allowing other tools, such as the credential-dumping software Mimikatz, to execute unhindered. Unit 42 noted, “Each recording shows a particular AV/EDR agent installed at that point that included the execution of the bypassing tool followed by a successful execution of Mimikatz,” revealing the extent of the threat actor’s confidence in their tool.
Additionally, the researchers discovered a series of artifacts that provided clues about the threat actor’s identity. These included a folder titled “freelance” and a series of aliases that led Unit 42 to cybercrime forums like XSS and Exploit, where similar tools were being sold. By connecting these aliases to known cybercrime profiles, investigators identified a user, “Marti71,” who had previously posted about AV/EDR bypass tools, suggesting they may have been involved in this scheme.
The evidence gathered by Unit 42 underscores the rising sophistication of tools used in extortion and ransomware schemes. The findings also highlight how underground forums and subscription-based cybercrime models contribute to the rapid evolution and proliferation of EDR evasion techniques. “These tools will likely continue to evolve in their attempts to exploit various security platforms,” warned Unit 42 researchers, stressing the need for organizations to adapt their defenses in response.