ElectricEye
ElectricEye is a set of Python scripts (affectionately called Auditors) that continuously monitor your AWS infrastructure looking for configurations related to confidentiality, integrity, and availability that do not align with AWS best practices. All findings from these scans will be sent to AWS Security Hub where you can perform basic correlation against other AWS and 3rd Party services that send findings to Security Hub. Security Hub also provides a centralized view from which account owners and other responsible parties can view and take action on findings.
ElectricEye runs on AWS Fargate, which is a serverless container orchestration service. On a schedule, Fargate will download all of the auditor scripts from an S3 bucket, run the checks and send results to Security Hub. All infrastructure will be deployed via CloudFormation or Terraform to help you apply this solution to many accounts and/or regions. All findings (passed or failed) will contain AWS documentation references in the Remediation.Recommendation section of the ASFF (and the Remediation section of the Security Hub UI) to further educate yourself and others on.
Personas who can make use of this tool are DevOps/DevSecOps engineers, SecOps analysts, Cloud Center-of-Excellence personnel, Site Reliability Engineers (SREs), Internal Audit and/or Compliance Analysts.
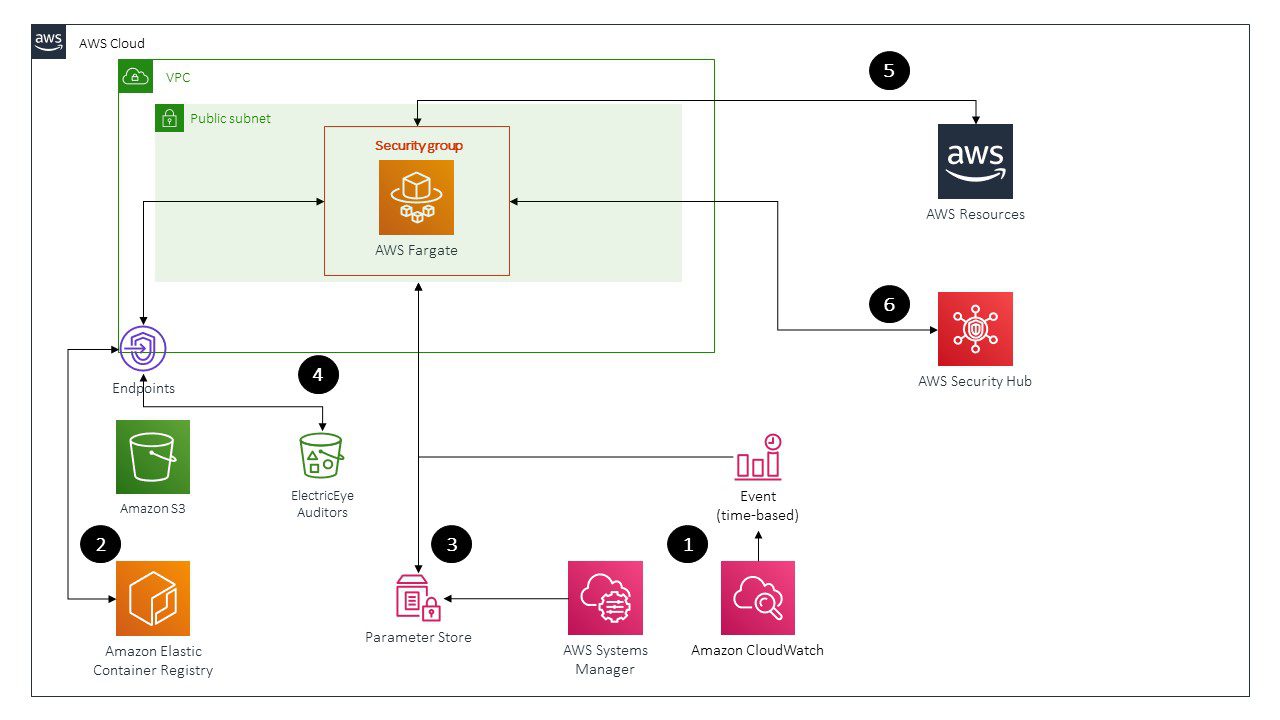
Solution Architecture
- A time-based CloudWatch Event starts up an ElectricEye task every 12 hours (or whatever time period you set)
- The ElectricEye Task will pull the Docker image from Elastic Container Registry (ECR) via a VPC Interface Endpoint (Note: The endpoint
com.amazonaws.region.ecr.dkralso needs the S3 Gateway Endpoint under the covers as Docker image layers are stored in S3, it serves a dual purpose to download the auditor scripts as well) - Systems Manager Parameter Store parameters are provided to the ElectricEye Task, these store values such as the S3 bucket containing the Auditor scripts and your Shodan.io API key (if used). These allow you to not have to hardcode these values in the environment variables of ECS or in the codebase
- The ElectricEye task will download all Auditor scripts from S3 via the VPC endpoint
- ElectricEye executes the scripts to scan your AWS infrastructure for both compliant and non-compliant configurations
- All findings are sent to Security Hub using the BatchImportFindings API, findings about compliant resources are automatically archived.
Refer to the Supported Services and Checks section for an up-to-date list of supported services and checks performed by the Auditors.
Install & Use
Copyright (C) 2020 jonrau1