lorsrf
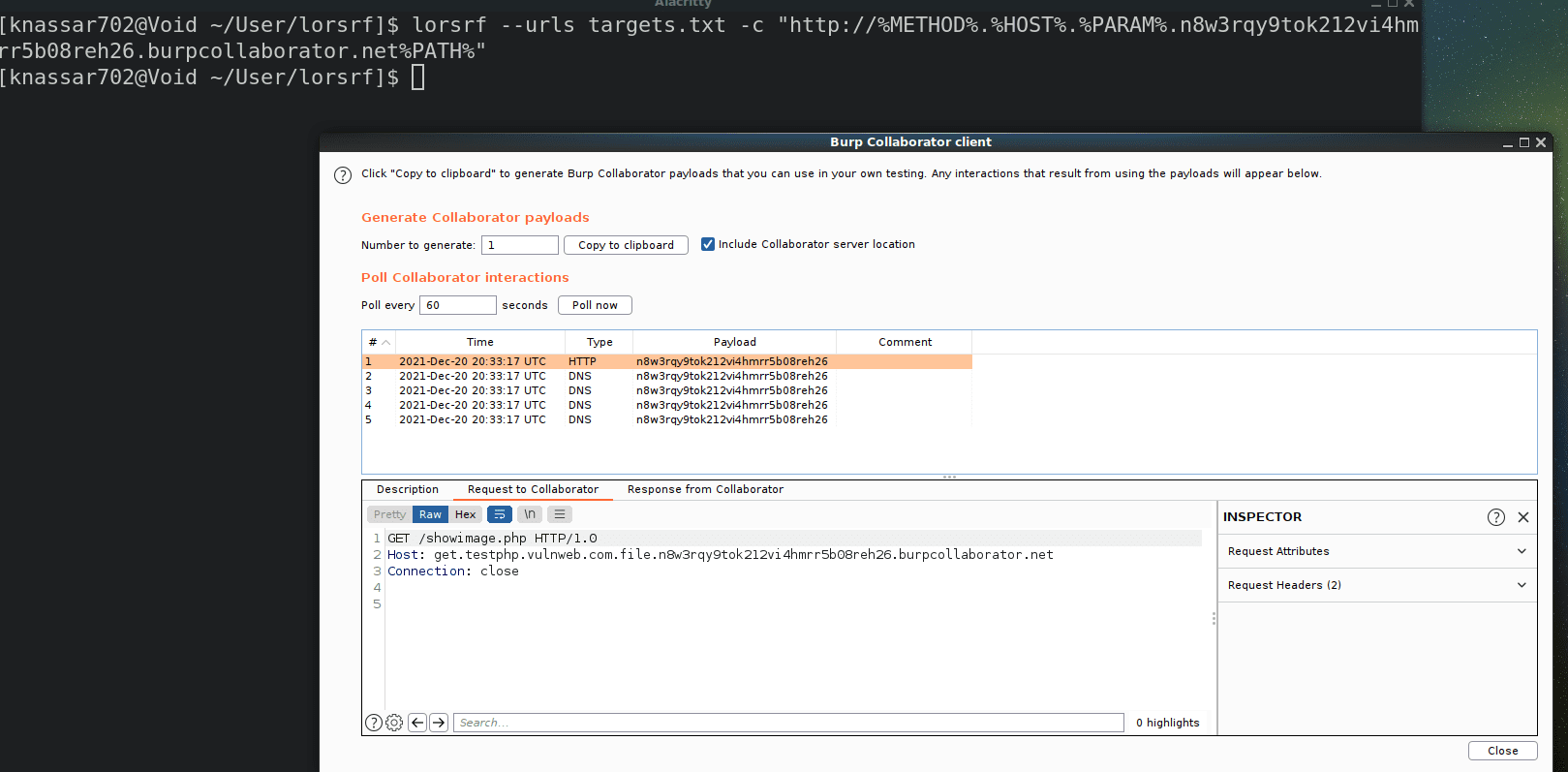
lorsrf is just a web pen-testing tool that I wrote to find the parameters that can be used to find SSRF or Out-of-band resource load by adding an OAST host like Burp Collaborator to the parameter value, above of all, the request that will be received in Burp Collaborator will be an HTTP request without any real pieces of information about the target, I was thinking about how can I get vulnerable parameter/endpoint, Hence I made a simple feature is that allowed you to add some pieces of information of the target in your OAST host as a variable.

| Variable | Description |
|---|---|
| %PARAM% | the guessed parameter |
| %PATH% | the endpoint of your target domain |
| %HOST% | the scanning host |
| %QUERY% | the query of the url |
| %METHOD% | Current METHOD |
you can use these to include more information in your OAST host
target: http://testphp.vulnweb.com/showimage.php
payload: http://%HOST%.%PARAM%.testing.interactsh.com%PATH%
output: http://testphp.vulnweb.com.file.testing.interactsh.com/showimage.php
by default, lorsrf use the GET method if you want a post method with form body or json you can add these flags
$ lorsrf –json –form
Changelog v2.1
-
Fix progressbar
Install
- install rust from https://www.rust-lang.org/learn/get-started
- run these commmands
>>> apt install gcc pkg-config libssl-dev
>>> cargo install –git https://github.com/knassar702/lorsrf
Use
Examples
$ lorsrf –urls targets.txt -c “http://myhost.com” –wordlist params.txt
- json
$ lorsrf –urls targets.txt -c “http://myhost.com” –wordlist params.txt –json
- form
$ lorsrf –urls targets.txt -c “http://myhost.com” –wordlist params.txt –form
parameter scanner without guessing
$ waybackurls http://testphp.vulnweb.com > urls.txt
$ lorsrf –urls urls.txt -c “http://myhost.com“ –wordlist params.txt
Copyright (C) 2020 knassar702
Source: https://github.com/knassar702/