Ransom notes | Image: Netskope Threat Labs
Netskope Threat Labs has recently published an analysis of a new ransomware variant dubbed Elysium, linked to the notorious Ghost (also known as Cring or Crypt3r) ransomware family. This group has been active since 2021, targeting organizations in critical infrastructure, healthcare, and government sectors. The attackers typically gain initial access by exploiting known vulnerabilities in outdated applications.
Elysium, like other Ghost variants, employs a multi-stage attack chain. “Once inside the network, the attackers use several different tools and techniques to complete the attack,” the analysis states. These tools include Cobalt Strike for command and control, BadPotato and GodPotato for privilege escalation, Mimikatz for credential theft, SharpShares for network discovery, and WMI for lateral movement.
Once the attackers gain sufficient access, they deploy the Elysium ransomware payload. This payload is written in .NET and utilizes obfuscation techniques like string obfuscation to hinder analysis.
Elysium takes steps to disrupt recovery efforts. It terminates services related to databases, backups, and security software, specifically targeting services with names including “sql,” “oracle,” “veeam,” “backup,” “acronis,” “sophos,” “endpoint,” and “exchange.” It also attempts to stop Hyper-V virtual machines via PowerShell.
Before encrypting files, Elysium disables system backups, deletes shadow copies, and modifies the boot status policy to impede system recovery. The ransomware then encrypts files using AES-256 in CFB mode, encrypts the AES key with RSA, and appends it to the encrypted file. Finally, it adds the “.HvTovz” extension to the encrypted file names.
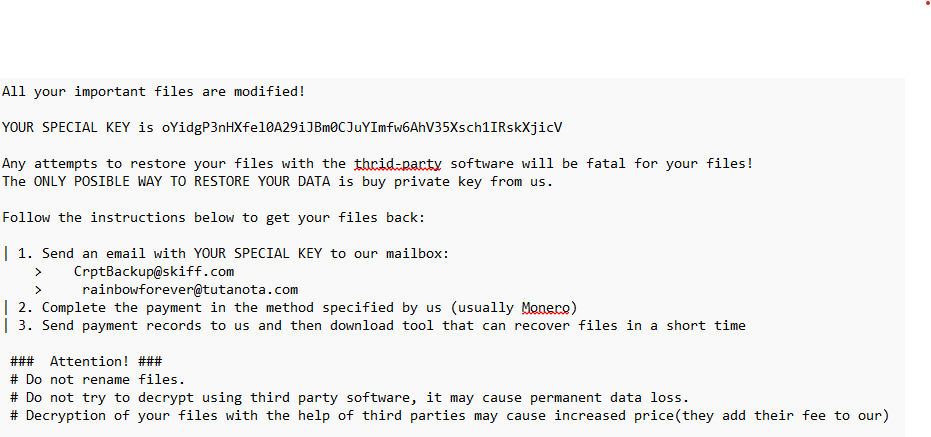
Elysium drops a ransom note named “HvTovz-README.txt” in each Desktop folder, demanding payment in Monero for the decryption key. The ransom note warns against using third-party decryption tools, threatening potential data loss and increased costs.
