In an article published yesterday, ESET stated that they found three applications that carry Trojan horses on the CNET Download site (163th Alexa ranking). This is the world’s largest Internet download directory site. Founded in 1996, it has more than 100,000 free-to-use software (including MAC computers, Windows computers, and other mobile devices). In addition, it also offers free downloads of music, games, and videos.
The reason why ESET will do such a survey comes from a forum post published by a Monroe coin investor named Crawsh.
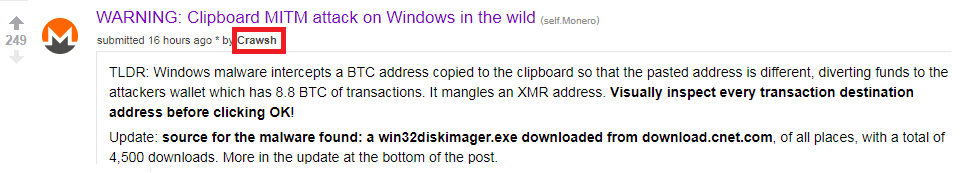
When Crawsh tried to copy and paste his Monroe wallet address to another location, he was prompted “invalid address.” This caused Crawsh’s attention, he immediately began to check and think that the biggest possibility is due to malicious software.
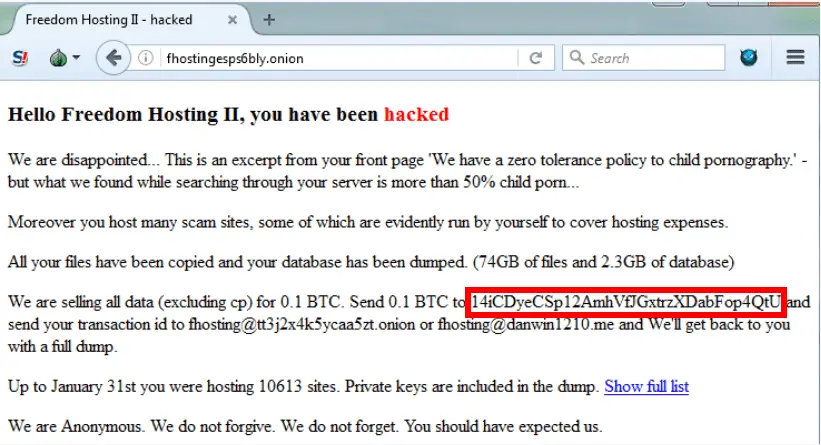
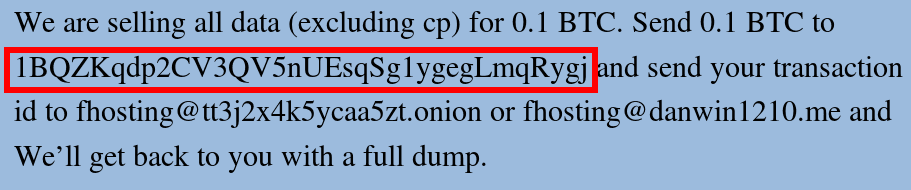
It turns out that he is right. Crawsh copied the pasted wallet address and was intercepted by the malware when it entered the clipboard and was replaced by the attacker’s hard-coded Bitcoin wallet address. Fortunately for Crawsh, because the malware seems to be targeting Bitcoin only and does not apply to the Monroe trades that Crawsh is trying to do.
Crawsh’s post caught the attention of ESET security researchers and they decided to see if anyone on the network had encountered the same thing. They used the hard-coded Bitcoin wallet address of the attacker to search Google, and some other victims were quickly discovered. In a blog post, the author’s Bitcoin wallet address was replaced with the hard-coded Bitcoin wallet address of the attacker Crawsh encountered, indicating that the author of this blog post also became a victim of Bitcoin theft software.
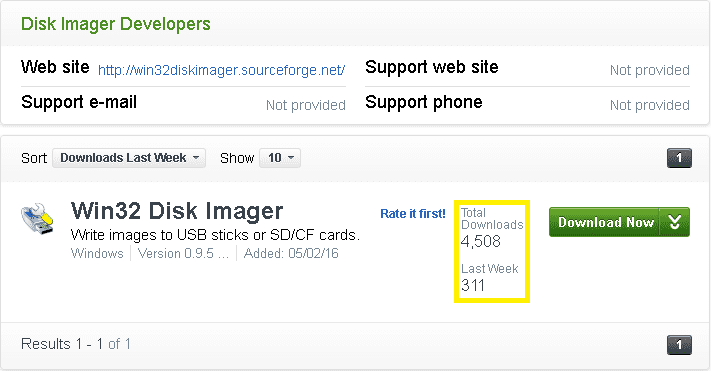
On the other hand, ESET discovered that the source of Crawsh infection was the Win32 Disk Imager application downloaded from the CNET Download site. Since May 2, 2016, the application has been hosted on this site, with a total of more than 4,500 downloads and only 311 downloads last week. Unsurprisingly, ESET detected Trojans in this application, which is a variant of the MSIL/ TrojanDropper.Agent.DQJ Trojan.
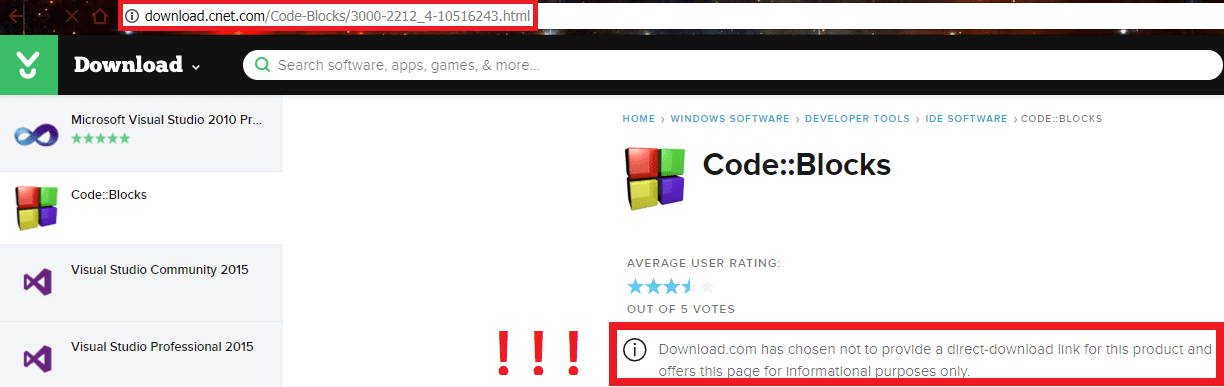
At the end of the survey, ESET discovered that the Win32 Disk Imager is not the only Trojanization application hosted on CNET Download. The other two Trojanization applications from the same author were also found. One of them is CodeBlocks. The carried Trojan virus is detected as MSIL/CLipBanker.DF and can replace the Bitcoin wallet address in the clipboard.
The other is MinGW-w64, which can be downloaded at the beginning of the ESET survey. It contains several malicious payloads, including Bitcoin stealers and Trojans.
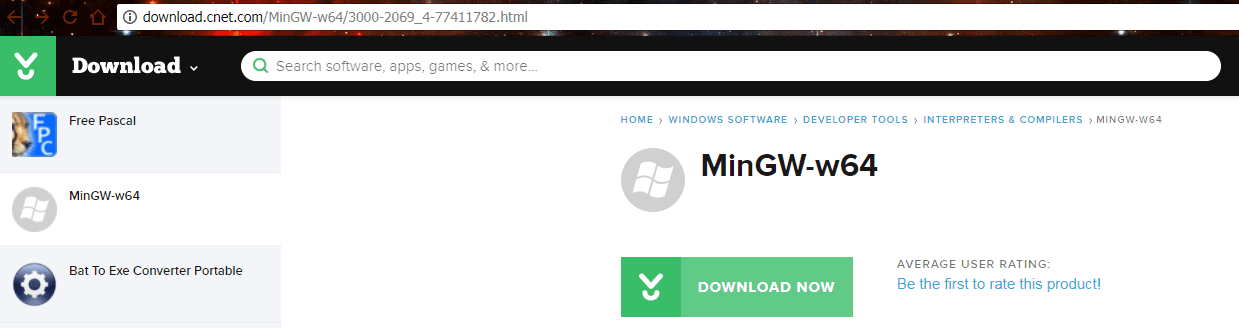
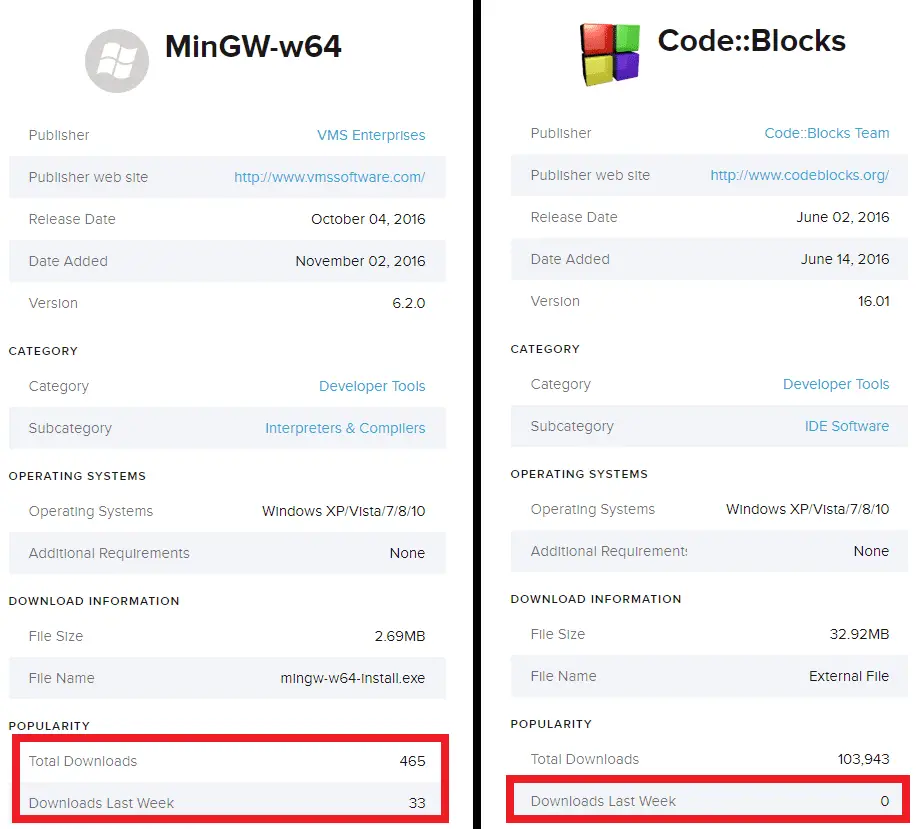
The download status of these two applications on the CNET Download site is as follows, where CodeBlock recently downloaded 0 because it has been deleted by CNET. According to ESET telemetry data, it may be deleted around March 2017.

ESET has now notified these discoveries to CNET and these applications have been removed. In addition, if you suspect that you are also infected with this Trojan virus, then you need to manually perform the following steps:
- Delete the downloaded installers called win32diskimager.exe (SHA1: 0B1F49656DC5E4097441B04731DDDD02D4617566) resp. codeblocks.exe (SHA1: 7242AE29D2B5678C1429F57176DDEBA2679EF6EB) resp. mingw-w64-install.exe (SHA1: 590D0B13B6C8A7E39558D45DFEC4BDE3BBF24918) from your Download folder location
- Remove exe in the %appdata%\dibifu_8\ folder (SHA1: E0BB415E858C379A859B8454BC9BA2370E239266)
- Remove y3_temp008.exe from %temp%\ folder (SHA1: 3AF17CDEBFE52B7064A0D8337CAE91ABE9B7E4E3, resp. C758F832935A30A865274AA683957B8CBC65DFDE )
- Delete ScdBcd registry value from the key HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
Source,Image: welivesecurity