In an ever-evolving digital landscape, the specter of malware looms large. Cybercriminals, armed with sophisticated tools and tactics, continually devise new ways to exploit vulnerabilities, targeting unsuspecting users and organizations. Security researchers from Kaspersky unravels the intricate web of modern malware, examining how they operate, the threats they pose, and the steps to mitigate their impact.
1. The Evolution of Malware Distribution: The FakeSG Campaign

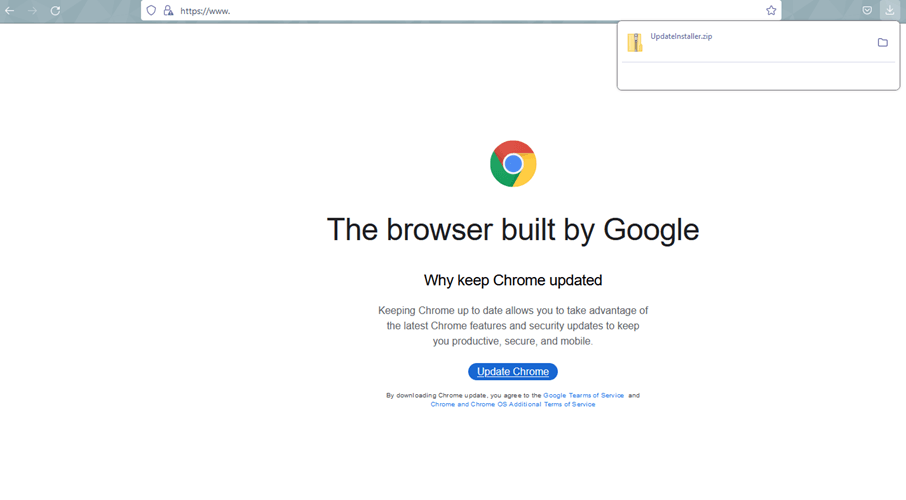
The ingenuity of malware distribution is exemplified by the FakeSG campaign, a sinister operation that employs a NetSupport RAT (Remote Access Trojan). Cybercriminals cleverly infect legitimate websites, tricking users into downloading malware under the guise of a browser update. This campaign demonstrates the adaptive nature of threat actors, who constantly modify their tactics to evade detection.
2. Akira Ransomware: A New Threat on the Horizon
Akira, a new ransomware variant detected in April, showcases the escalating sophistication of malware. Capable of operating in Windows and Linux environments, Akira targets large organizations across various industries. While sharing common traits with other ransomware families, such as encrypting logical drives and deleting shadow copies, Akira distinguishes itself with unique features, like its old-school, minimalist communication site on the TOR network, which employs robust security measures to thwart analysis.
3. The Rise of macOS Stealers: The Case of AMOS
MacOS users, often perceived as less susceptible to malware, face a growing threat from stealers like AMOS. Discovered in April 2023, AMOS exemplifies the burgeoning market for macOS-targeted malware. Initially leased to cybercriminals via Telegram, AMOS has evolved, both in terms of programming language and infection methods. It showcases the alarming trend of malvertising, where popular software sites are cloned to distribute malware, highlighting the need for heightened vigilance among macOS users.
The global reach of these malware campaigns, from FakeSG to Akira and AMOS, underscores the universal vulnerability to cyber threats. These campaigns have left footprints across continents, with countries like Russia and Brazil being heavily targeted. This global pandemic of cybercrime necessitates a concerted effort in cybersecurity practices, including regular software updates, robust security solutions, and continuous user education.