GadgetProbe
Description
You just found a Java deserialization bug, you ran all your ysoserial payloads, and…. you got nothing. What now? How can you debug or build a gadget chain if you’re totally blind?
Introducing GadgetProbe, a tool that shines a light on remote classpaths and raises bug severity for all!
It takes a wordlist of Java classes, outputs serialized DNS callback objects and reports what’s lurking in the remote classpath.
Burp Extension Usage
The Burp extension automatically integrates with Burp Collaborator to handle DNS callbacks. The extension also includes signatures and an analyzer to identify library versions of popular sources for gadgets.
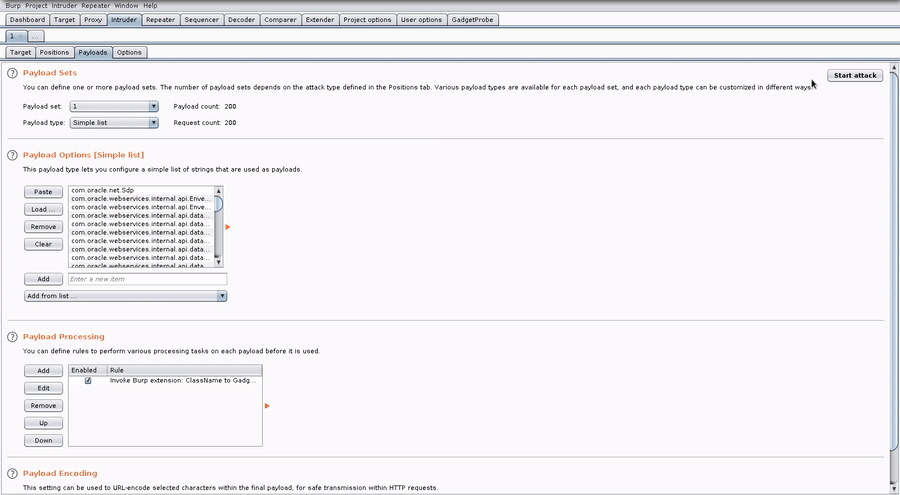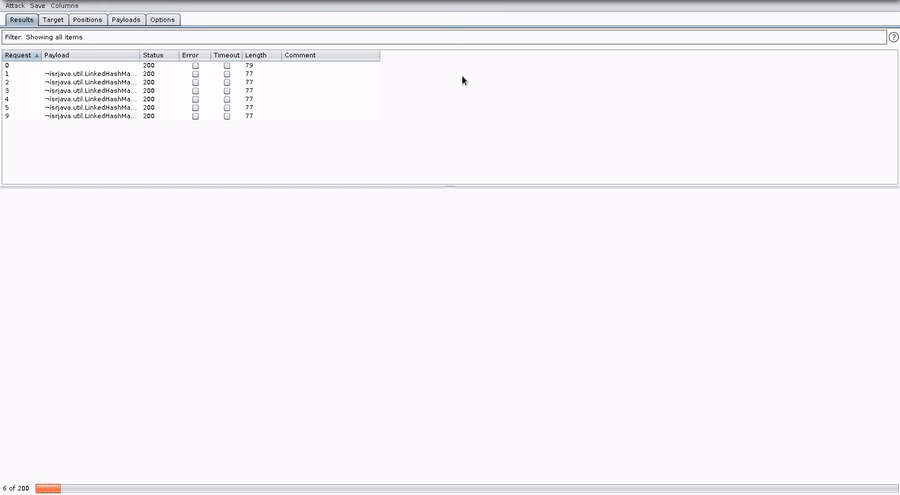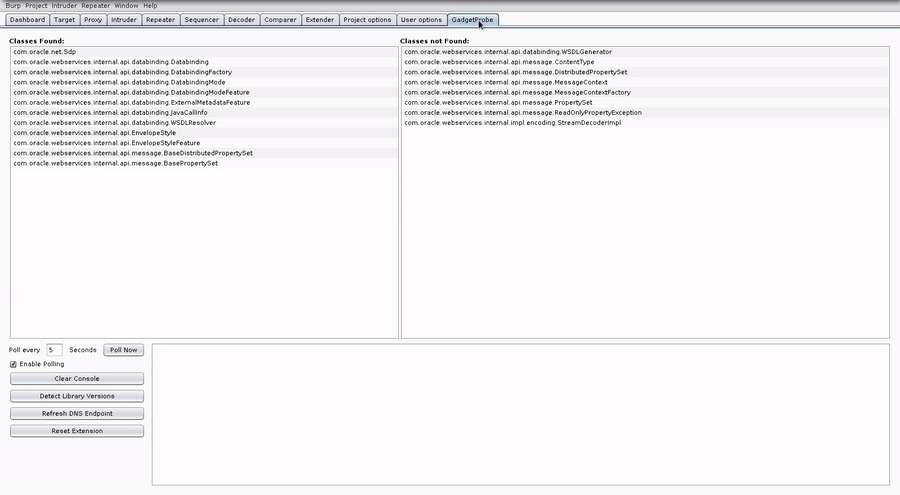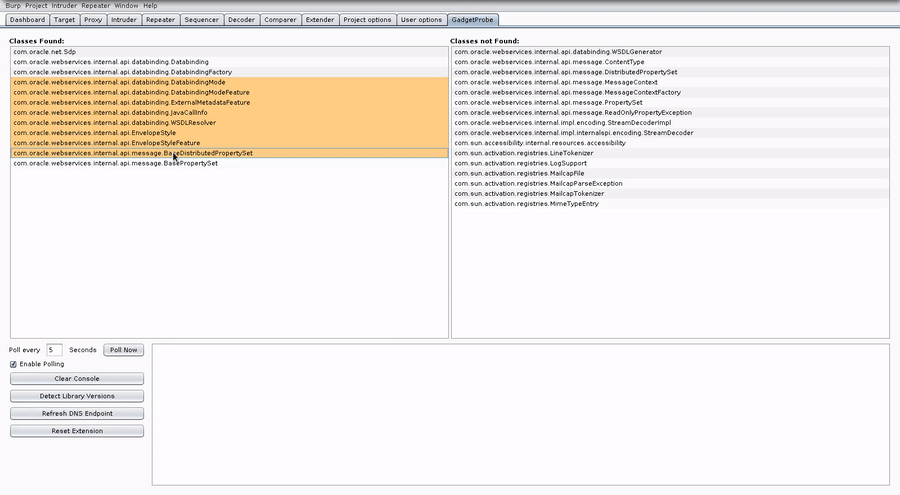
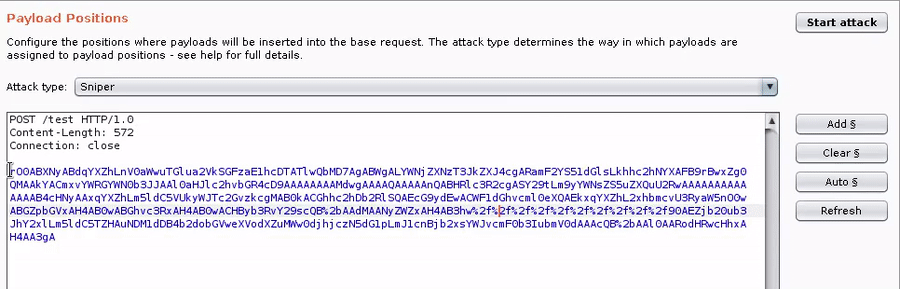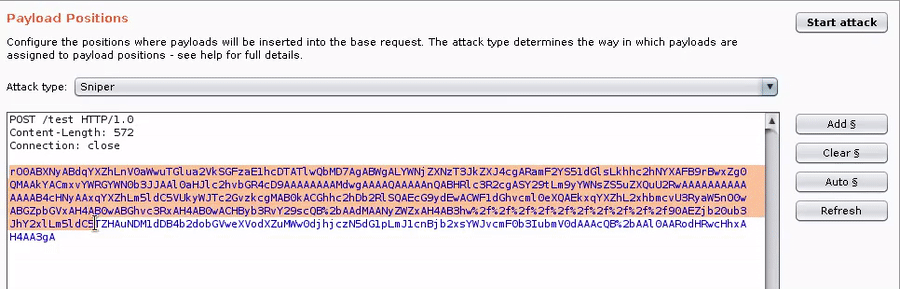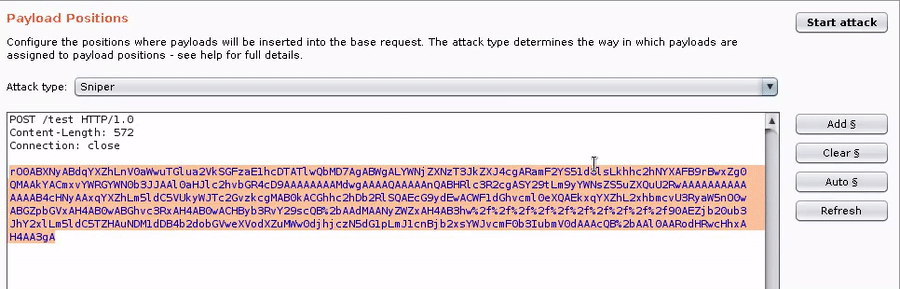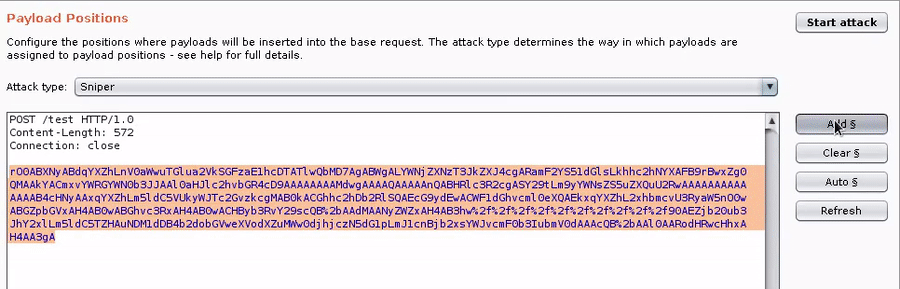
After loading the Burp extension:
2. Add a list of Java classes (see included wordlists)
3. Add the GadgetProbe payload processor, and any other required processors in your chain (e.g., Base64 encode).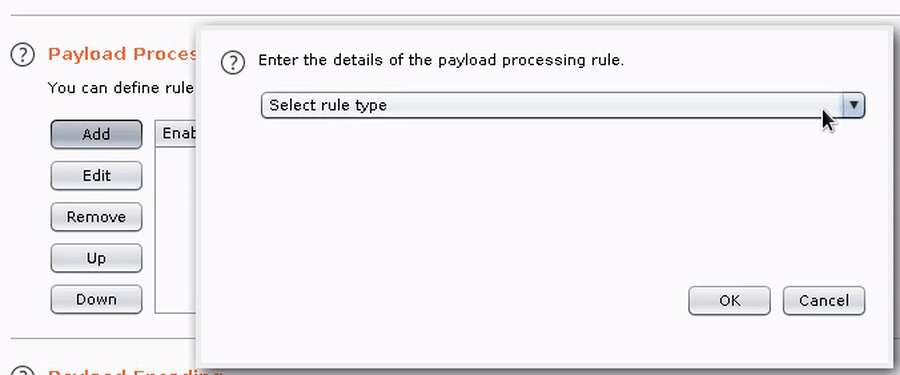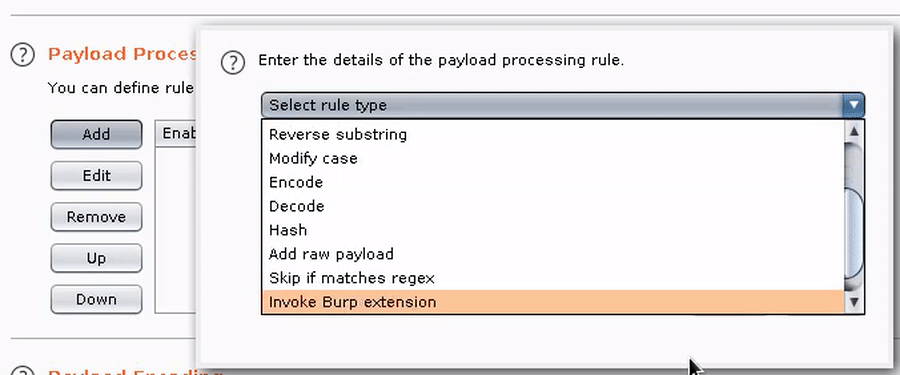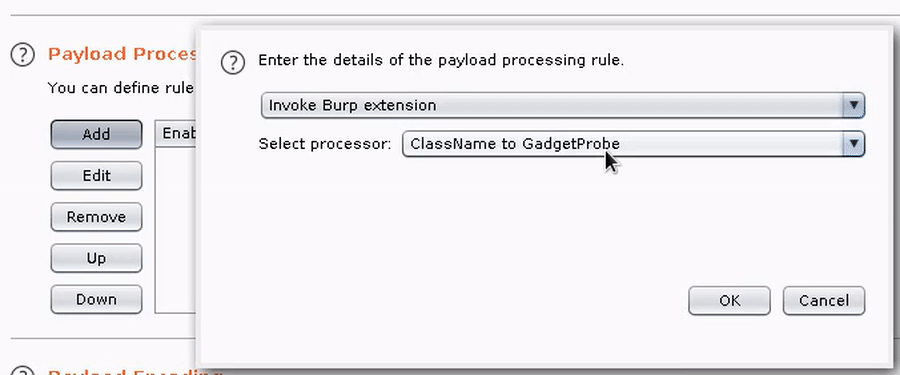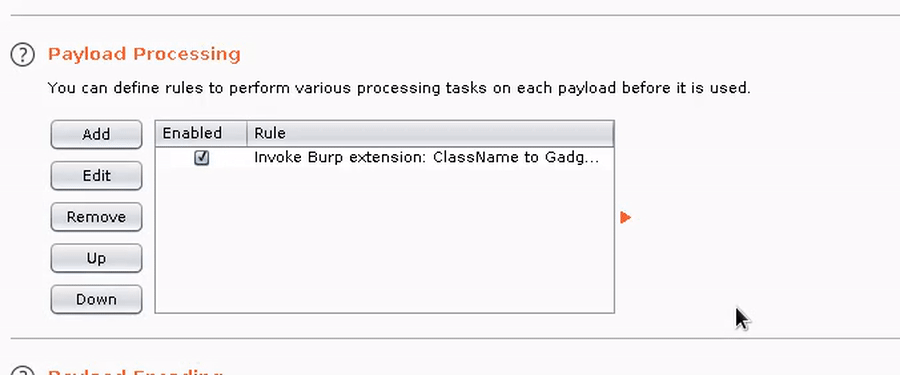
4. Run the intruder attack and watch the results come back in the GadgetProbe Burp Tab.
GadgetProbe Java Library Usage
It can also be used as a Java library or CLI for specialized attacks.
Download
Copyright (c) 2020 BishopFox