According to securityaffairs on March 14, the security company ESET released an analysis report that the OceanLotus APT organization (also known as APT32 and APT-c-00) used a new backdoor in its recent attacks to get remote access and full control over the infected system.
The OceanLotus organization has been active since 2013. According to experts, the organization is a state-funded hacking organization related to Vietnam, most of which are located in Vietnam, the Philippines, Laos, and Cambodia. According to the survey, OceanLotus is also targeted at foreign governments, dissidents, and journalists, in addition to organizations targeting multiple industries.
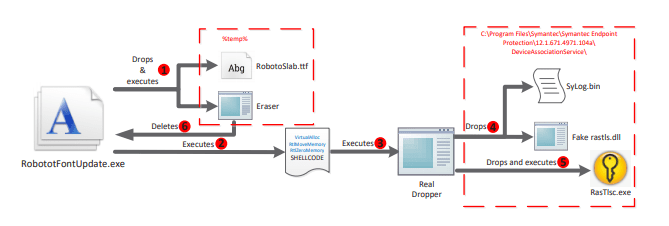
At present, the OceanLotus attack is conducted in two stages. The first stage hackers use a dropper that passes spear-phishing information to obtain the initial location of the target system. The second stage is that its malicious code prepares for deploying the back door.

Dropper execution flow
At present, OceanLotus will constantly update the toolset during its attack activities, which shows the organization’s intention to keep hidden by selecting targets. In addition, OceanLotus also restricts the distribution of its malware and uses multiple different servers to avoid attracting attention to a single domain name or IP address.
Read the “OceanLotus Old techniques, new backdoor ” report here.
Source: Security Affairs