Image: Sekoia
A large-scale operation to remove the PlugX trojan from infected devices has commenced in six countries. This campaign was organized by the French police with the support of Europol and the French cybersecurity company Sekoia.
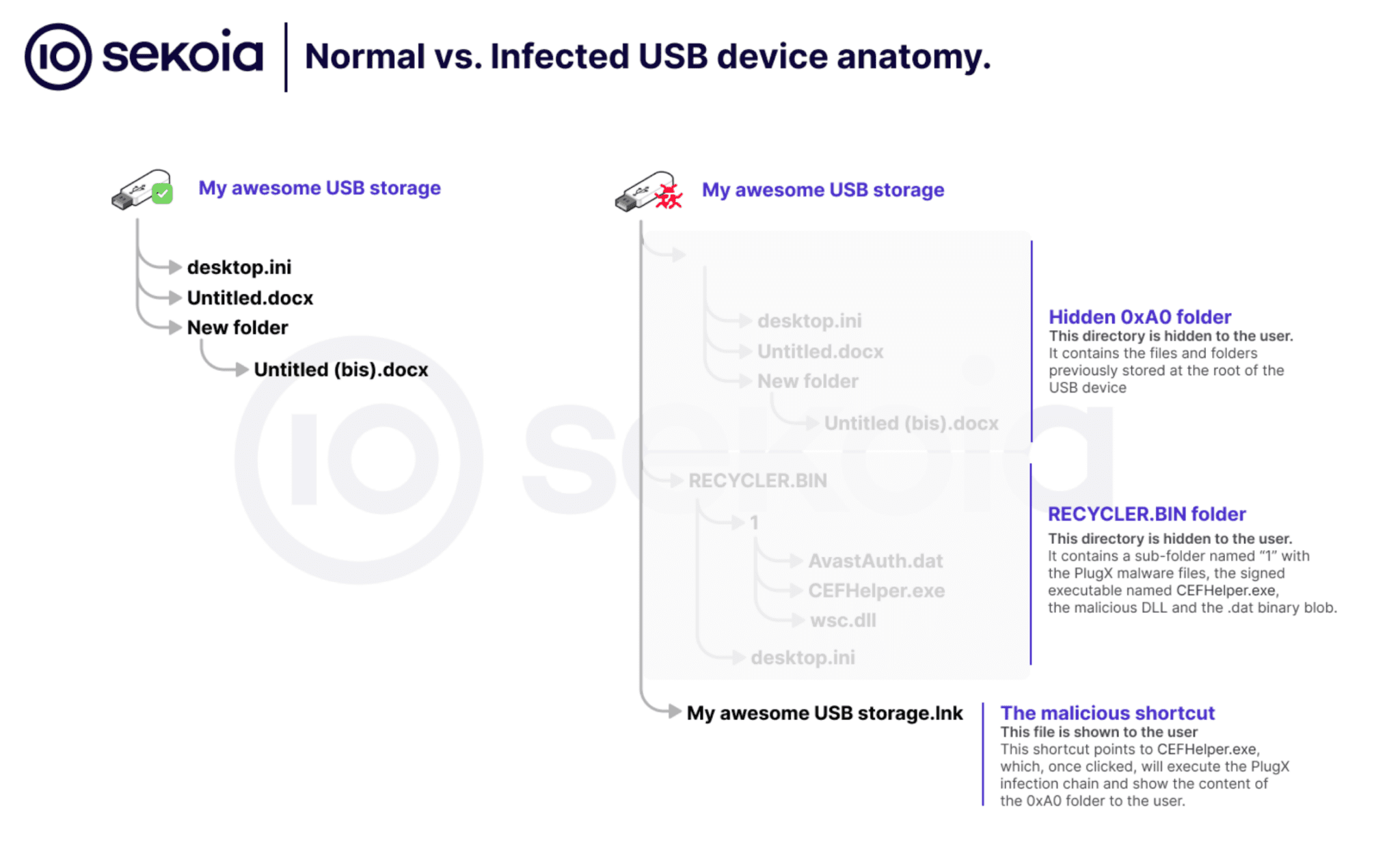
PlugX is a Remote Access Trojan (RAT) that has long been used by Chinese hackers. New versions of PlugX are modified and released based on the current needs of the attackers.
In April, Sekoia took control of the C2 server of one variant of PlugX. The malware spread through USB drives, creating a botnet that continued to infect devices even after being abandoned by its operator. As a result, in six months of autonomous operation, the trojan infected approximately 2.5 million devices worldwide. Since the botnet remained active, it was susceptible to being hijacked by other cyber criminals.
To mitigate the threat, Sekoia specialists proposed a cleansing mechanism that uses a special plugin for PlugX, which sends a command to the infected device to self-destruct the malware. They also suggested a method for scanning connected USB drives to remove the trojan. However, automatic cleaning of USB drives could damage the media and lead to the loss of legitimate files, making this approach risky.
Given the legal complexities that could arise from conducting a large-scale cleanup campaign, Sekoia handed over its solution to Computer Emergency Response Teams (CERT), law enforcement agencies, and cybersecurity regulators.
Europol received the “disinfector” and shared it with partner countries to remove PlugX from devices. Although details about the cleaning mechanism are not disclosed, the created program is likely similar to the PlugX module described in Sekoia’s April report.
Amidst the 2024 Paris Olympics, French authorities are on high alert, and the risk of PlugX being present in 3,000 systems in France is unacceptable. Consequently, PlugX is now being removed from infected systems not only in France but also in Malta, Portugal, Croatia, Slovakia, and Austria. The cleanup operation began on July 18 and will likely continue for several months, probably until the end of the year.
It is noted that this variant of PlugX spreads through infected USB drives, and it is unknown whether Sekoia’s solution includes the capability to remove malware from removable media. Users are advised to exercise caution when connecting USB drives to computers in print shops and other locations where numerous physical connections occur daily and to scan their devices before connecting them to systems containing sensitive data.
Europol and the French authorities have not provided comments.
Related Posts:
- PlugX malware: The Enigma of Cyber Espionage Unveiled
- Earth Preta’s Targeted Asian Campaigns: The DOPLUGS Malware Threat
- French and German finance ministers called for a ban on bitcoin
- French security researcher: 20,000 Aadhaar cards available online