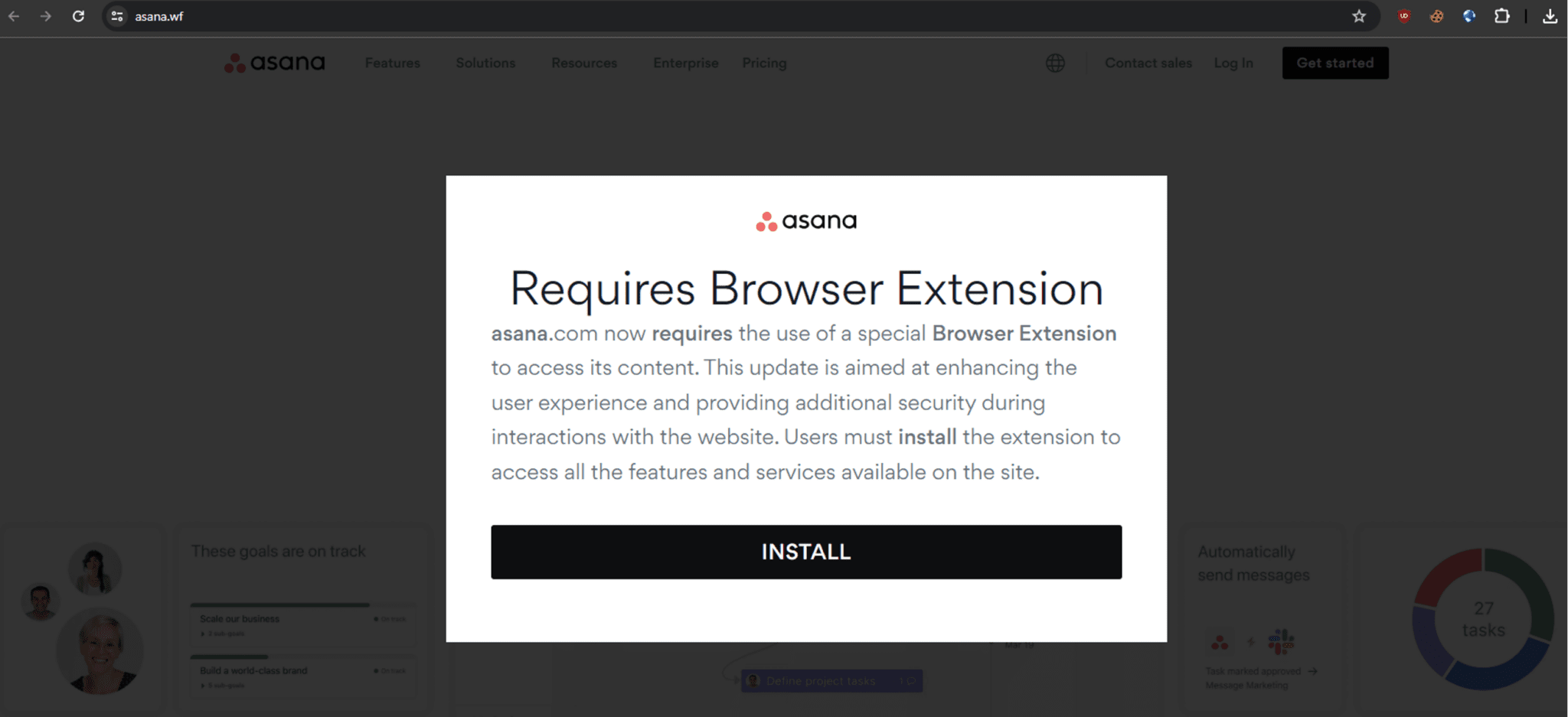
Malicious website serving the malicious payload
Researchers at eSentire’s Threat Response Unit (TRU) have uncovered a disturbing trend in FIN7 attacks demonstrating the notorious cybercrime group’s evolving tactics for infiltrating systems. FIN7’s campaign targets users with malicious websites disguised as legitimate brands, spreading NetSupport RAT and the powerful DiceLoader malware to gain backdoor access.

In a series of incidents observed in April 2024, FIN7 crafted malicious websites that convincingly impersonated reputable companies such as AnyDesk, WinSCP, BlackRock, Asana, Concur, The Wall Street Journal, Workable, and Google Meet. Visitors to these sites were met with pop-up notifications urging them to download seemingly innocuous browser extensions. These pop-ups, however, were fronts for initiating downloads of MSIX files, a packaging format used by Windows apps that appeared legitimate but contained malicious payloads.
Upon visiting the malicious sites via sponsored Google Ads, users unknowingly triggered the download of these MSIX files, which were intricately crafted to deploy the NetSupport Remote Access Trojan (RAT) and subsequently, DiceLoader, a secondary payload. This two-stage infection process was meticulously designed to first gain control over the victim’s system and then deliver further malicious software.
Case One: A user downloads a fake extension from a spoofed website. The MSIX file harbors a malicious PowerShell script that executes automatically.
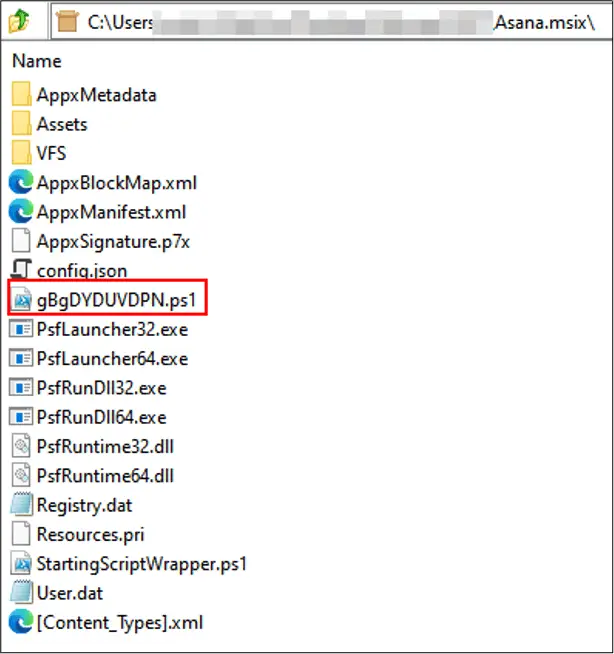
This script is designed to:
- Collect system information such as OS version and antivirus products.
- Generate a unique identifier (GUID) for the compromised machine.
- Download additional payloads from a command and control (C2) server using a detailed URL, which is constructed using the system information collected.
Case Two: Similar to the first, this case involves a user being deceived into downloading a fake “MeetGo” MSIX installer from a fraudulent website. Post installation, NetSupport RAT is activated, and about three hours later, the attacker connects to the machine. The attacker then uses the RAT to execute further malicious activities, including:
- Downloading tools to extract Active Directory data.
- Executing a Python payload for additional data gathering and command execution.
The MSIX files used in these attacks were found to be signed by “SOFTWARE SP Z O O” and “SOFTWARE BYTES LTD,” adding a veneer of legitimacy. eSentire has since contacted GlobalSign to get these certificates revoked, mitigating some risk associated with these files.
Given the cunning nature of these attacks, we recommend:
- Vigilance when interacting with pop-ups and downloads, even from seemingly reputable sources.
- Regular updates to antivirus and anti-malware solutions to detect and prevent the execution of malicious scripts.
- Educating employees about the dangers of sponsored ads and the importance of verifying software through official channels.