Fenrir v0.9: Simple Bash IOC Scanner
Fenrir
Simple Bash IOC Scanner
Fenrir is a simple IOC scanner bash script. It allows scanning Linux/Unix/OSX systems for the following Indicators of Compromise (IOCs):
- HashesMD5, SHA1, and SHA256 (using md5sum, sha1sum, sha -a 256)
- File Namesstring – checked for substring of the full path, e.g. “temp/p.exe” in “/var/temp/p.exe”
- Stringsgrep in files
- C2 Serverchecking for C2 server strings in ‘lsof -i’ and ‘lsof -i -n’ output
- Hot Time Frameusing stat in different modes – define min and max epoch timestamp and get all files that have been created in between
Basic characteristics:
- Bash Script
- No installation or agent needed
- Uses common tools to extract attributes (e.g. md5sum, grep, stat in different modes)
- Intended to run on any Linux / Unix / OS X with Bash
- Low footprint – Ansible playbook with RAM drive solution
- Smart exclusions (file size, extension, certain directories) speeds up the scan process
Step by Step
What Fenrir does is:
- Reads the IOC files
- Takes a parameter as starting directory for the recursive walk
- Checks C2 servers in lsof output
- Checks for directory exclusions (configurable in the script header)
- Checks for certain file extensions to check (configurable in the script header)
- Checks the file name (full path) for matches in IOC files
- Checks for file size exclusions (configurable in the script header)
- Checks for certain strings in the file (via grep)
- Checks for certain hash values
- Checks for change/creation timestamp
Changelog v0.9
- of a compromise (see IOC files)
- of vulnerable log4j versions (hash list by @mubix)
Download
git clone https://github.com/Neo23x0/Fenrir.git
Usage
Usage: ./fenrir.sh DIRECTORY
DIRECTORY – Start point of the recursive scan
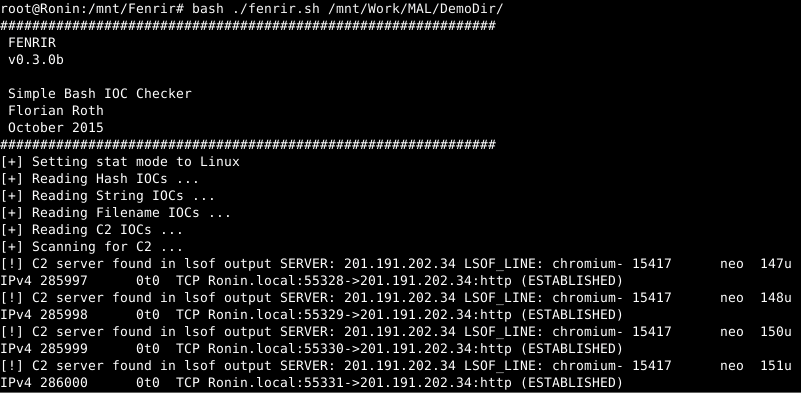
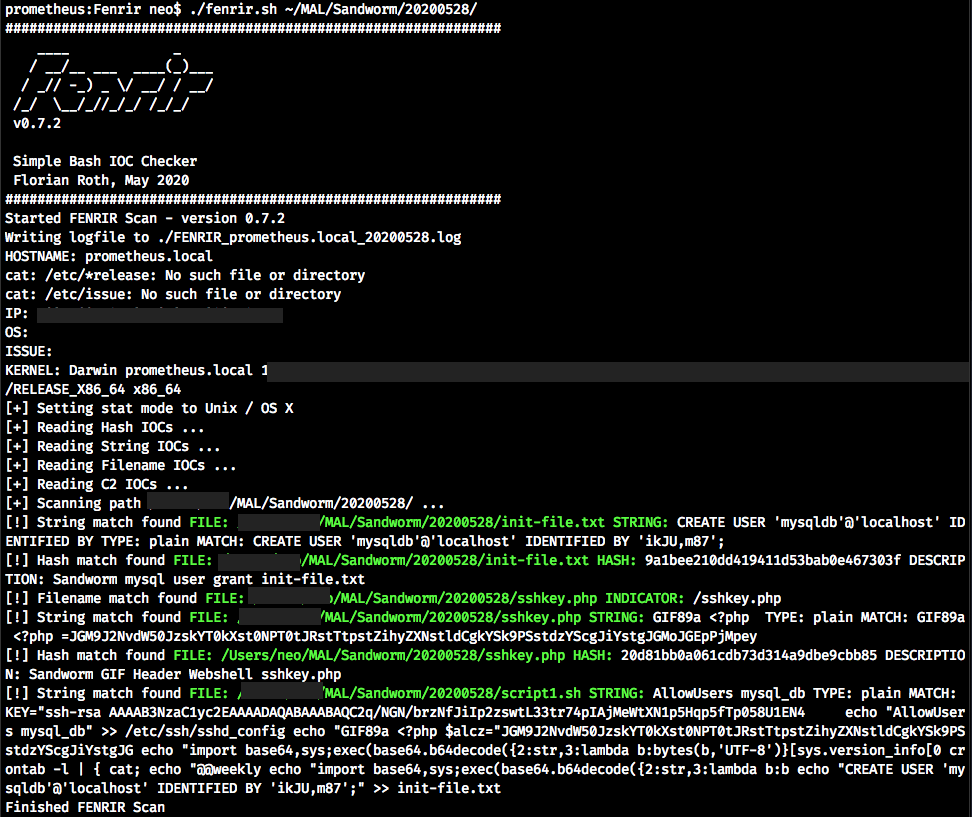
Scan Run showing the different match types in a demo directory.
Detect C2 connections
Detect strings in GZIP packed log files
Configuration
Ansible Playbook
Stat issue (regarding the CREATED file stamp on Linux file systems)
Copyright (c) 2015 Florian Roth
Source: https://github.com/Neo23x0/










