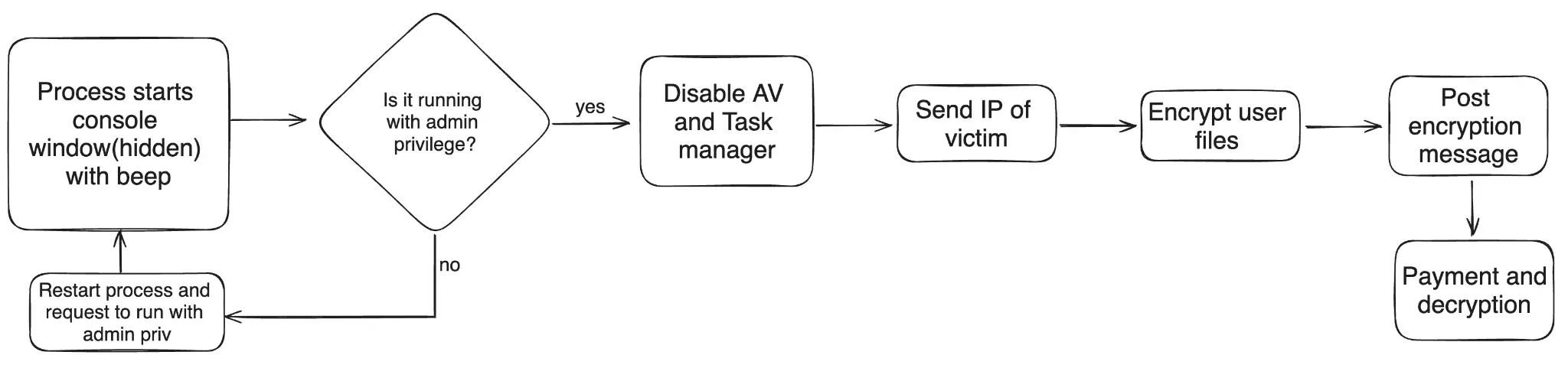
Evil Ant execution flow
Cybersecurity researchers at Netskope Threat Labs have uncovered a new ransomware strain dubbed “Evil Ant.” While this ransomware can successfully encrypt a victim’s files, serious flaws in its design offer hope for recovery, even without paying the ransom.
The Evil Ant ransomware, written in Python and compiled using PyInstaller, targets a wide array of files in a victim’s folders and any external drives. Researchers emphasize the danger of rebooting, shutting down, or interrupting the ransomware process, as this will likely render the files unrecoverable.

A major blunder in Evil Ant’s code is the hardcoded decryption key–it exists within the malware itself. This means that, at present, victims of Evil Ant ransomware may not need to pay the ransom, but may instead recover their files with the assistance of security specialists.
“Even though the Evil Ant ransomware can successfully encrypt files, we believe that this ransomware strain is still in its development stage,” states Netskope researcher.
Evil Ant initiates its attack by concealing its process console and, in some variants, emitting a beeping sound to signal activation. This is followed by a check for administrative privileges. If the malware does not have the required permissions, it prompts the user to grant elevated access. Once admin rights are obtained, Evil Ant proceeds to disable critical security features such as Windows Defender and Task Manager, ensuring its operations proceed uninterrupted.
The ransomware then collects the victim’s public IP address, likely to tailor its attack or for future targeting purposes. Subsequently, it encrypts all files within specific user directories and any connected external drives, focusing particularly on files with a .bak extension—commonly associated with backups—making recovery more challenging.
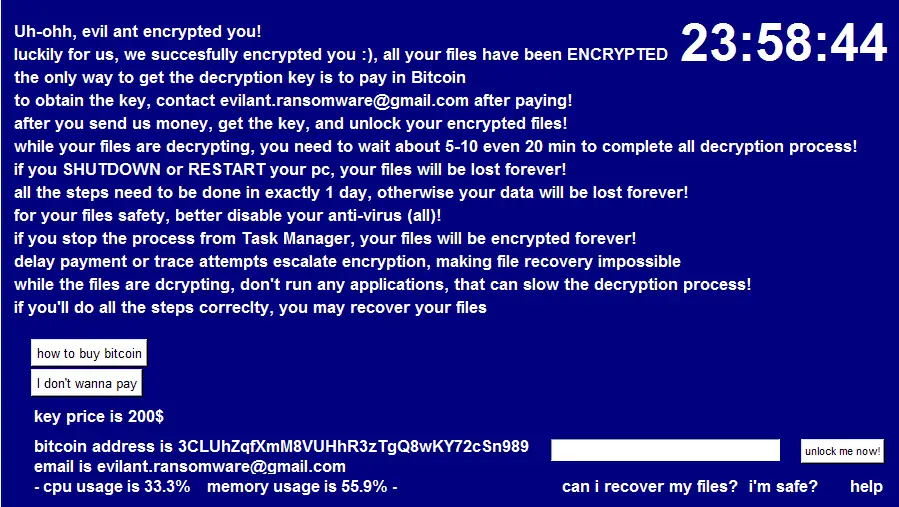
Utilizing the Fernet symmetric cryptography library, Evil Ant encrypts the targeted files and displays a ransom note through a GUI built with Python’s tkinter package. The note demands payment in Bitcoin and includes a timer, adding pressure on the victim to comply swiftly. Notably, the ransomware makes an egregious error: the decryption key is hardcoded into the malware itself, in plaintext. This oversight allows victims to decrypt their files without making any payment.
The ransomware also displays several other aggressive behaviors:
- Disables Anti-Virus: Evil Ant attempts to disable Windows Defender and Task Manager.
- Demands Bitcoin Payment: The ransom note provides instructions for purchasing Bitcoin and a deadline, adding pressure to the victim.
- IP Address Collection: Some variants gather the victim’s IP address and send it to the attacker via Telegram.
Despite its aggressive tactics, researchers believe Evil Ant is still under development. The hardcoded decryption key is a significant oversight, and the ransomware displays other quirks that reveal its early stage.