frp v0.53 releases: fast reverse proxy for exposing a local server behind a NAT or firewall to the internet
frp is a fast reverse proxy to help you expose a local server behind a NAT or firewall to the internet. Now, it supports tcp, udp, HTTP, and https protocols when requests can be forwarded by domains to backward web services.
What can I do with frp?
- Expose any http and https service behind a NAT or firewall to the internet by a server with a public IP address(Name-based Virtual Host Support).
- Expose any tcp or udp service behind a NAT or firewall to the internet by a server with the public IP address.
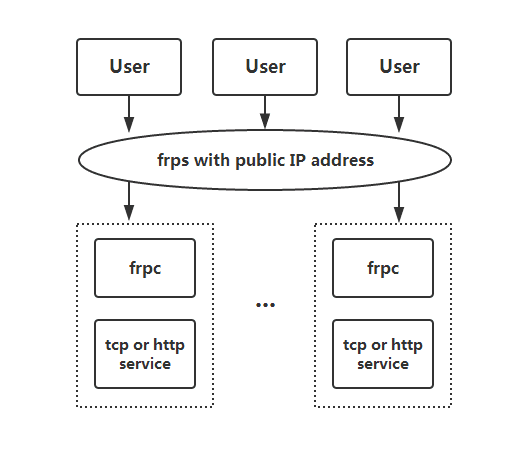
Architecture

Changelog v0.53
Features
- The new command line parameter
--strict_confighas been added to enable strict configuration validation mode. It will throw an error for unknown fields instead of ignoring them. In future versions, we will set the default value of this parameter to true to avoid misconfigurations. - Support
SSH reverse tunneling. With this feature, you can expose your local service without running frpc, only using SSH. The SSH reverse tunnel agent has many functional limitations compared to the frpc agent. The currently supported proxy types are tcp, http, https, tcpmux, and stcp. - The frpc tcpmux command line parameters have been updated to support configuring
http_userandhttp_pwd. - The frpc stcp/sudp/xtcp command line parameters have been updated to support configuring
allow_users.
Fixes
- frpc: Return code 1 when the first login attempt fails and exits.
- When auth.method is
oidcand auth.additionalScopes containsHeartBeats, if obtaining AccessToken fails, the application will be unresponsive.
Download
For some services, if the direct exposure to the public network will be a security risk.
Use a proxy of type stcp (secret tcp) to prevent anyone from having access to the service they want to penetrate, but the visitor also needs to run another frpc.
The following example will create an ssh service proxy that only has access to it.
Normal start frps.
Start frpc, forward network ssh service, configuration is as follows, do not need to specify the remote port:
# frpc.ini
[common]
server_addr = x.x.x.x
server_port = 7000[secret_ssh]
type = stcp
sk = abcdefg
local_ip = 127.0.0.1
local_port = 22
In the machine to visit this service to start another frpc, the configuration is as follows:
# frpc.ini
[common]
server_addr = x.x.x.x
server_port = 7000[secret_ssh_vistor]
type = stcp
role = vistor
server_name = secret_ssh
sk = abcdefg
bind_addr = 127.0.0.1
bind_port = 6000
Through ssh visit the network machine, assuming the username test:
ssh -oPort=6000 test@127.0.0.1
Example Usage
Firstly, download the latest programs from Release page according to your os and arch.
Put frps and frps.ini to your server with public IP.
Put frpc and frpc.ini to your server in LAN.
Access your computer in LAN by SSH
- Modify frps.ini:
# frps.ini
[common]
bind_port = 7000 - Start frps:
./frps -c ./frps.ini - Modify frpc.ini, server_addr is your frps’s server IP:# frpc.ini
[common]
server_addr = x.x.x.x
server_port = 7000[ssh]
type = tcp
local_ip = 127.0.0.1
local_port = 22
remote_port = 6000 - Start frpc:
./frpc -c ./frpc.ini - Connect to the server in LAN by ssh assuming that username is tested:
ssh -oPort=6000 test@x.x.x.x
More info and tutorial, visit here.
Copyright 2017 fatedier






