Process flow | Source: ASEC
The AhnLab Security Intelligence Center (ASEC) has uncovered a series of cyberattacks on Korean companies orchestrated by the TIDRONE threat actor. Known for its focus on Taiwanese defense and drone industries, TIDRONE has now extended its operations to South Korea, exploiting Enterprise Resource Planning (ERP) software to deploy the CLNTEND backdoor malware.
Initially identified by Trend Micro in September 2024, TIDRONE is linked to a threat group associated with Chinese-speaking operators. Their activities have targeted organizations in Taiwan and now extend to South Korea, particularly small-scale ERP solutions. ASEC states: “Since July 2024, the group has also been exploiting Korean ERP software… likely developed by small-sized companies and distributed to a few Korean companies.”
The use of ERP software as an attack vector underscores the group’s strategic targeting of supply chains, particularly software with limited distribution and security visibility.
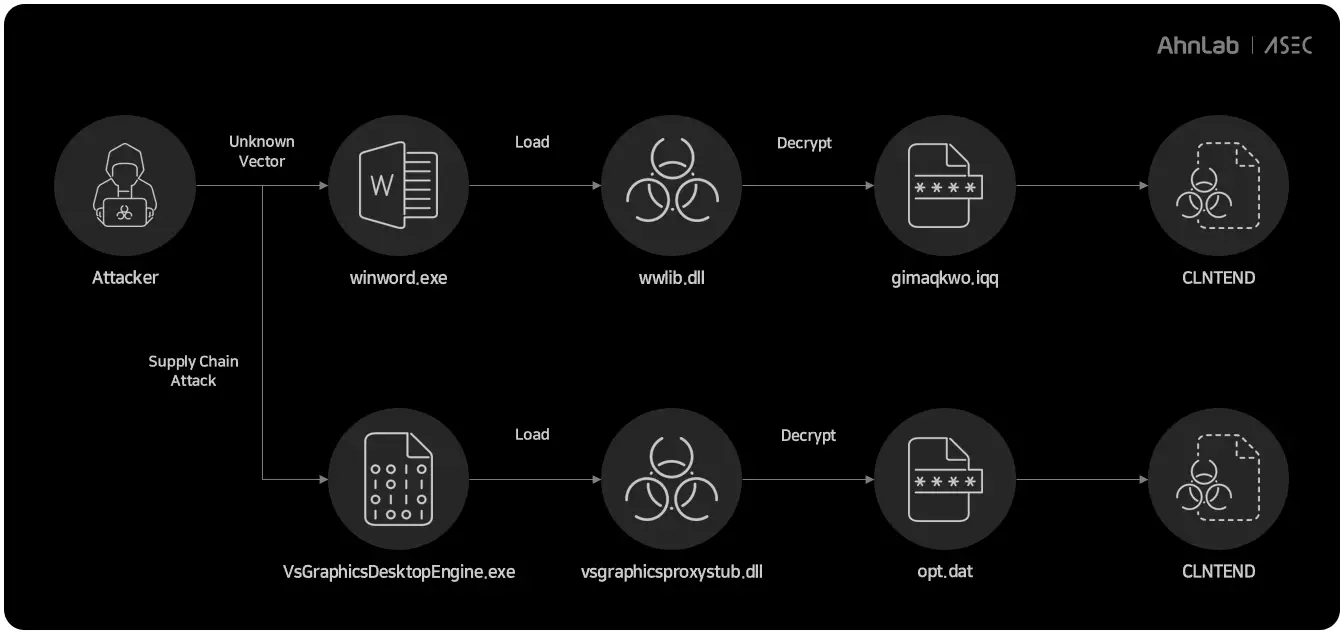
The attacks involve DLL side-loading, a well-known technique that allows malware to execute under the guise of a legitimate program. The distribution process follows two main patterns:
- Customized ERP Exploitation: Small-scale ERP developers provide software tailored to each client, giving attackers an opening to insert malware. ASEC observed that malicious versions of these ERPs were “about 4 MB in size,” compared to legitimate ones of “about 20 MB.”
- Dropper Installation: Attackers distribute versions of ERP software containing droppers that install both the ERP and the CLNTEND malware.
Malicious loaders often abuse legitimate executables such as:
- winword.exe (Microsoft Word)
- VsGraphicsDesktopEngine.exe
- rc.exe
The malware drops files like wwlib.dll and vsgraphicsproxystub.dll, enabling side-loading to decrypt and execute the CLNTEND payload in memory.
CLNTEND, described as a Remote Access Trojan (RAT), is capable of sophisticated communication with command-and-control (C2) servers. ASEC explains:
“CLNTEND is known for supporting various communication protocols such as TCP (Raw Socket, Web Socket), TLS, HTTP, HTTPS, and SMB, unlike CXCLNT.”
The malware’s encrypted data files, such as wctE5ED.tmp, are decrypted using advanced obfuscation techniques like FlsCallback, further complicating analysis for researchers.
The malware employs hardcoded paths for execution and persistence. Some observed paths include:
C:\AMD\Chipset_SoftWare\VsGraphicsDesktopEnginese.exeC:\NVIDIA\DisplayDriver\rc.exeC:\ProgramData\Microsoft OneDrive\setup\nir.exe
This highlights TIDRONE’s consistent strategy of blending malicious components into recognizable directories to evade detection.
The TIDRONE group’s pivot to targeting Korean companies via ERP exploitation demonstrates the growing sophistication of supply chain attacks. By leveraging ERP software, which is often trusted by businesses but developed with limited security oversight, the group ensures wider access to vulnerable systems.
ASEC concludes: “The recently identified attack cases involve the exploitation of ERPs that are suspected to have been created by a small development company.”
Organizations relying on ERP systems—especially those from smaller vendors—are advised to scrutinize their software supply chain, implement stricter monitoring mechanisms, and regularly update their endpoint defenses to mitigate risks posed by such advanced threats.
Related Posts:
- TIDRONE: The Unseen Cyberespionage Threat Targeting Taiwan’s Military and Satellite Industries
- CVE-2024-38856: Critical Apache OFBiz Flaw Opens Door to Unauthorized Code Execution
- Beware of “How to Fix” Button: New Phishing Emails Trick Users into Executing Malicious Commands
