evil-ssdp: Spoof SSDP replies to phish for NTLM hashes on a network
evil-ssdp
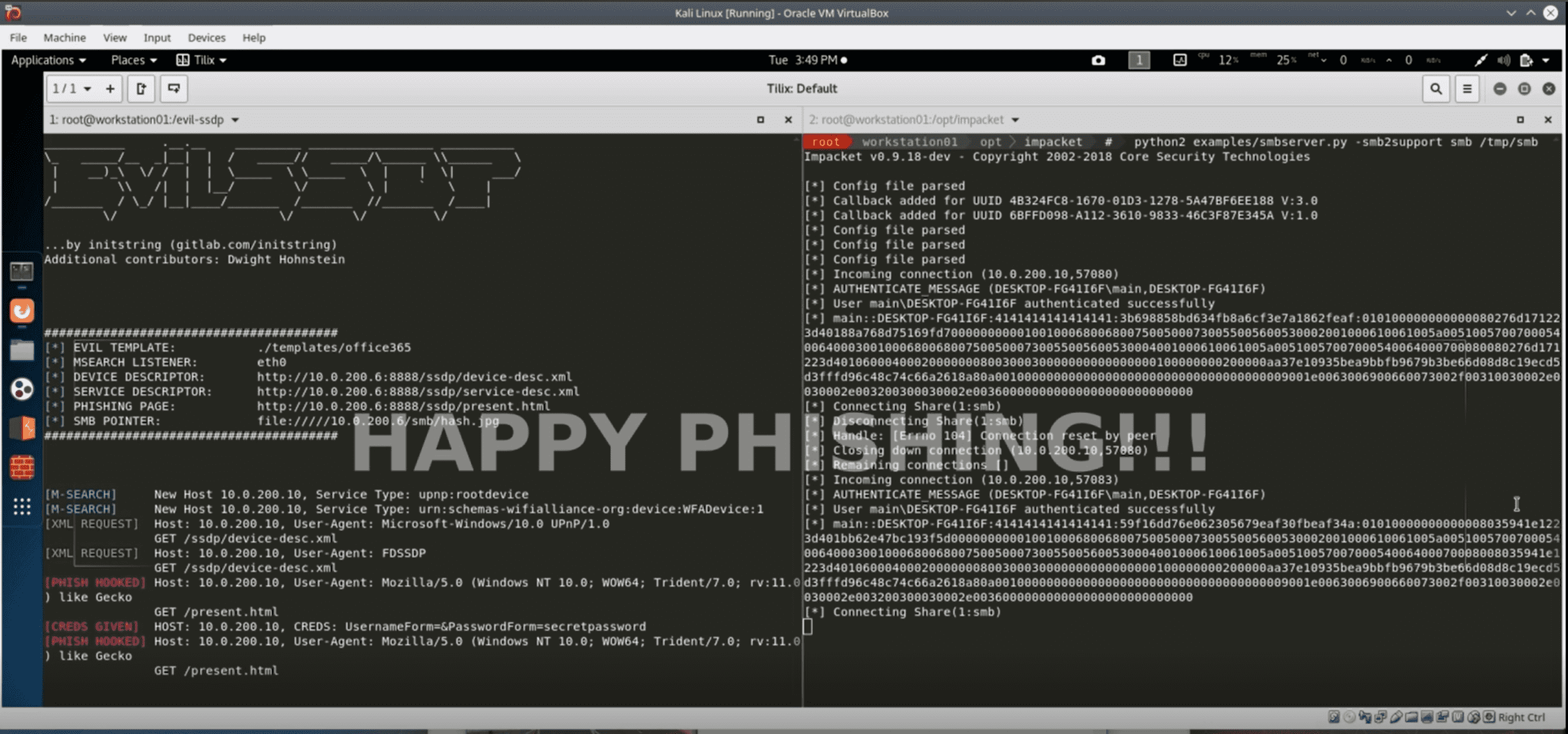
This tool responds to SSDP multicast discovery requests, posing as a generic UPNP device. Your spoofed device will magically appear in Windows Explorer on machines in your local network. Users who are tempted to open the device are shown a configurable phishing page. This page can load a hidden image over SMB, allowing you to capture or relay the NetNTLM challenge/response.
Templates are also provided to capture clear-text credentials via basic authentication and logon forms, and creating your own custom templates is quick and easy.
This requires no existing credentials to execute and works even on networks that have protected against Responder attacks by disabling NETBIOS and LLMNR. Any Operating System or application leveraging SSDP/UPNP can be targeted, but most of the current weaponization has been aimed at Windows 10.
As a bonus, this tool can also detect and exploit potential zero-day vulnerabilities in the XML parsing engines of applications using SSDP/UPNP. If a vulnerable device is found, it will alert you in the UI and then mount your SMB share or exfiltrate data with NO USER INTERACTION REQUIRED via an XML External Entity (XXE) attack.

The following templates come with the tool. If you have good design skills, please contribute one of your own!
- office365: Will show up in Windows Explorer as “Office365 Backups”. Phishing page looking like Office365 logon will POST credentials back to you. These will be flagged in the UI and logged in the log file. Recommend to run with ‘-u https://www.office.com’ to redirect users to the legit site after stealing their credentials. Developer: pentestgeek.
- scanner: Will show up in Windows Explorer as a scanner with the name “Corporate Scanner [3 NEW SCANS WAITING]”. Double-clicking will bring to a generic looking logon page. This template would do well with customization for your particular target. Template mostly copied from this template.
- Microsoft-azure: Will appear in Windows Explorer as “Microsoft Azure Storage”. Landing page is the Windows Live login page when cookies are disabled. Recommend to use with the -u option to redirect users to real login page. Developer: Dwight Hohnstein.
- bitcoin: Will show up in Windows Explorer as “Bitcoin Wallet”. Phishing page is just a random set of Bitcoin private/public/address info. There are no actual funds in these accounts.
- password-vault: Will show up in Windows Explorer as “IT Password Vault”. Phishing page contains a short list of fake passwords/ssh keys / etc.
- xxe-smb: Will not likely show up in Windows Explorer. Used for finding zero-day vulnerabilities in XML parsers. Will trigger an “XXE – VULN” alert in the UI for hits and will attempt to force clients to authenticate with the SMB server, with 0 interaction.
- xxe-exfil: Another example of searching for XXE vulnerabilities, but this time attempting to exfiltrate a test file from a Windows host. Of course, you can customize this to look for whatever specific file you are after, Windows or Linux. In the vulnerable applications, I’ve discovered, exfiltration works only on a file with no whitespace or line breaks. This is due to how it is injected into the URL of a GET request. If you get this working on multi-line files, PLEASE let me know how you did it.
Creating your own templates is easy. Simply copy the folder of an existing template and edit the following files:
- device.xml: Here is where you will define what the device looks like inside Windows Explorer.
- present.html: This is the phishing page displayed when a target opens the evil device. Craft anything you like here. Note that Python’s string template will parse this, so you will need to use $$ in place of $ anywhere to escape the template engine.
- service.xml: Not yet implemented. Maybe needed for more complex UPNP spoofing in the future.
Usage
Copyright (c) 2018 InitString
Source: https://gitlab.com/initstring/