FirmAE: Towards Large-Scale Emulation of IoT Firmware for Dynamic Analysis
FirmAE
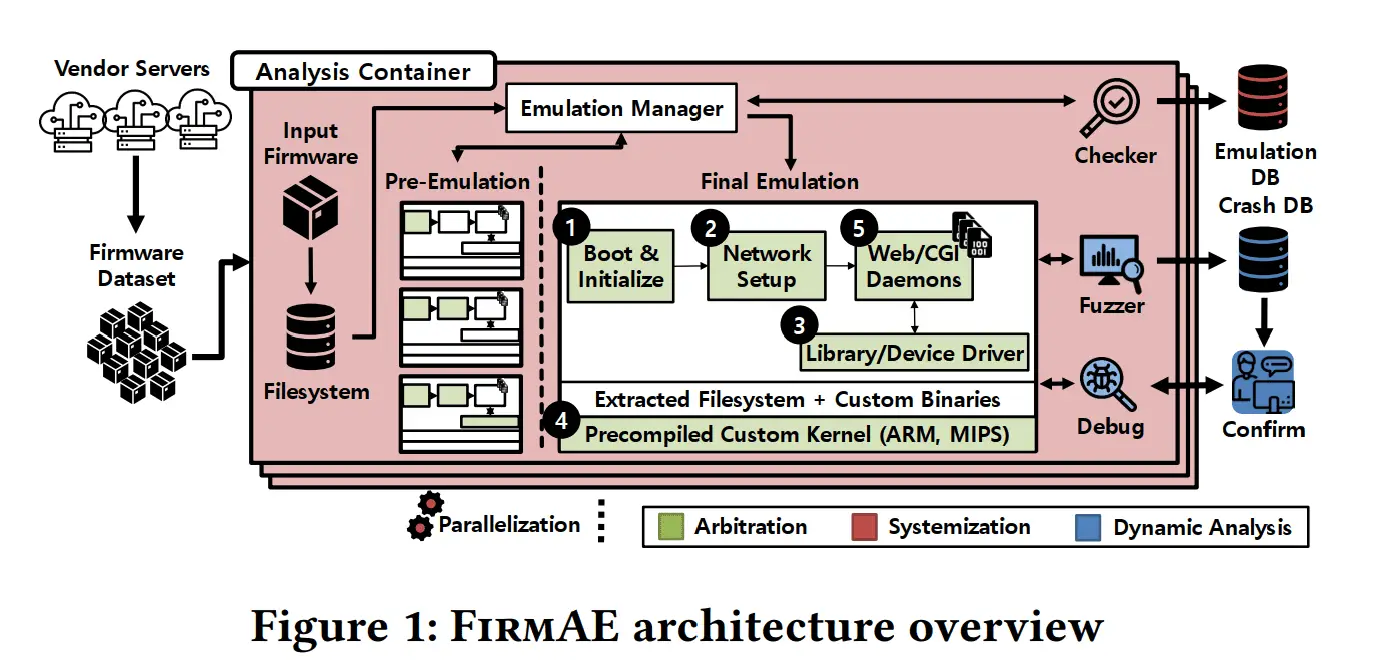
FirmAE is a fully-automated framework that performs emulation and vulnerability analysis. FirmAE significantly increases the emulation success rate (From Firmadyne‘s 16.28% to 79.36%) with five arbitration techniques. We tested FirmAE on 1,124 wireless routers and IP-camera firmware images from the top eight vendors.
We also developed a dynamic analysis tool for 0-day discovery, which infers web service information based on the filesystem and kernel logs of target firmware. By running our tool on the successful emulation firmware images, we discovered 12 new 0-days which affect 23 devices.

FirmAE emulates a firmware image similar to Firmadyne on a pre-built customized Linux kernel and libraries. It also emulates a target image twice to collect various system logs and utilize the information for further emulation. We refer to the former emulation step as pre-emulation and the latter as final emulation. The arbitrations applied in FirmAE can be categorized into five, which are derived by our failure case investigation on AnalysisSet.
For large-scale analysis, FirmAE needs to be fully automated. Naturally, numerous steps of Firmadyne are automated; however, it still requires some user interaction. For example, users must first extract the filesystem of the target firmware with specific options. Then, they evaluate whether the filesystem is successfully extracted and retrieve the architecture information. Subsequently, they make a firmware image for QEMU and collect information in pre-emulation. Finally, they run a script for final emulation and perform dynamic analysis. We automated all such interactions and added an automated evaluation procedure for network reachability and web service availability. For this, we built a module in FirmAE that periodically runs ping and curl commands.
Install & Use
Copyright (c) 2015 – 2016, Daming Dominic Chen
Copyright (c) 2017 – 2020, Mingeun Kim, Dongkwan Kim, Eunsoo Kim