Website facade and the hidden exploit loader
Kaspersky Labs has uncovered a sophisticated campaign by the Lazarus APT group, utilizing a fake cryptocurrency game to lure unsuspecting investors and infect their systems with malware. The attackers employed a zero-day exploit in the Google Chrome web browser.
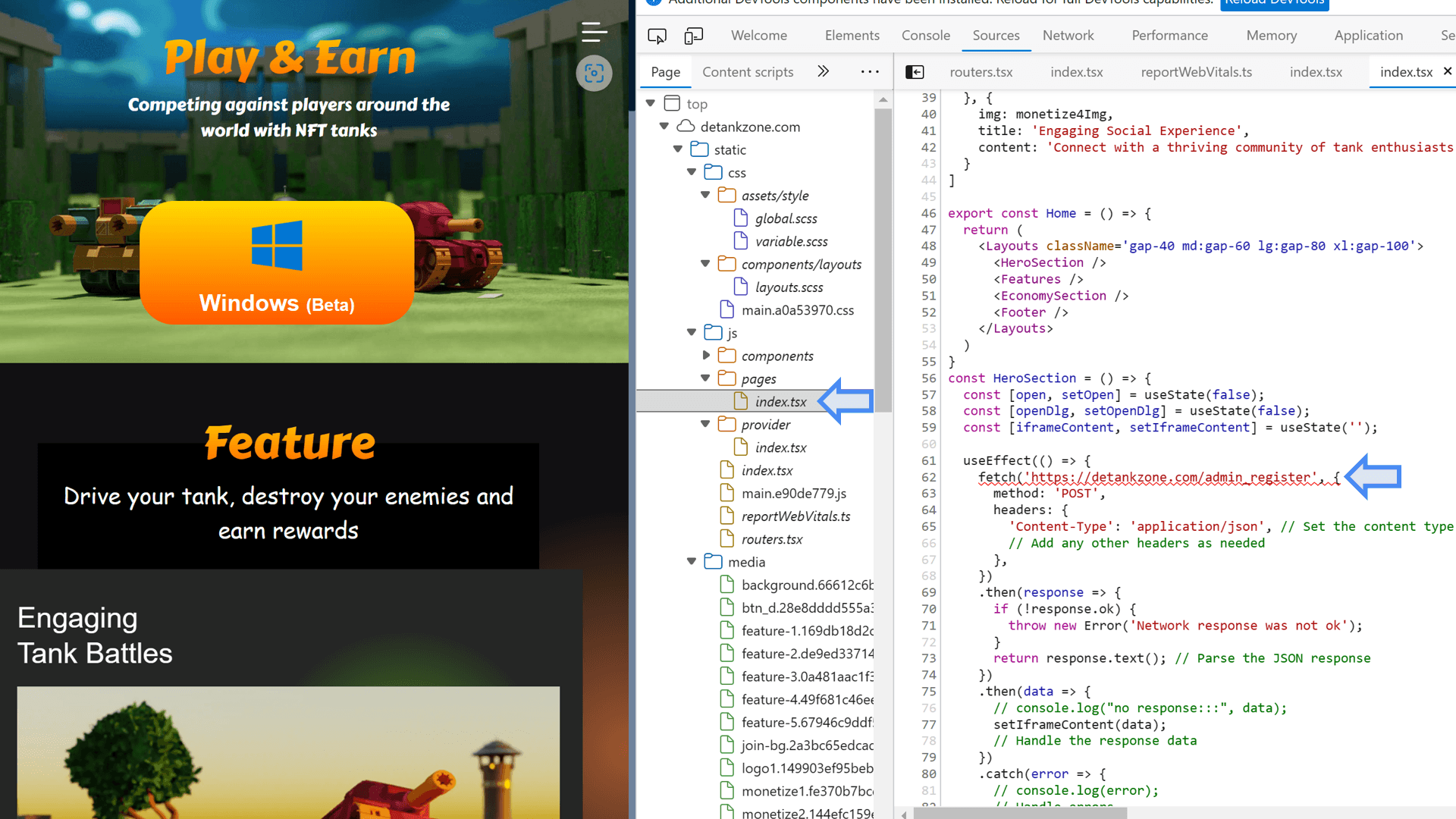
The campaign revolved around a seemingly legitimate website promoting “DeTankZone,” a decentralized finance (DeFi) NFT-based tank game. However, this website was a facade, harboring a hidden script that exploited a zero-day vulnerability in Google Chrome. “Visiting the website was all it took to get infected – the game was just a distraction,” Kaspersky researchers noted.
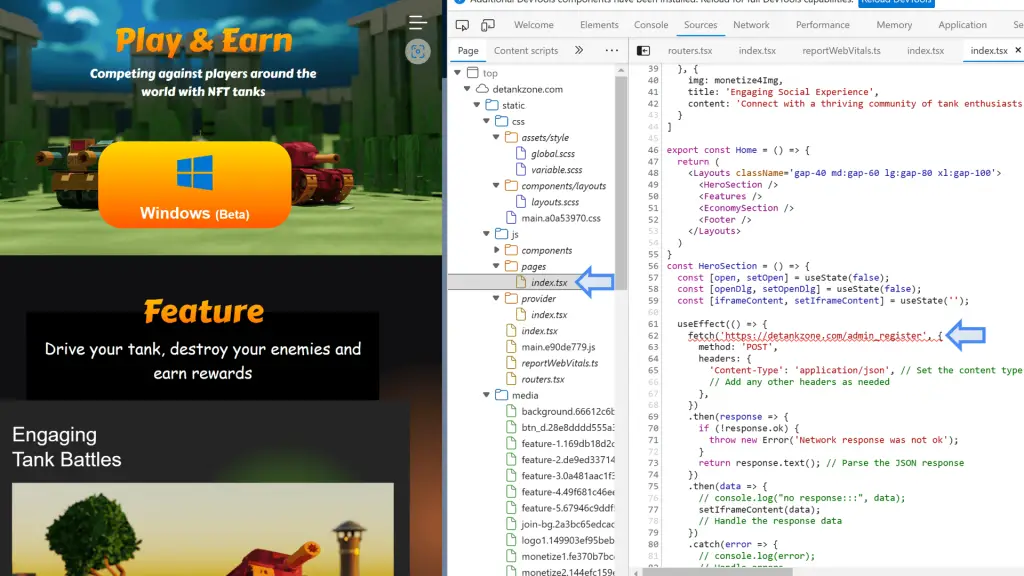
The attackers spared no effort in making the website appear legitimate, even developing it using modern frameworks like TypeScript/React. However, hidden within the index files of the site was a dangerous exploit aimed at Google Chrome’s V8 JavaScript engine. This exploit targeted two vulnerabilities: one to gain read/write permissions in Chrome’s process memory and another to bypass the V8 sandbox, effectively breaching Chrome’s security defenses.
Kaspersky discovered that the first vulnerability, CVE-2024-4947, resided in Chrome’s newly introduced Maglev compiler, part of its Just-In-Time (JIT) compilation pipeline. By exploiting this flaw, Lazarus was able to overwrite critical JavaScript object structures, triggering memory corruption and allowing arbitrary code execution. This vulnerability allowed the attackers to gain direct access to the memory of the Chrome process, paving the way for more severe breaches.
The attackers did not stop there. By chaining the CVE-2024-4947 vulnerability with a bypass of the V8 sandbox, they were able to escalate their privileges, breaking out of Chrome’s protective environment. This provided them with extensive control over the victim’s machine, from reading sensitive data to executing further payloads.
The Lazarus APT’s trademark is its sophisticated social engineering campaigns, and this latest attack was no exception. The group used multiple social media accounts on X (formerly Twitter) to promote DeTankZone, convincing cryptocurrency influencers and gamers alike to share the game link. Once users clicked on the malicious site, they were immediately vulnerable to the zero-day attack.

The attackers went to great lengths to make their campaign credible, even developing a functional prototype of the game. However, Kaspersky’s investigation revealed that the game’s source code was stolen from another developer, DeFiTankLand, whose cold wallet was hacked and $20,000 worth of DFTL2 coins stolen.
This campaign demonstrates the increasing sophistication of Lazarus APT’s tactics, leveraging social engineering, zero-day exploits, and even stolen game source code to achieve their malicious goals. “What makes Lazarus’s attacks particularly dangerous is their frequent use of zero-day exploits,” warned Kaspersky researchers. “Simply clicking a link on a social network or in an email can lead to the complete compromise of a personal computer or corporate network.”