
Bait document PDF document | Image: ThreatBook
The ThreatBook Research and Response Team has revealed a sophisticated campaign by APT35, also known as Magic Hound or Charming Kitten, targeting the aerospace and semiconductor industries across multiple countries, including the United States, Thailand, and the UAE. This Iranian-backed group, affiliated with the Islamic Revolutionary Guard Corps (IRGC), has a history of high-profile cyberattacks dating back to 2014.
In one of its campaigns, APT35 launched a fake recruitment site, particularly aimed at experts in drone design within the aerospace sector in Thailand. The site featured high-paying job postings, adding legitimacy to the ruse. According to ThreatBook, attackers mixed legitimate programs with malicious modules in their “authorized access” offerings: “The authorized access program provided by the site is mixed with two white and black malicious samples, among which SignedConnection.exe is a legitimate OneDrive program, and secur32.dll, Qt5Core.dll are the first and second stage malicious programs, respectively.”
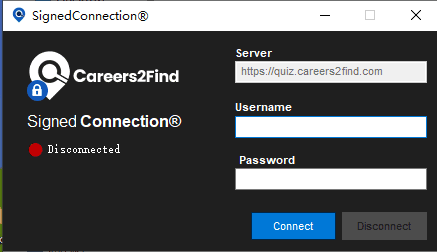
The malicious module secur32.dll, written in C#, silently loaded further stages of malware, employing obfuscation techniques such as string reconstruction to evade detection.
APT35’s methods included deploying a complex, multi-stage payload through renamed files and registry key manipulation to achieve persistence. The group also leveraged legitimate platforms like Google Cloud, GitHub, and OneDrive for command-and-control (C&C) communication.
“ThreatBook, through the analysis of related samples, IPs, and domain names, has extracted multiple related IOCs for threat intelligence detection,” reported ThreatBook.
The malware also exploited GitHub repositories and pre-configured backup C&C domains to ensure connectivity in case primary addresses were blocked. This adaptability indicates APT35’s dedication to maintaining operational resilience.
Another notable strategy involved fake VPN programs targeting semiconductor firms. The VPN installer was rigged to load a malicious DLL module named msvcp.dll, functioning as a downloader to fetch additional payloads from C&C servers hosted on legitimate cloud platforms.
“Utilize the VPN access program to load the malicious DLL module msvcp.dll, which is the same type of downloader as Qt5Core.dll,” noted ThreatBook.
APT35’s operations demonstrate its ability to exploit trust in well-known brands and tools, such as OneDrive and GitHub, to infiltrate high-value industries. The group’s extensive use of social engineering tactics, coupled with technical sophistication, highlights the need for heightened vigilance in industries handling sensitive technologies.
Related Posts:
- Iranian APT hacker organisation falsifies Israeli security companies official website to implement phishing activities
- The Dark Side of ChatGPT: Trade Secret Leaks in Samsung
- Intel Secures Nearly $8 Billion in CHIPS Act Funding to Boost US Semiconductor Production
- East Asia’s Semiconductor Industry Targeted in New Espionage Campaign
- Iranian Cyber Group Imperial Kitten Attacks Middle East