EMERALDWHALE Operation Exposes Over 15,000 Cloud Credentials in Widespread Git Exploit
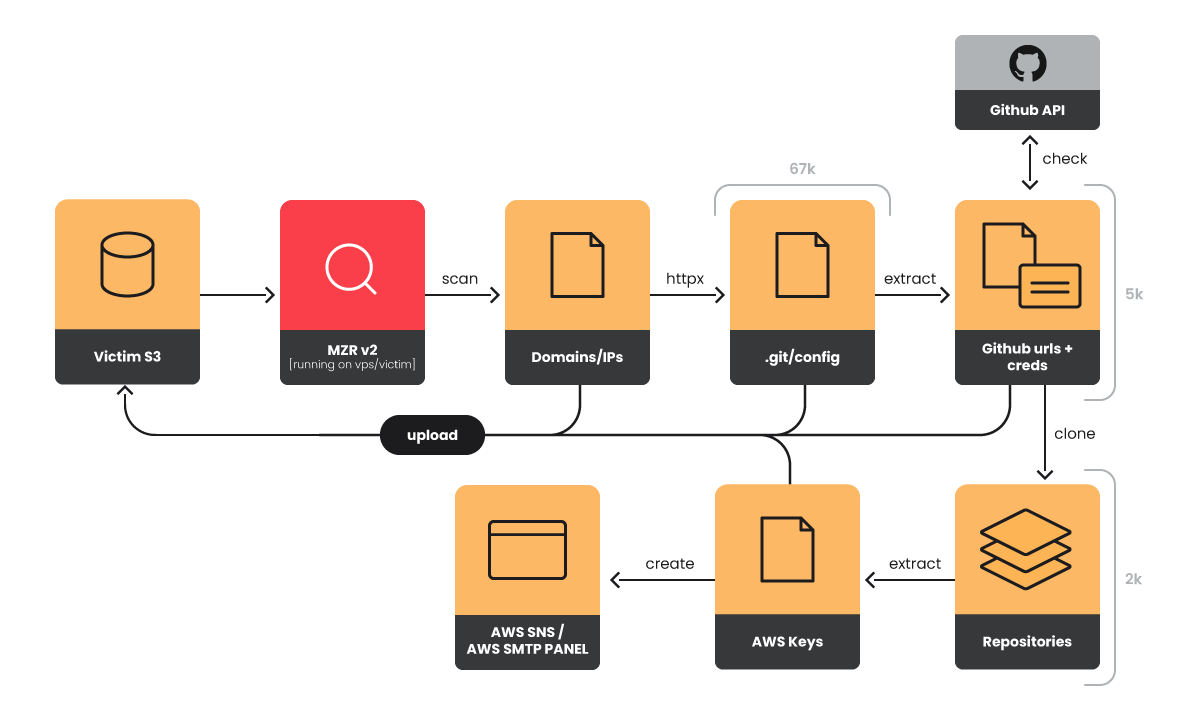
The Sysdig Threat Research Team (TRT) has uncovered a global operation, EMERALDWHALE, that has led to the theft of over 15,000 cloud credentials by exploiting exposed Git configuration files. The report highlights an alarming trend in misconfigured web servers that leak credentials, impacting thousands of private repositories and potentially costing victims hundreds of dollars per compromised account.
EMERALDWHALE’s approach involved targeting the .git/config files of exposed repositories across platforms like GitHub, GitLab, and BitBucket. Sysdig TRT noted, “EMERALDWHALE targeted large swaths of the Internet,” using open-source scanning tools like httpx to identify vulnerable configurations en masse. Once detected, the attackers cloned these repositories and extracted sensitive tokens, including cloud credentials from Git configuration files. The team discovered, “credentials for over 10,000 private repositories were collected during the operation,” with the stolen data stored in an S3 bucket from a prior victim.
Git configuration files offer attackers a wealth of data, as they contain critical authentication tokens, branch information, and complete commit histories. According to Sysdig, “If the .git directory is exposed, attackers can retrieve valuable data about the repository’s history, structure, and sensitive project information.” Insecurely configured web servers allow public access to this directory, exposing projects to potential data leaks, identity theft.
The Sysdig report identified two tools, MZR V2 (MIZARU) and Seyzo-v2, as instrumental in the operation. MZR V2, a collection of Python and shell scripts, automates the scanning of IPs for accessible Git config files, while Seyzo-v2 builds on this with enhanced functionality, using tools like git-dumper to capture repository data. These tools, available on underground marketplaces, allow attackers to “create users for SPAM and phishing campaigns,” adding further financial incentives.
EMERALDWHALE also targeted Laravel .env files, which are notorious for containing cloud and database credentials. Using a tool called Multigrabber, the attackers scanned domains for exposed .env files to capture credentials for use in spam and phishing operations. This tool, found in forums and Telegram groups, has continued to evolve, with the latest version enabling attackers to target even more potential victims.
The operation has highlighted the vulnerabilities associated with poorly secured Git configurations and underscores the importance of robust secret management practices. Sysdig TRT emphasizes that “secret management alone is not enough to secure an environment,” pointing out the vast number of ways credentials can inadvertently leak.
As attackers find new ways to exploit misconfigurations, the cybersecurity community must prioritize proactive security measures, including rigorous server configuration checks, to prevent similar large-scale credential thefts.





