fingerprintAllTheThings: extracting network metadata and fingerprints from pcap files and live network traffic
fingerprint all the things!
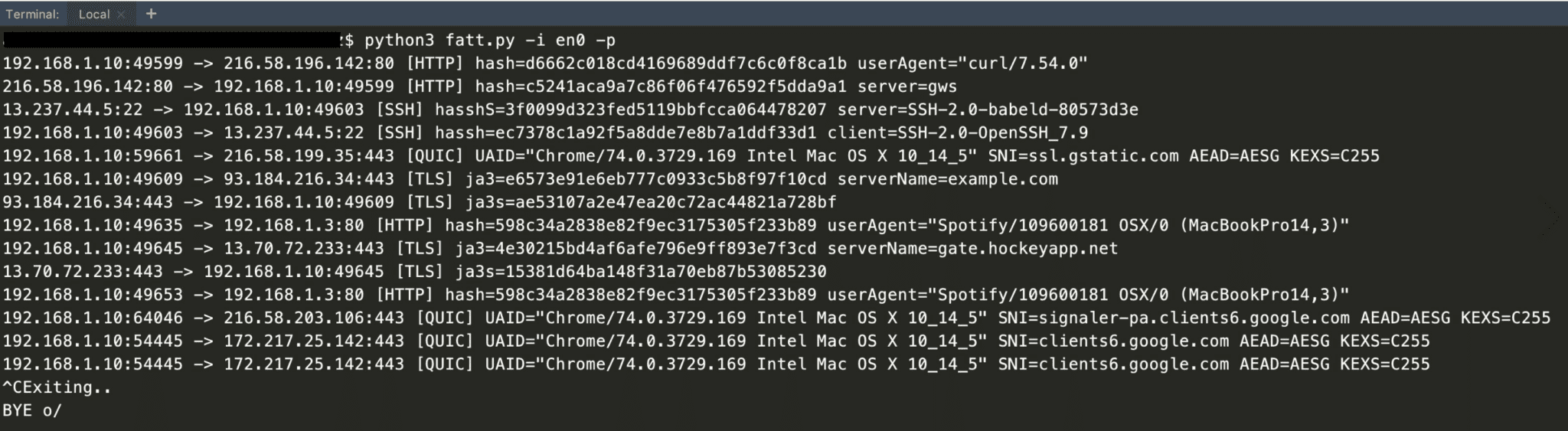
A script for extracting network metadata and fingerprints such as JA3 and HASSH from packet capture files (pcap) or live network traffic. The main use-case is for monitoring honeypots, but you can also use it for other use cases such as network forensic analysis. fatt works on Linux, macOS, and Windows.
Note that fatt uses pyshark (a python wrapper for tshark) and therefore the performance is not great! But that’s not a big issue as obviously, this is not a tool you use in production. You can use other network analysis tools such as Bro/Zeek, Suricata or Netcap for more serious use cases. Joy is another great tool you can use for capturing and analyzing network flow data.
Features
- Protocol support: SSL/TLS, SSH, RDP, HTTP, gQUIC.
- To be added soon: IETF QUIC, MySQL, MSSQL, etc.
- Fingerprinting
- JA3: TLS client/server fingerprint
- HASSH: SSH client/server fingerprint
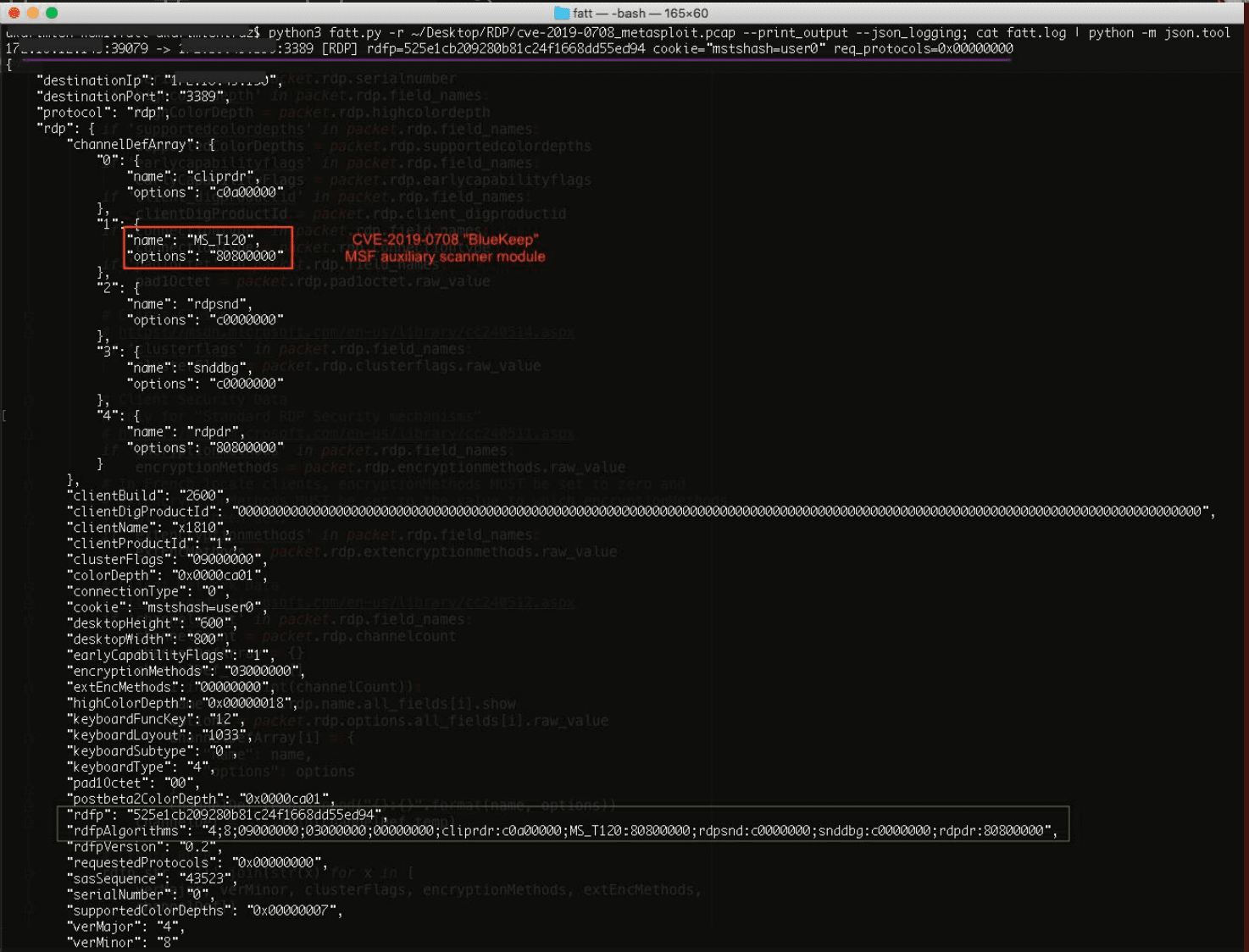
- RDFP: my experimental RDP fingerprint for standard RDP security protocol (note that other RDP security modes use TLS and can be fingerprinted with JA3)
- HTTP header fingerprint
- gQUIC/iQUIC fingerprint will be added soon
- JSON output
Install
- Install tshark
- git clone https://github.com/0x4D31/fatt.git
cd fatt/
pip3 install pipenv
pipenv install
Use
Let’s have a look at the captured traffic of Metasploit auxiliary scanner for the recent CVE-2019-0708 RDP vulnerability (BlueKeep).
Copyright (C) 2019 0x4D31
Source: https://github.com/0x4D31/