electronegativity v1.10 releases: identify misconfigurations and security anti-patterns in Electron applications
Electronegativity
It is a tool to identify misconfigurations and security anti-patterns in Electron-based applications.
It leverages AST and DOM parsing to look for security-relevant configurations, as described in the “Electron Security Checklist – A Guide for Developers and Auditors” whitepaper.
Software developers and security auditors can use this tool to detect and mitigate potential weaknesses and implementation bugs when developing applications using Electron. A good understanding of Electron (in)security is still required when using Electronegativity, as some of the potential issues detected by the tool require manual investigation.
If you’re interested in Electron Security, have a look at our BlackHat 2017 research Electronegativity – A Study of Electron Security and keep an eye on the Doyensec’s blog.
Changelog v1.10
- New check for
setWindowOpenHandlerpreviously only included in ElectroNG, fixes #92 - Fix the
parserPluginspreviously throwing an error if Electronegativity was used as a library #98 - Update mocha dependency #100
- New support for i18n, with Spanish and French as locales.
Installation
$ npm install @doyensec/electronegativity -g
Usage
| Option | Description |
|---|---|
| -V | output the version number |
| -i, –input | input (directory, .js, .htm, .asar) |
| -o, –output | save the results to a file in csv or sarif format |
| -h, –help | output usage information |

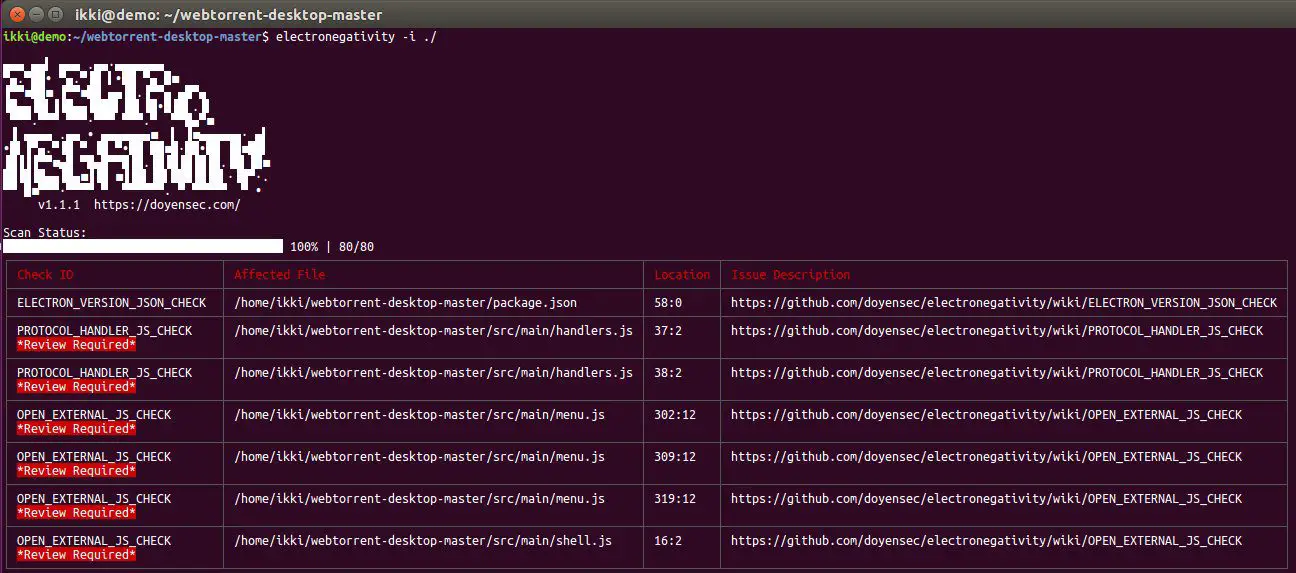
Using electronegativity to look for issues in a directory containing an Electron app:
$ electronegativity -i /path/to/electron/app
Using electronegativity to look for issues in an asar archive and saving the results in a csv file:
$ electronegativity -i /path/to/asar/archive -o result.csv
Note: if you’re running into the Fatal Error “JavaScript heap out of memory”, you can run node using
node --max-old-space-size=4096 electronegativity -i /path/to/asar/archive -o result.csv
Copyright (C) 2018
Source: https://github.com/doyensec/





