evilgophish
Combination of evilginx2 and GoPhish.

Why?
As a penetration tester or red teamer, you may have heard of evilginx2 as a proxy man-in-the-middle framework capable of bypassing two-factor/multi-factor authentication. This is enticing to us, to say the least, but when trying to use it for social engineering engagements, there are some issues off the bat. I will highlight the two main problems that have been addressed with this project, although some other bugs have been fixed in this version which I will highlight later.
- Lack of tracking – evilginx2 does not provide unique tracking statistics per victim (e.g. opened email, clicked the link, etc.), this is problematic for clients who want/need/pay for these statistics when signing up for a social engineering engagement.
- Session overwriting with NAT and proxying – evilginx2 bases a lot of logic off of a remote IP address and will whitelist an IP for 10 minutes after the victim triggers a lure path. evilginx2 will then skip creating a new session for the IP address if it triggers the lure path again (if still in the 10-minute window). This presents issues for us if our victims are behind a firewall all sharing the same public IP address, as the same session within evilginx2 will continue to overwrite with multiple victim’s data, leading to missed and lost data. This also presents an issue for our proxy setup, since localhost is the only IP address requesting evilginx2.
Background
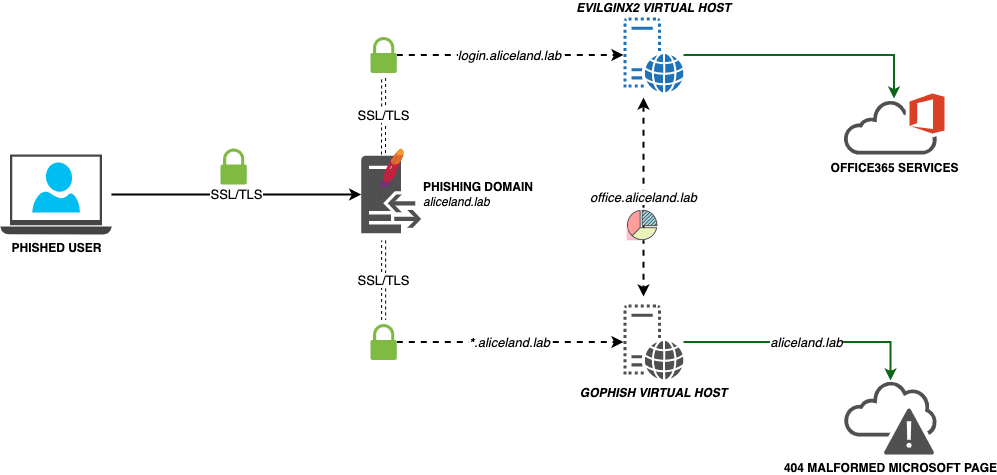
This project is based on this blog and I encourage you to read it before getting started. In this setup, GoPhish is used to send emails, track opened emails, and provide a dashboard for evilginx2 campaign statistics, but it is not used for any landing pages. To provide tracking between the two, the function responsible for providing campaign results inside GoPhish has been modified to instead get clicked link event details and submitted data event details from logs related to evilginx2. Your phishing links sent from GoPhish will point to an evilginx2 lure path and evilginx2 will be used for landing pages. This provides the ability to still bypass 2FA/MFA with evilginx2, without losing those precious stats. The operator will also be informed of a submitted data event in real time. This should ensure the operator won’t run out of time to use captured cookies, or at least be informed as soon as possible. The operator will still need to bounce over to the evilginx2 terminal to fetch the full JSON string of captured tokens/cookies.
Infrastructure Layout
- evilginx2 will listen locally on port 8443
- GoPhish will listen locally on port8080
- Apache2 will listen on port 443 externally and proxy to either local GoPhish/evilginx2 depending on the subdomain name requested. Apache2 access log file is created for both GoPhish/evilginx2 servers
- Requests will be filtered at Apache2 layer based on redirect rules and IP blacklist configuration
- 404 functionality for unauthorized requests is still baked into GoPhish if a request hits the GoPhish server
- Redirect functionality for unauthorized requests is still baked into evilginx2 if a request hits the evilginx2 server
- Requests will be filtered at Apache2 layer based on redirect rules and IP blacklist configuration
While Multi-factor authentication (MFA) and two-factor authentication (2fa) are effective security measures, bad actors can exploit vulnerabilities in these methods through sophisticated cyber hack techniques like the GoPhish technique described here. Passwordless authentication model is known to be effective in the elimination of passwords that are much easier to exploit. Nonetheless, continuous monitoring and user education should be a core part of any cyber security strategy aiming at eliminating phishing threats.
Changelog 07/08/2023
Upgraded evilginx2 to evilginx3
Install & Use
Copyright (C) 2022