Image: Peter Gabaldon
Security researcher Peter Gabaldon published the technical details and proof-of-concept exploit code for two high-severity vulnerabilities, CVE-2024-7479 and CVE-2024-7481, which have been found in TeamViewer, the popular remote access tool. These flaws expose Windows users to local privilege escalation attacks, allowing attackers to gain SYSTEM-level access and execute arbitrary code by exploiting the improper verification of cryptographic signatures during driver installation.
Both vulnerabilities (CVSS score: 8.8) stem from the same underlying issue—a lack of authentication and insufficient cryptographic signature verification when installing drivers via the TeamViewer_service.exe component. This service, running by default on port 5939/tcp, is vulnerable to manipulation, allowing attackers to escalate privileges and take control of critical system functions.

Gabaldon highlights in his analysis: “TeamViewer was not verifying the signature of the driver being installed. Thus, a privilege escalation from USER to KERNEL was possible thanks to TeamViewer.” The flaws exist within the installation process of both VPN and Printer drivers, leading to the discovery of two distinct but related vulnerabilities.
The first vulnerability, CVE-2024-7479, occurs during the installation of a VPN driver. By spoofing a legitimate TeamViewer client and exploiting the lack of proper signature verification, an attacker can request the installation of a malicious driver, effectively bypassing TeamViewer’s authentication mechanisms. Gabaldon describes the attack methodology: “We will spoof a TeamViewer client and ask for a VPN Driver installation but indicating another INF… I reutilized the same original INF of TeamViewer but in another (non-privileged) path, renaming the ‘bad’ driver to teamviewervpn.sys”.
CVE-2024-7481 is similar to its counterpart but involves the installation of a printer driver instead of a VPN driver. Gabaldon explains that TeamViewer made “the same error two times,” with both IPC messages containing vulnerabilities that allow arbitrary driver loading. “The message is thrown when clicking Install VPN Driver or Printer Driver… but the result is the same—an arbitrary driver can be loaded.”
Gabaldon has published a proof-of-concept (PoC) exploit on GitHub, allowing researchers and security professionals to better understand and test CVE-2024-7479 & CVE-2024-7481. His detailed explanation includes guidance on how attackers can “bring their own vulnerable driver” (BYOD) to escalate privileges from user mode to kernel mode, allowing complete system compromise.
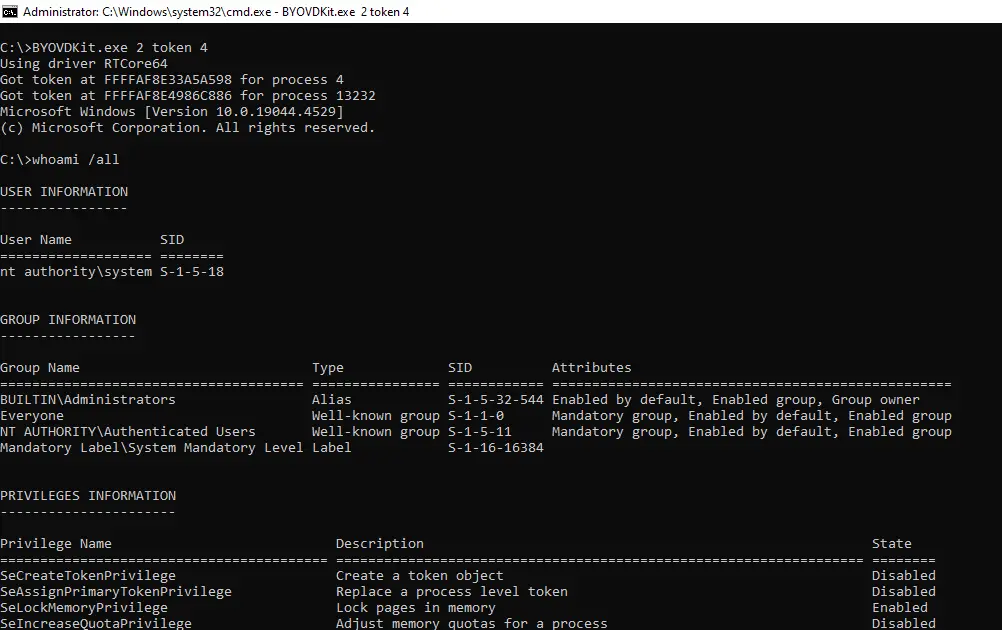
In a particularly striking revelation, the exploit bypasses TeamViewer’s graphical user interface protections. “This bypasses also TeamViewer’s option ‘Changes require administrative rights on this computer.’ The check is only effective via the GUI, but it is possible to connect to the socket and perform the arbitrary driver load.
While TeamViewer has addressed these vulnerabilities in version 15.58.4 for Windows, users must update their software immediately. Systems running outdated versions of TeamViewer are vulnerable to these privilege escalation attacks.
Gabaldon’s analysis serves as a stark reminder of the dangers posed by inadequate cryptographic validation, particularly in software with extensive access to system resources. “One of the best approaches is to use the well-known technique BYOD, Bring Your Own Vulnerable Driver to load a valid signed driver into Windows Kernel and then exploit it in order to perform privileged actions from user level.”
Related Posts:
- TeamViewer Urges Users to Patch Privilege Escalation Flaws (CVE-2024-7479 and CVE-2024-7481)
- TeamViewer Confirms Cyberattack by Notorious APT Group
- CVE-2024-0819: TeamViewer’s Security Flaw Risks Password Safety