EvilOSX v7.2.0 releases: remote administration tool (RAT) for macOS/OS X

EvilOSX
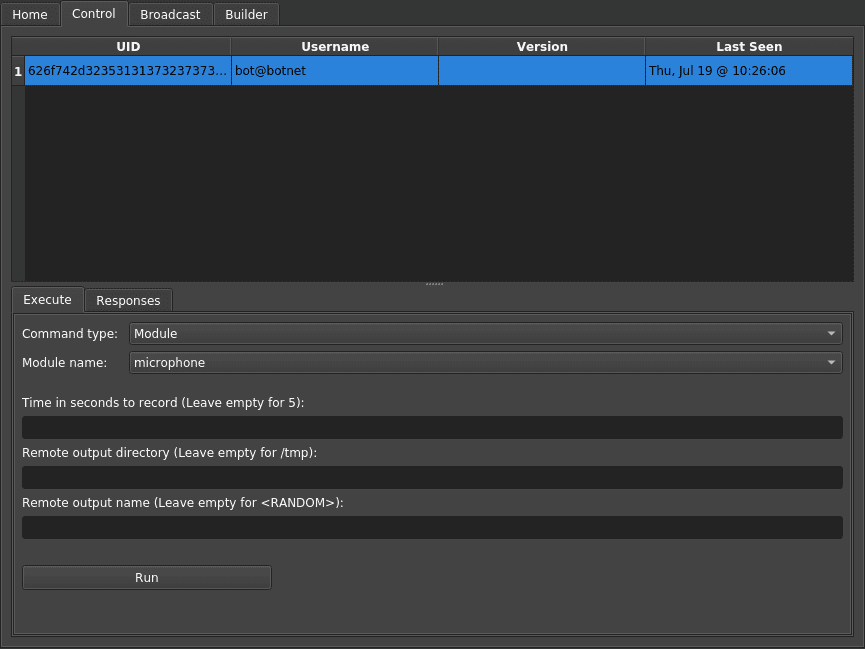
A pure python, post-exploitation, remote administration tool (RAT) for macOS/OS X.
Feature
- Emulate a terminal instance
- Simple extendable module system
- No bot dependencies (pure python)
- Undetected by anti-virus (OpenSSL AES-256 encrypted payloads)
- Persistent
- GUI and CLI support
- Retrieve Chrome passwords
- Retrieve iCloud tokens and contacts
- Retrieve/monitor the clipboard
- Retrieve browser history (Chrome and Safari)
- Phish for iCloud passwords via iTunes
- iTunes (iOS) backup enumeration
- Record the microphone
- Take a desktop screenshot or picture using the webcam
- Attempt to get root via local privilege escalation
Design Notes
- The server uses the MVC pattern
- Infecting a machine is split up into three parts:
- A launcher is run on the target machine whose only goal is to run the stager
- The stager asks the server for a loader which handles how a payload will be loaded
- The loader is given a uniquely encrypted payload and then sent back to the stager
- The server hides it’s communications by sending messages hidden in HTTP 404 error pages (from BlackHat’s “Hiding In Plain Sight”)
- Command requests are retrieved from the server via a GET request
- Command responses are sent to the server via a POST request
- Modules take advantage of Python’s dynamic nature, they are simply sent over the network compressed with zlib, along with any configuration options
- Since the bot only communicates with the server and never the other way around, the server has no way of knowing when a bot goes offline
How To Use
Copyright (C) 2018 Marten4n6
Source: https://github.com/Marten4n6/





