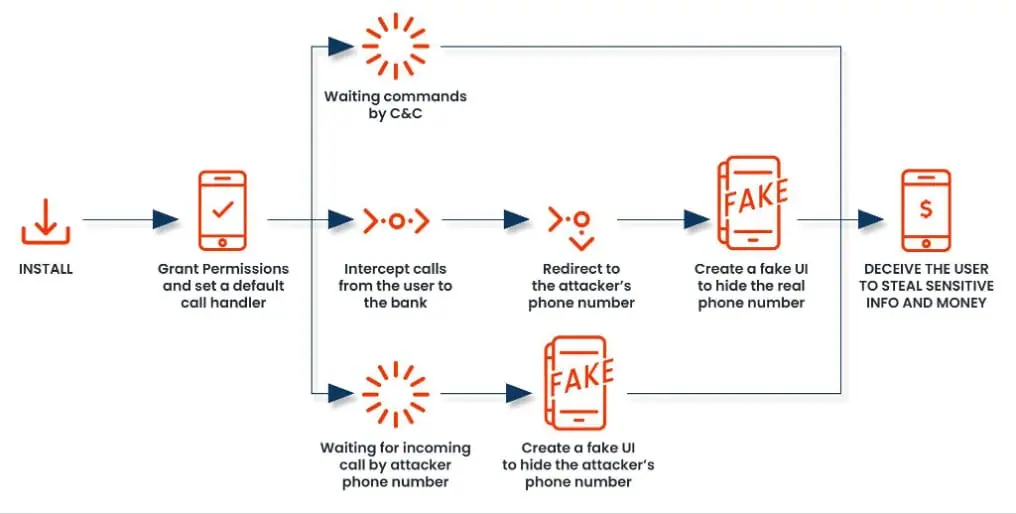
How the FakeCall Vishing Attack Works | Image: Zimperium
The zLabs team at Zimperium has issued an alert on a new variant of the FakeCall malware, a vishing (voice phishing) threat that targets mobile banking users through fraudulent phone calls. Disguised as a banking application, this malware variant enables attackers to intercept, control, and manipulate both incoming and outgoing calls, posing a serious threat to users’ sensitive financial information.
The FakeCall malware leverages Vishing—a subset of mobile phishing termed Mishing—to deceive users into divulging confidential information. The report explains, “FakeCall is an extremely sophisticated Vishing attack that leverages malware to take almost complete control of the mobile device, including the interception of incoming and outgoing calls.” By positioning itself as the device’s default call handler, FakeCall mimics the legitimate call interface, tricking users into believing they’re speaking to their bank or financial institution when they’re actually connected to an attacker.
The attack begins when a user downloads an infected APK file, commonly through phishing links. Once installed, the malware acts as a dropper to install its second-stage payload, establishing a connection with a Command and Control (C2) server. The zLabs team notes, “The samples we have identified belong to this second-stage malware,” which communicates with the C2 server to execute various deceptive actions designed to steal information.
FakeCall is equipped with advanced tools that allow attackers to manage user interactions seamlessly:
- Call Redirection and UI Manipulation: Once designated as the default call handler, the malware intercepts outgoing calls. Users attempting to contact their bank are unknowingly redirected to a fraudulent number. The app displays a fake user interface mimicking the Android call app, making it nearly impossible for victims to detect the fraud.
- Automatic Permissions and Remote Control: By exploiting the Android Accessibility Service, the malware can grant itself necessary permissions, bypassing the need for user consent. This includes the ability to manipulate device interactions remotely, with the zLabs team revealing, “The malware enables remote attackers to take full control of the victim’s device UI, allowing them to simulate user interactions.”
- Data Collection: FakeCall doesn’t stop at calls. It can upload contacts, call logs, SMS messages, and even audio recordings of calls to the C2 server. The zLabs report outlines, “The malware incorporates a new service inherited from the Android Accessibility Service, granting it significant control over the user interface and the ability to capture information displayed on the screen.”
Perhaps the most insidious feature of FakeCall is its ability to convincingly impersonate a banking interface. If a user attempts to call their bank, FakeCall intercepts the call and displays the bank’s real phone number on a fake dialer screen. This deceptive UI allows attackers to interact with victims as if they were genuine bank representatives, capturing sensitive information like login credentials and PIN codes.
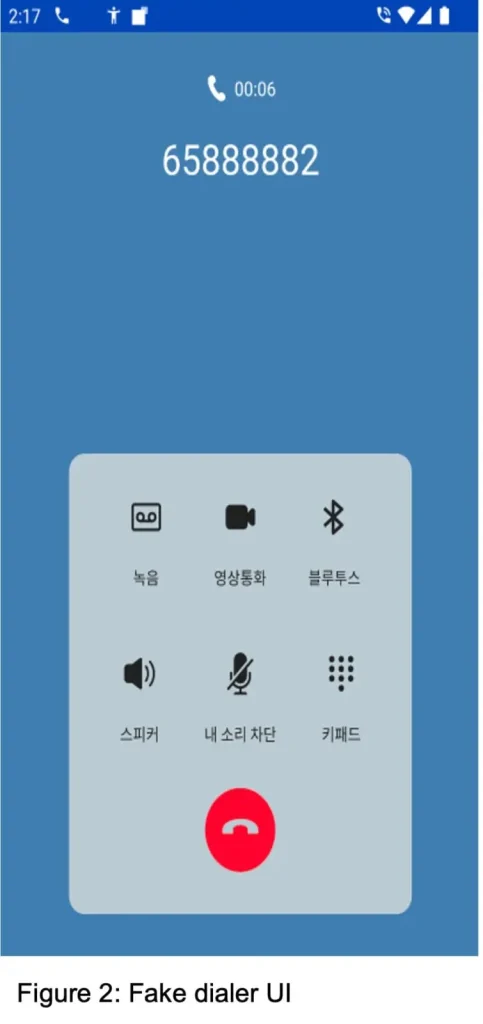
The zLabs team warns that “When the compromised individual attempts to contact their financial institution, the malware redirects the call to a fraudulent number controlled by the attacker.” This setup allows attackers to stage a seamless, lifelike interaction to extract valuable financial data.
As the zLabs team continues to investigate, users are advised to exercise caution when downloading apps outside official app stores, avoid clicking on suspicious links, and review their device’s call handler permissions.
Related Posts:
- ZLAB Announces Ransomware-as-a-Service platforms Report
- CSE CybSec ZLAB releases Malware Analysis Report: Dark Caracal APT
- Massive Scam Surge: Google Ads Fueling Fraud