Second attack scenario | Image: paloaltonetworks
In the ever-evolving realm of cloud computing, a critical risk has surfaced within Google Workspace’s Domain-Wide Delegation feature, as revealed by Unit 42 researchers at Palo Alto Networks. This discovery sheds light on the potential for malicious exploitation of Google Workspace domain data from the Google Cloud Platform (GCP), highlighting the intricate and often overlooked vulnerabilities in cloud-based services.
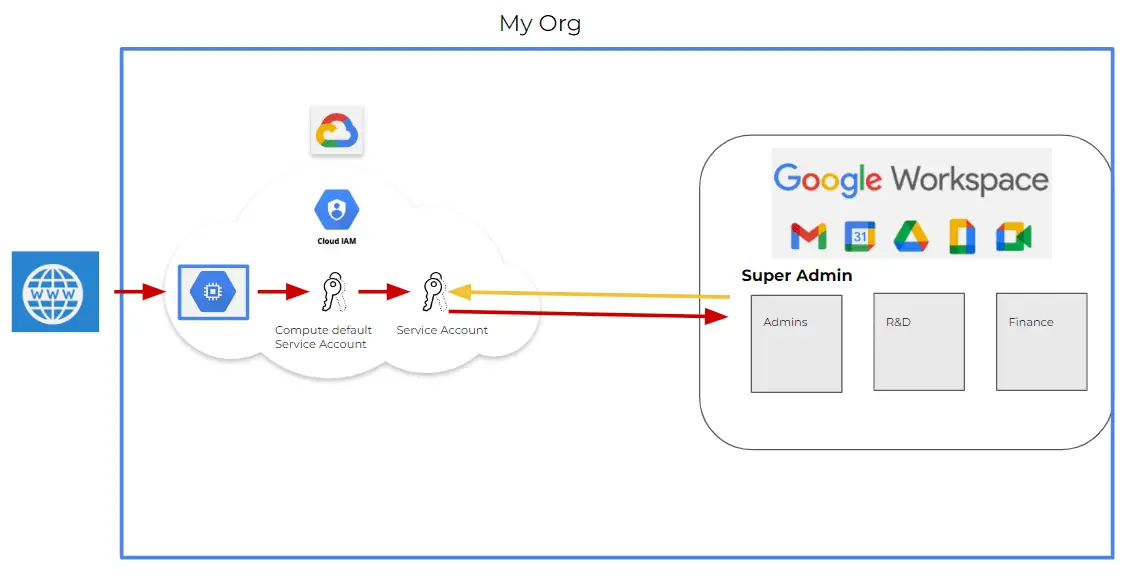
The critical risk lies in the ability of a GCP identity with necessary permissions to generate an access token for a delegated user. This scenario creates a potent pathway for malicious insiders or external attackers armed with stolen credentials. They can exploit this to impersonate Google Workspace users, gaining unauthorized access to sensitive data or conducting operations on their behalf.

An attacker or a malicious insider, such as a developer with editor permissions in a GCP project, could abuse a service account granted domain-wide delegation permissions in Google Workspace. With this access, they can impersonate users and authenticate API requests, accessing and potentially compromising confidential information like emails, documents, and other critical data stored within the domain.
This exploitation is facilitated by leveraging domain-wide delegation permissions, allowing a malicious actor to navigate from GCP to gain access to the Google Workspace environment. The capability to move laterally from GCP to Google Workspace exemplifies the seamless yet risky integration between these platforms.
To mitigate this risk, a hierarchical approach in the GCP hierarchy is recommended, where permissions and policies at higher levels do not automatically grant access to lower-level folders or projects. This strategy reduces the surface area for security breaches by potential malicious insiders who would typically only have permissions within lower-level folders or projects.
The revelation of this vulnerability emphasizes the importance of being vigilant in configuring permissions, especially concerning the domain-wide delegation feature. The mismatch between the initial permissions required for an attacker to misuse this feature and the potential impact is a stark reminder of the need for robust security practices in cloud environments.
The critical risk identified in Google Workspace’s Domain-Wide Delegation feature underlines the complexities and potential pitfalls of cloud-based services. It’s a call to action for organizations to reassess their cloud security posture, enforce least-privilege access, and stay vigilant against sophisticated cyber threats in an increasingly interconnected digital landscape.