fibratus v2.0 releases: exploration and tracing of the Windows kernel
Fibratus
Fibratus is a tool for exploration and tracing of the Windows kernel. It lets you trap system-wide events such as process life-cycle, file system I/O, registry modifications or network requests among many other observability signals. In a nutshell, Fibratus allows for gaining deep operational visibility into the Windows kernel but also processes running on top of it.
Events can be shipped to a wide array of output sinks or dumped to capture files for local inspection and forensics analysis. The powerful filtering engine permits drilling into the event flux entrails.
You can use filaments to extend Fibratus with your own arsenal of tools and so leverage the power of the Python ecosystem.
Features
- ⚡ blazing fast
- 📡 collects a wide spectrum of kernel events – from process to network observability signals
- 🔍 the super powerful filtering engine
- 🐍 running Python scriptlets on top of kernel event flow
- 💽 capturing event flux to kcap files and replaying anywhere
- 🚀 transporting events to Elasticsearch, RabbitMQ or console sinks
- ✂️ transforming kernel events
- 🐞 scanning malicious processes and files with Yara
- 📁 PE (Portable Executable) introspection
Filtering
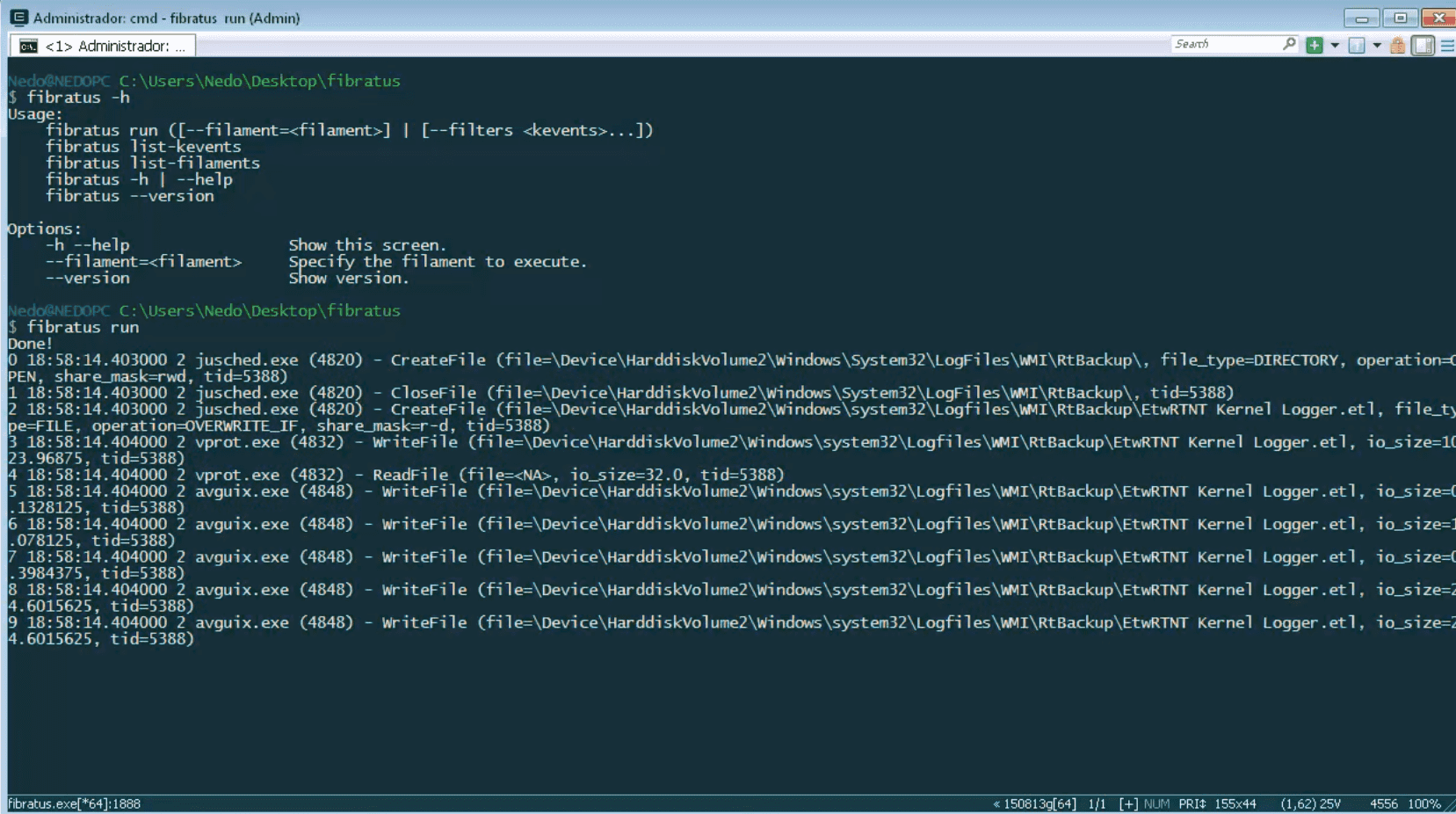
Fibratus supports basic filtering capabilities on kernel event names. To capture the specified kernel events, use fibratus run --filters command. For example, fibratus run --filters CreateProcess Send would capture the events related to process creation and data sending over network sockets. For a full list of the kernel, events see the table below.
| Kernel event | Description |
|---|---|
| ContextSwitch | Scheduler selects a new thread to run |
| CreateProcess | Creates a new process and its primary thread |
| CreateThread | Creates a thread to execute within the virtual address space of the calling process |
| TerminateProcess | Terminates the process and all of its threads |
| TerminateThread | Terminates a thread |
| LoadImage | Loads the module into the address space of the calling process |
| UnloadImage | Frees the loaded module from the address space of the calling process |
| CreateFile | Creates or opens a file or I/O device |
| CloseFile | Closes the file or I/O device |
| DeleteFile | Deletes an existing file or directory |
| RenameFile | Renames a file or directory |
| ReadFile | Reads data from the file or I/O device |
| WriteFile | Writes data to the file or I/O device |
| Send | Sends data on a connected socket |
| Recv | Receives data from a connected socket |
| Accept | Initiates the connection attempt from the remote or local TCP socket |
| Connect | Establishes the connection to a TCP socket |
| Disconnect | Closes the connection to a TCP socket |
| Reconnect | Reconnects to a TCP socket |
| RegCreateKey | Creates the registry key or opens it if the key already exists |
| RegQueryKey | Retrieves information about the registry key |
| RegOpenKey | Opens the registry key |
| RegDeleteKey | Deletes a subkey and its values |
| RegQueryValue | Retrieves the type and data of the value associated with an open registry key |
| RegSetValue | Sets the data and type of a value under a registry key |
| RegDeleteValue | Removes a value from the registry key |
New features
- New
VirtualAllocandVirtualFreeevents. Read more - New
MapViewFileandUnmapViewFileevents and mapped-files state. Read more - New
DuplicateHandleevent Read more - DNS telemetry via
QueryDnsandReplyDnsevents Read more - New
RegCloseKeyevent - Image signature information exposed via parameters and
image.signature.type/image.signature.levelfilter fields Read more - Image format parameters and filter fields
- Decorate non-open disposition
CreateFileevents with image format parameters - Macros for detecting loading of unsigned/untrusted modules
ps.sidfilter field contains the raw SID value, e.g.S-1-5-18- Parse and append
create_optionsparameter toCreateFileevents - Certificate info and filter fields for
LoadImage/UnloadImageevents - Expand
pefilter field set and allow lazily value extraction Read more - Support for expressions with bare boolean filter fields
Enhancements
- Significant core refactoring to aim for a more sustainable codebase growth
- Refactored many tests to embrace table-driven testing
- Introduce a new set of parameter types such as flags, system status code, file path, address, etc.
- Switch to
golang.org/sys/windowspackage for the vast majority of API calls and structures - Use the syscall generator to produce stubs for the API calls not available through
golang.org/sys/windows - Bump
golangci-lintlinters to version1.52.2 - Event consumer tests to verify the correctness of captured events
- Trace controller tests to verify real-world tracing session management
- Harden driver handle objects decoration of the file path parameters
- Expand the size of the
Ktypetype to accommodate 2-bytes event hook identifiers - Switch to the upstream
saferwall/pepackage for version resource parsing - Only allow a single instance of the Fibratus process to be run simultaneously
Configuration changes
- Disable initial handle snapshot to reduce overall memory utilization
- Added
RegCloseKeyto the list of ignored events - Removed the
Systemprocess image from the list of ignored processes
Deprecation
- Remove
kstream.raw-event-parsingconfig flag as binary event parsing is the default option now - Nuke TDH event parsing functionality
- Sunset Antimalware provider as we can tap into driver loading events via
LoadImageevents
Bug fixes
- Resolution of success system codes should compare the range of information values
- Use only the rule name in the filter field deprecation log message
- Solved
yaratests hanging issues
Breaking changes
- Convert flags event parameters to uppercase strings
- The
sidparameter and theps.sidfilter fields contain the raw SID value instead of the username/domain tuple - Command line parameters and filter fields contain the original, unexpanded command line
- The major kcap file format version is increased in this version. The side-effect is the inability to replay old capture files
operationparameter name in theCreateFileevent is renamed tocreate_dispositionshare_maskparameter contains the full permission name, e.g.READ|WRITE|DELETEcommparameter name in process events is renamed tocmdline
Download & Usage

Copyright 2015/2016 by Nedim Sabic (RabbitStack)
Source: https://github.com/rabbitstack/