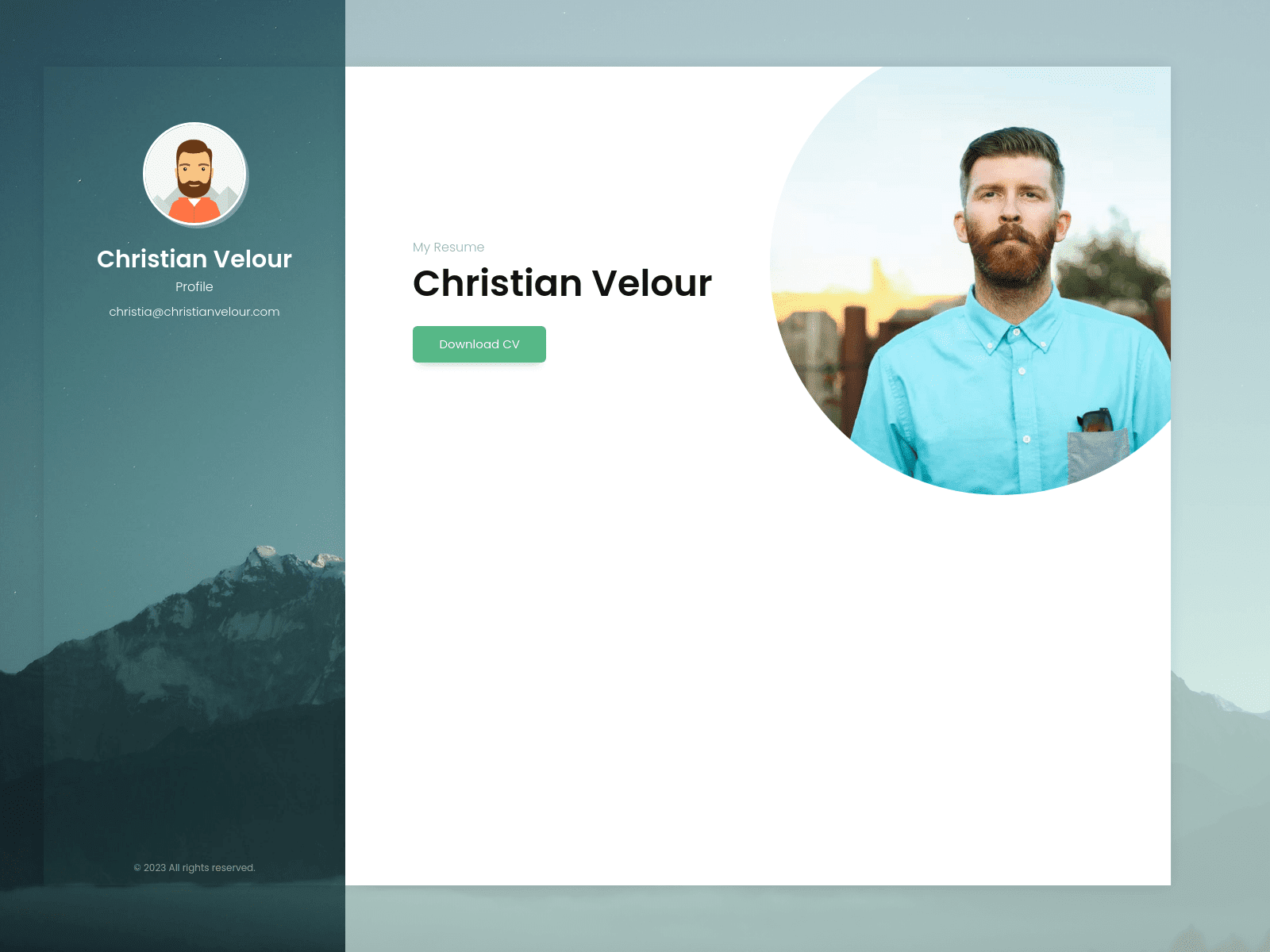
Fake resume download site
eSentire’s Threat Response Unit (TRU) has unveiled a persistent and sophisticated cyber campaign employing the notorious more_eggs malware, primarily targeting recruiters in the industrial services sector. This campaign exploits the trust inherent in job applications, luring victims with fake resumes hosted on malicious websites.
The attackers, believed to be the Golden Chickens group (aka Venom Spider), have refined their tactics since earlier campaigns in 2022, disguising themselves as both recruiters and job applicants to maximize their reach during peak hiring seasons.
The infection chain begins with a seemingly innocuous link to a resume, which, when clicked, triggers a series of obfuscated commands. These commands ultimately lead to the download and execution of a malicious DLL (55609.dll), establishing persistence on the victim’s system.
The 55609.dll file was highly obfuscated, containing multiple anti-debug and anti-sandbox checks. The payload was encrypted, requiring a key generated through an iterative process involving string comparisons and hash matching.
Once decrypted, the DLL set up persistence in the host’s registry and dropped additional components, including msxsl.exe and two text files containing JavaScript code. These files were critical for establishing command and control (C2) connections and executing further malicious actions.
The malware then deploys a multi-stage payload, utilizing anti-debug and anti-sandbox techniques to evade detection. This payload exfiltrates sensitive data, including credentials for corporate bank accounts, email accounts, and IT administrator accounts, to a command and control (C2) server.
The continued activity of the more_eggs malware emphasizes the importance of cybersecurity awareness and the implementation of robust security measures.