efiXplorer – IDA plugin for UEFI firmware analysis and reverse engineering automation
Supported versions of Hex-Rays products: every time we focus on the last versions of IDA and Decompiler because trying to use the most recent features from new SDK releases. That means we tested only on recent versions of Hex-Rays products and do not guarantee stable work on previous generations.
Why not IDApython: all code developed in C++ because it’s a more stable and performant way to support a complex plugin and get the full power of the most recent SDK’s features.
Supported Platforms: Win, Linux, and OSX (x86/x64).
Key features
Identify available Boot Services automatically
Annotate assembly code automatically with available Boot Services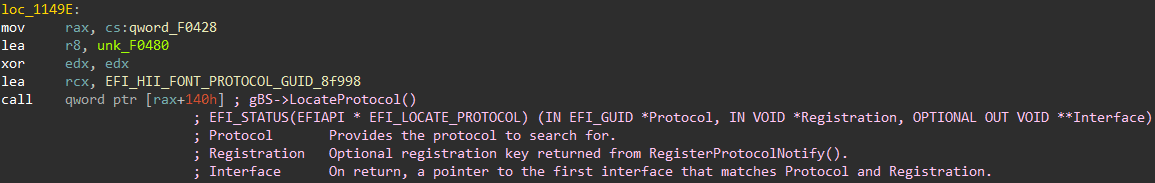
Identify available Runtime Services automatically
Annotate assembly code automatically with available Runtime Services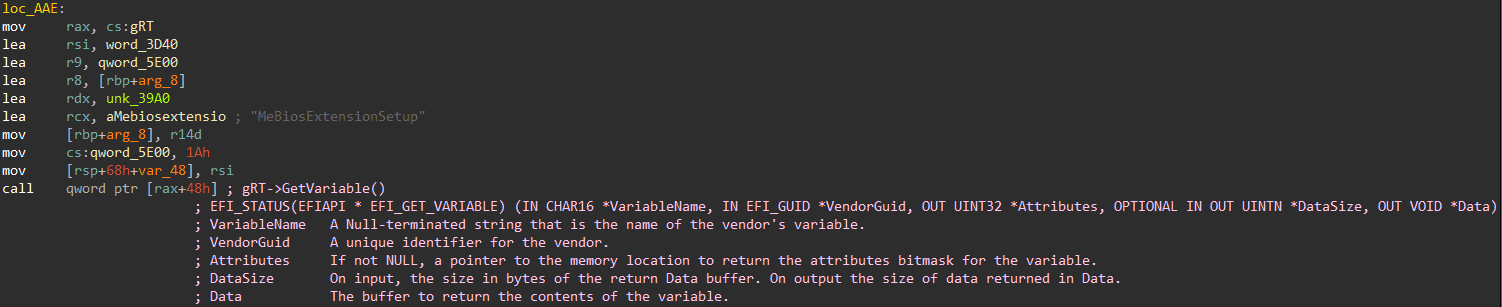
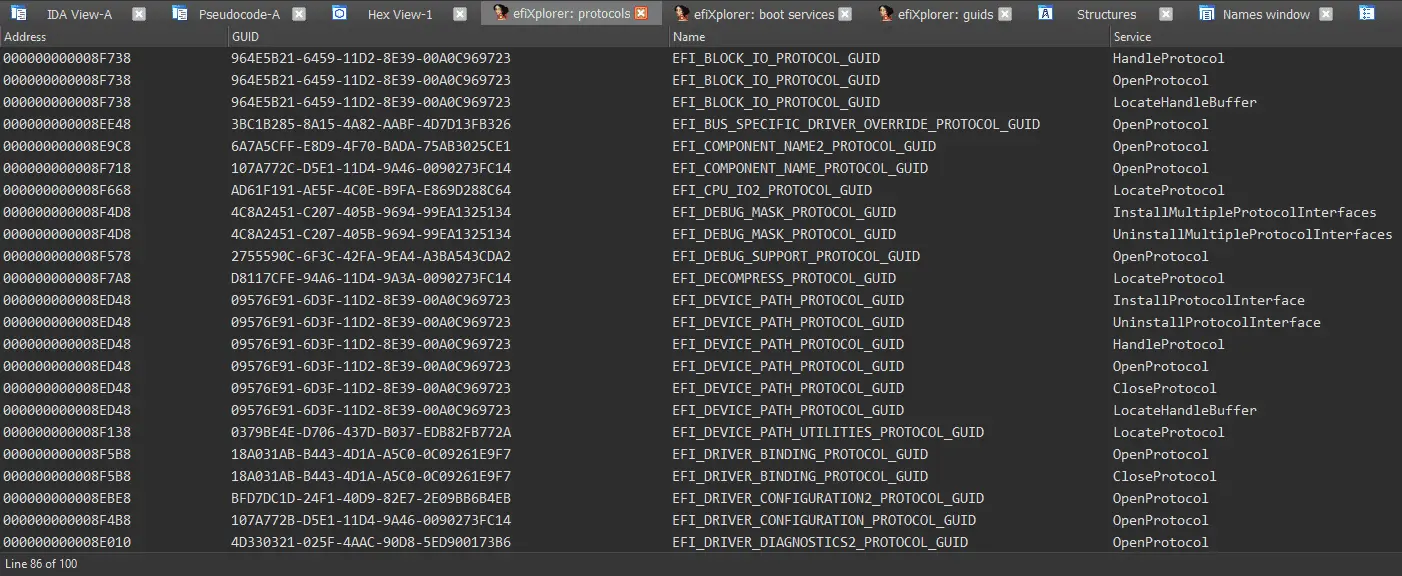
Identify available EFI Protocols automatically
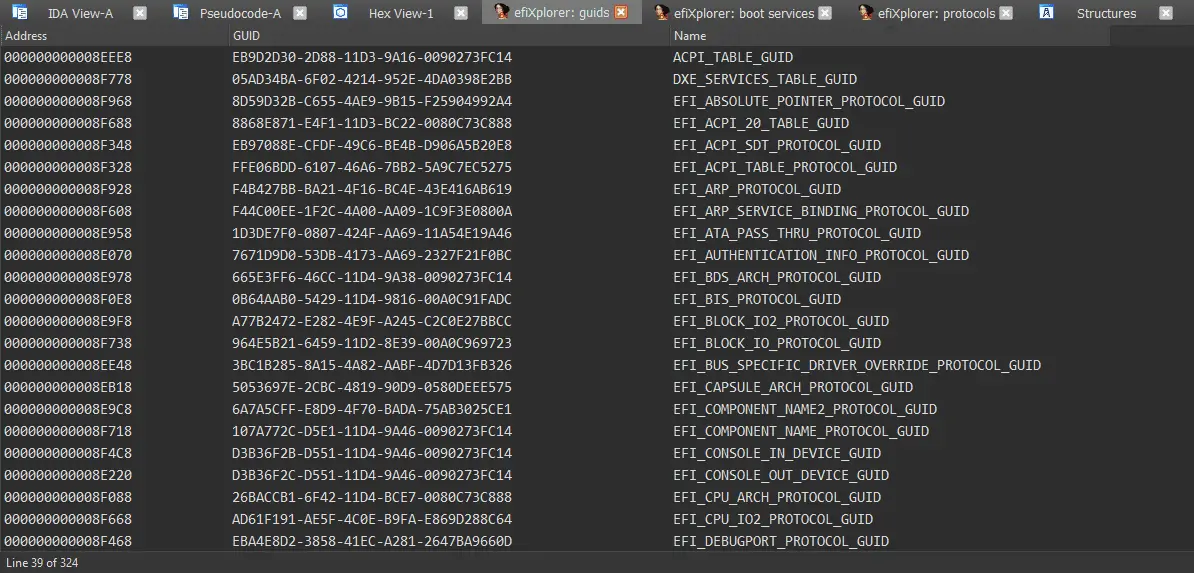
Identify known EFI GUID’s
efiXplorer Architecture
From the beginning of the project, we focus on building extensible architecture to make our life easier to support the current version and adding new features 🚀
Changelog v6.0
- [plugin] Multiple bug fixes and exception handling
- [plugin] Improvements in the double GetVariable scanner (@river-li)
- [plugin] Improvements in the UEFI global variables identification
- [plugin] Improvements in the SMI handlers identification
- [plugin] Hex-Rays based analysis for PEI services detection
- [plugin] Use of shifted pointers to improve pseudocode in PEI modules
- [plugin] PEI modules analysis support for Ampere ARM firmware
- [plugin] Update
guids.jsondatabase - [plugin] Flush all cached decompilations to automatically update decompiler output (@pagabuc)
- [loader] Integrate patfind plugin to identify more functions (@pagabuc)
- [loader] Add PEI and DXE a priori dependencies to
deps.json - Update dependencies
- Improve
FindIdaSdk.cmake - Moving to support of IDA SDK v8.3
Download
Copyright (C) 2020 Binarly