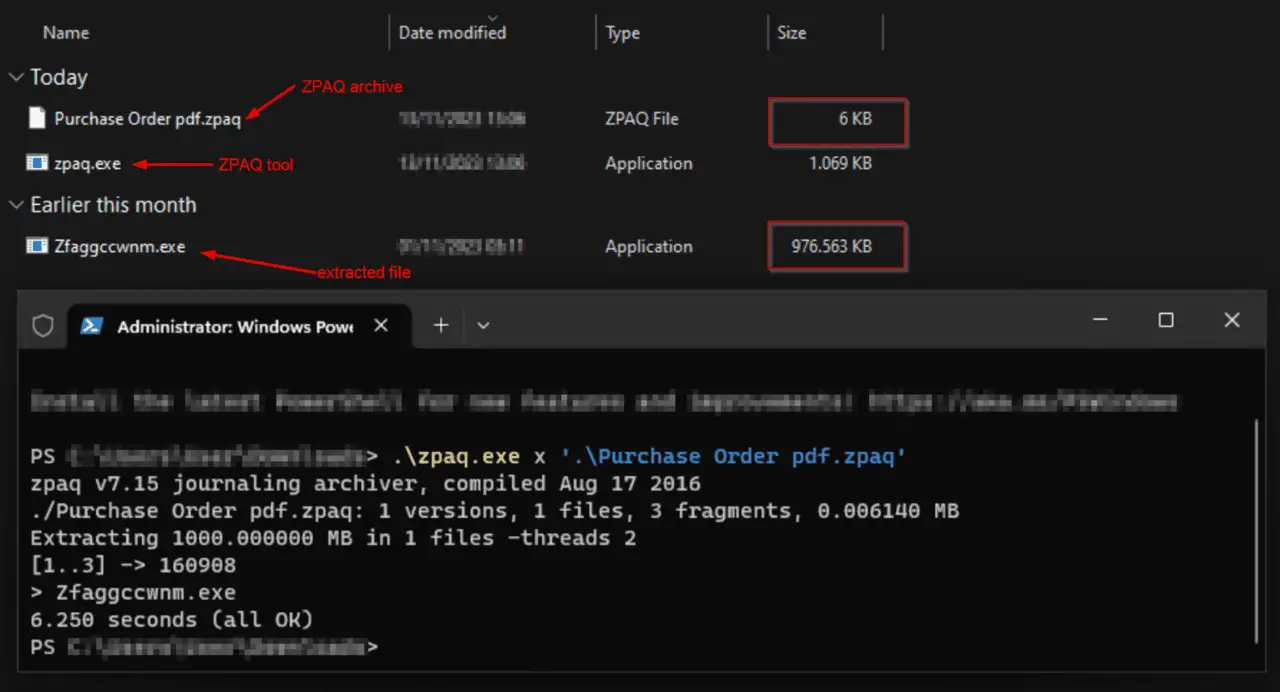
Extraction of the .NET executable with ZPAQ cmd tool and comparison of size. | Image: gdatasoftware
G Data has uncovered a novel variant of the malicious software Agent Tesla, delivered via a bait file in the ZPAQ compression format, aimed at harvesting data from several email clients and nearly 40 web browsers.
G Data noted that ZPAQ offers superior compression ratios and a logging function compared to conventional formats like ZIP and RAR, but its drawback lies in limited support from software applications.
First appearing in 2014, Agent Tesla is a keylogger and a Remote Access Trojan (RAT), crafted in .NET. Implemented as part of a ‘Malware-as-a-Service’ (MaaS) model, Agent Tesla is typically employed to facilitate remote access to compromised systems and to further download ransomware.

In the discovered campaigns, Agent Tesla is disseminated through phishing emails. In some instances, it exploited the CVE-2017-11882 vulnerability (CVSS: 7.8) in the Microsoft Office Equation Editor. The attack commences with an email bearing a ZPAQ file attachment, masquerading as a PDF document. Opening the file triggers the unpacking of an inflated .NET executable, artificially enlarged to 1 GB to circumvent standard security measures.
G Data explains that the primary function of the executable is to download and decrypt a .wav file, aiming to disguise malicious activity as regular traffic and thus impede its detection by network security solutions. The ultimate objective of the attack is to infect the device with Agent Tesla, concealed behind .NET Reactor, a legitimate software for code protection. Control is exercised via Telegram.
This latest development in the attacks signifies the perpetrators’ quest for novel delivery methods of malicious software, utilizing unconventional file formats. Such a trend demands heightened vigilance from users against suspicious emails and the continual updating of their systems. G Data remarks that the use of ZPAQ in this context raises questions, suggesting that the attackers are either targeting a specific group of technically savvy individuals or experimenting with new methods of spreading malware to bypass security systems.