enumdb v2.2 released: MySQL and MSSQL brute force and post exploitation tool
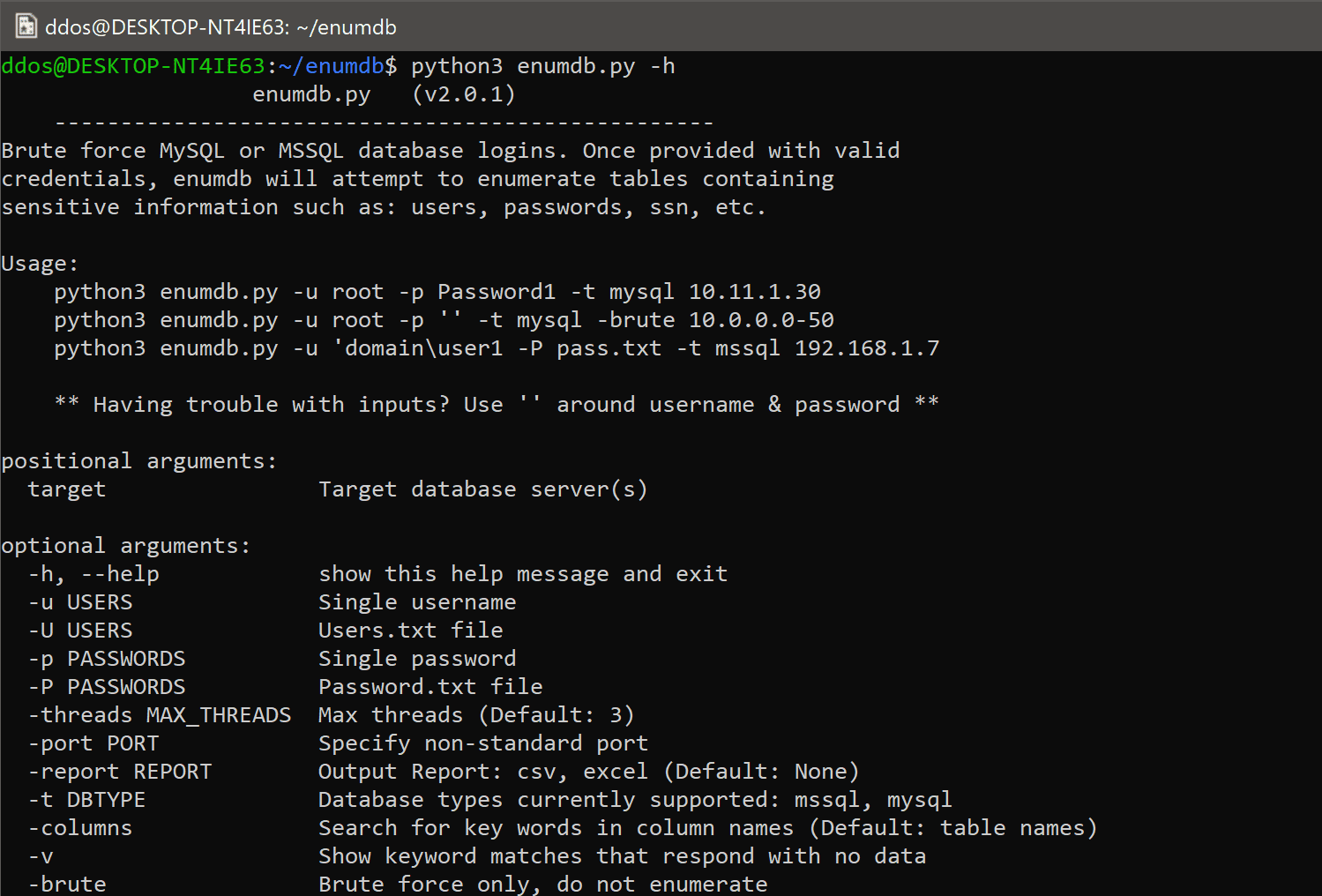
Enumdb is a brute force and post-exploitation tool for MySQL and MSSQL databases. When provided a list of usernames and/or passwords, it will cycle through each targeted host looking for valid credentials. By default, enumdb will use newly discovered credentials to search for sensitive information in the host’s databases via keyword searches on the table or column names. This information can then be extracted and reported to a .csv or .xlsx output file. See the Usage and All Options sections for more detailed usage and examples.
The latest version, enumdb v2.0, has been adapted for larger environments:
- Keyword searches can now be conducted on table or column names to identify sensitive information. These terms can be customized at the top of enumdb.py.
- Threading has been added to expedite brute-forcing and enumeration on larger networks.
- Enumdb no longer generates reports by default. Reporting (csv/xlsx) must be defined in the command line arguments.
- When extracting data for reports, users can now define a limit on the number of rows selected. The default value of 100, can be modified at the top of enumdb.py.
- Enumdb’s output formatting has been modified to provide more concise feedback when enumerating large amounts of data.
Enumdb is written in python3, use the setup.sh script to ensure all required libraries are installed.
Getting Started
In the Linux terminal run:
-
git clone https://github.com/m8r0wn/enumdb.git
-
sudo chmod +x enumdb/setup.sh
-
sudo ./enumdb/setup.sh
Usage
- Connect to a MySQL database and enumerate tables writing output to xlsx:
bash python3 enumdb.py -u root -p '' -t mysql 10.11.1.30 - Connect to an MSSQL database using a domain username and enumerate tables writing output to xlsx:
python3 enumdb.py -u 'domain\\user' -p Winter2018 -t mysql 10.11.1.30 - Connect to MySQL database and enumerate tables writing output to csv:
python3 enumdb.py -u root -p SecretPass! -t mysql -csv 10.0.0.1 - Brute force MSSQL sa account login. Once valid credentials are found, enumerate data writing output to xlsx:
python3 enumdb.py -u sa -P passwords.txt -t mssql 192.168.10.10 - Brute force MSSQL sa account login without enumerating data or logging output:
python3 enumdb.py -u sa -P passwords.txt -t mssql -brute 192.168.10.10
All Options
Copyright (C) 2018 m8r0wn
Source: https://github.com/m8r0wn




