
Fake e-shop campaign attack flow
In a disturbing development, a long-running scam campaign using fake e-commerce sites has significantly increased its danger. Initially focused on Malaysia, researchers at Cyble Research and Intelligence Lab (CRIL) reveal that this operation now has the potential to inflict serious financial harm across Southeast Asia.
This campaign, previously identified in 2021, has intensified its focus, now targeting 18 banks in Malaysia with a malign arsenal that includes Android malware integrated with unprecedented screen-sharing capabilities.
Originally casting a net over several Malaysian banks, the malevolent campaign has now broadened its horizons to ensnare financial institutions in Vietnam and Myanmar. This geographical expansion underscores the threat actors’ ambition and their increasingly sophisticated modus operandi.
The latest iteration of the malware showcases advanced features such as screen-sharing functionality, exploitation of accessibility services, and intricate communication channels with command and control (C&C) servers. This evolution indicates a significant leap in complexity and determination on the part of the attackers.

Cyble’s analysis in September 2022 reported a surge in fake e-shop activities across Malaysia, Vietnam, and Myanmar, revealing more than ten active phishing sites distributing an enhanced version of the malicious Android Package Kit (APK). This upgraded malware variant employs the open-source string obfuscator “Paranoid” and incorporates the Janus WebRTC module for screen sharing.
Victims are lured into downloading the malicious APK through phishing sites disguised as legitimate online shopping platforms. Once the malware is installed, it seeks Accessibility permissions to perform auto-clicks and other automated gestures on the infected device, thereby circumventing user interaction and further embedding its malicious activities.
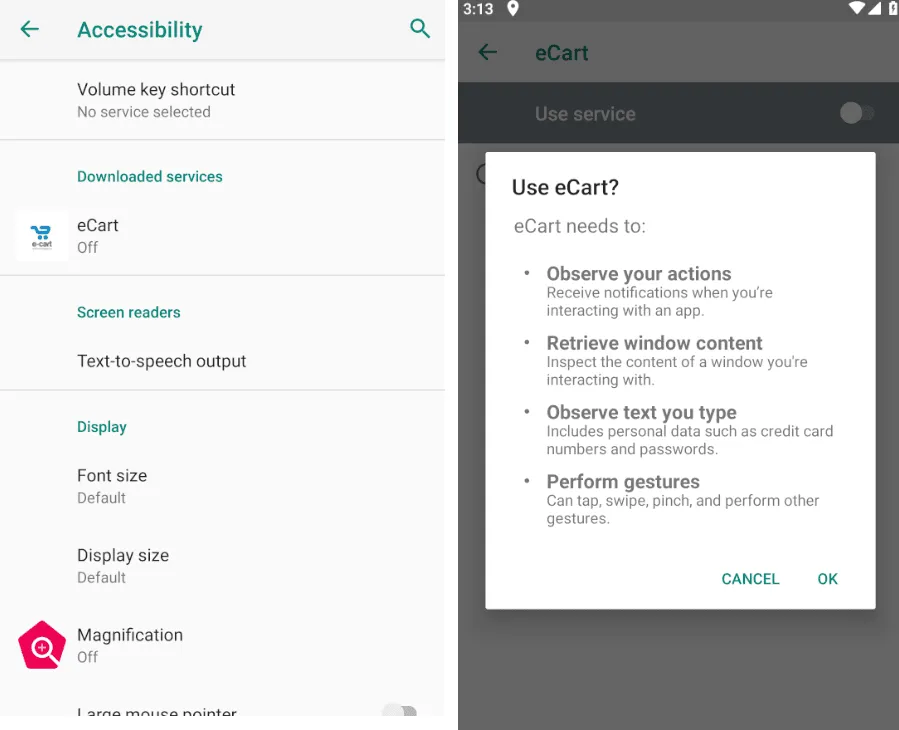
The introduction of screen-sharing functionality marks a significant advancement in the campaign’s capabilities. This feature, despite its operational challenges due to misconfiguration, signifies the threat actors’ intent to escalate their intrusion and data exfiltration efforts.
In Vietnam, the attackers set up a phishing site that mimicked an authentic payment application website, specifically targeting customers of Vietnam’s HD Bank. Similarly, in Myanmar, a malicious APK designed to mimic a cleaning service website sought to capture banking credentials for prominent banks through a phishing site crafted in the Burmese language.
The expansion of the fake e-shop campaign to target 18 banks in Malaysia, coupled with its reach into Vietnam and Myanmar, highlights a pressing concern for cybersecurity across the region. The inclusion of advanced malware features, such as screen-sharing and the exploitation of accessibility services, indicates that threat actors are continually refining their approaches to circumvent security measures and exploit vulnerabilities.
The campaign’s persistence and evolution underscore the importance of vigilance among users and financial institutions alike. It is crucial to exercise caution when downloading applications or engaging with online shopping platforms, especially those unfamiliar or unsolicited.