ggshield v1.21 releases: Detect secret in source code, scan your repo for leaks

GitGuardian Shield: protect your secrets with GitGuardian
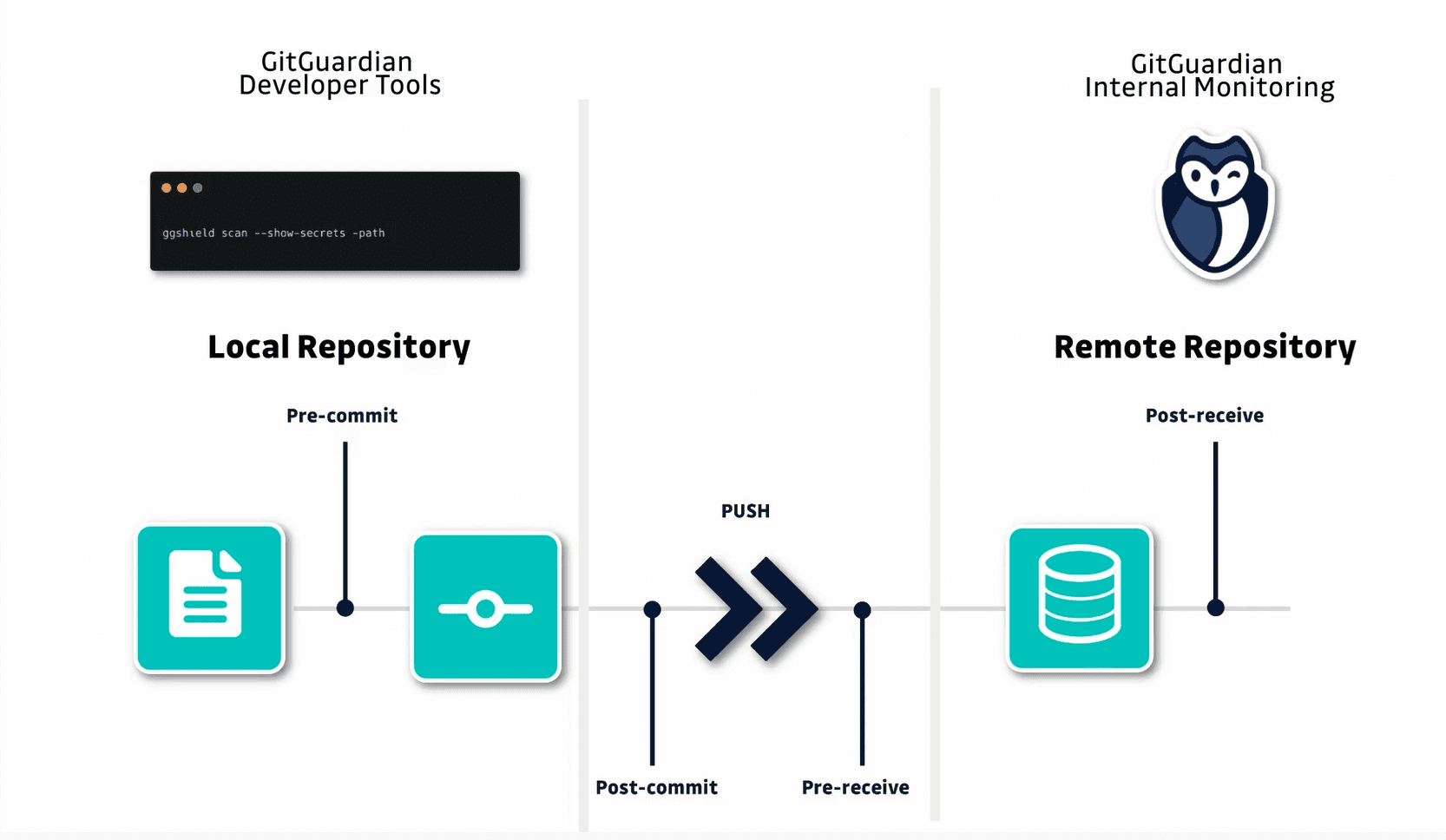
GitGuardian shield (ggshield) is a CLI application that runs in your local environment or in a CI environment to help you detect more than 300 types of secrets, as well as other potential security vulnerabilities or policy breaks.
GitGuardian shield uses our public API through py-gitguardian to scan and detect potential secrets on files and other text content.
Only metadata such as call time, request size, and scan mode is stored from scans using GitGuardian shield, therefore secrets and policy breaks incidents will not be displayed on your dashboard and your files and secrets won’t be stored.
You’ll need an API Key from GitGuardian to use ggshield.
Currently supported integrations
- Azure Pipelines
- Bitbucket Pipelines
- Circle CI Orbs
- Docker
- Drone
- GitHub Actions
- GitLab
- Jenkins
- Pre-commit hooks
- Pre-push hooks
- Pre-receive hooks
- Travis CI
Changelog v1.21
Added
- Support for new options in gitguardian config file. IaC
ignored-pathsandignored_policiescan now be defined as objects withcommentanduntilproperties. If anuntildate is provided, the path/policy is only ignored up until this date. The old format is still supported. Check.gitguardian.example.yamlfor a sample.
Changed
ggshield iac scan diff --jsonoutput was changed.added_vulns,persisting_vulnsandremoved_vulnswere renamed asnew,unchangedanddeleted. They also were moved into aentities_with_incidentssimilarly to the scan all JSON output.
Fixed
- When a git command fails, its output is now always correctly logged.
Install & Use
Copyright (c) 2019 GitGuardian