Git-Hunter
A tool to monitor possible key-leaks on Github, made by Ruby.
Introduction
If you come from a company or an organization, and you are a headache about your employee uploading some sensitive code to their own GitHub, e.g. AWS keys, DB password, company project code, you are in the right place. Git-Hunter is aimed to establish a monitor system to inform you at the first time once those bad things happen.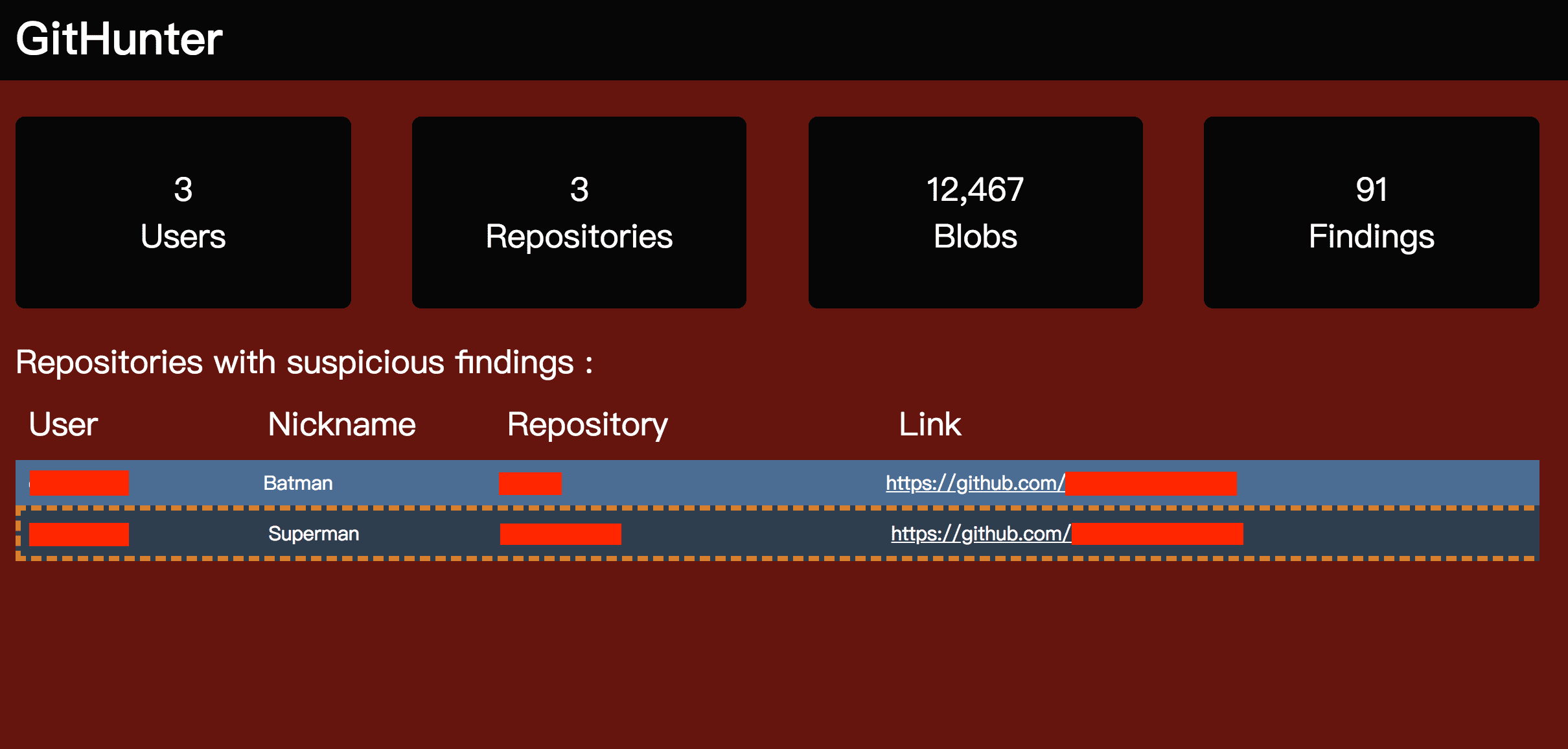
Installation
git clone https://github.com/Interfish/Git-Hunter.git
bundle install
Usage
Git-Hunter main functions:
1. Monitor Specified Github users.
First:
and add some Github users you wish to be monitored, one line each, for example:
What’s a nickname? If you wish to set relation between GitHub user and some name in your company’s personnel system, e.g. employee’s real name, employee’s job number, it could be convenient. No nickname is totally fine. Just leave it blank.
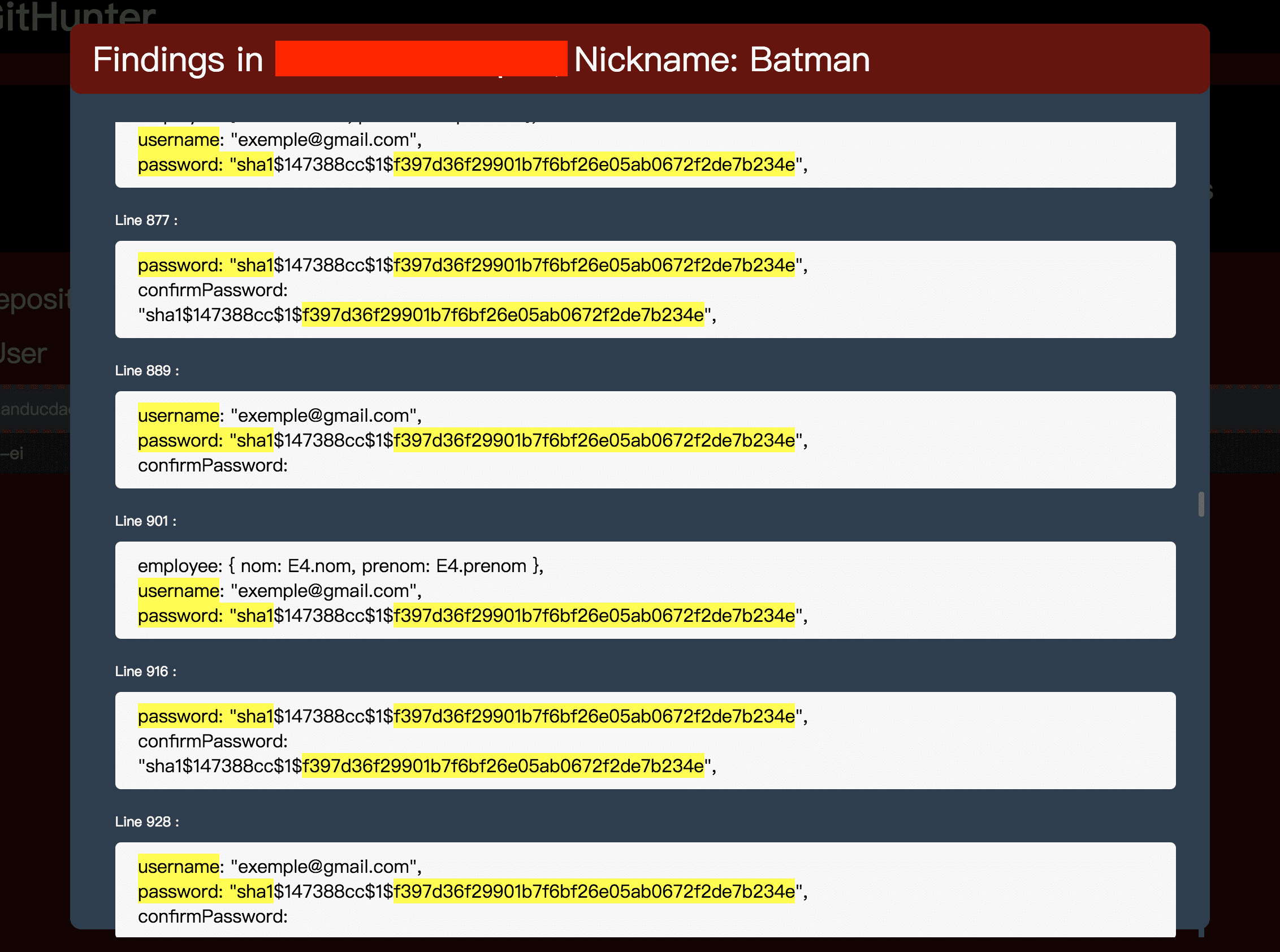
Then you may like to add some self-defined config. Git-Hunter will try to find two things in repos – sensitive words and possible key-leaks, and they are all in config.rb.
Config for key-leaks is in KEY_WORDS and it’s common to all users, so you don’t need to change it for the first time.
SENSITIVE_WORDS varies a lot. If you are from Google, some of your company’s project is named ‘abc’, ‘def’ and ‘ghi’, and some of your company’s domain are ‘dada.com’, ‘pope.com’, you can add following items:
Git-Hunter will use a regular expression to match these words. Some try to think of some highly representative words you care about.
One more thing, don’t forget to add Github personal access token, it’s necessary for Git-Hunter to work:
Ok! Time to Run, just:
$ ruby ./git_hunter.rb run
Git-Hunter will automatically clone and analyze all users’ repositories as listed in user_list.txt. When it finishes, it will generate an HTML report and highlight the findings, if there is any.
If you wish to analyze only one user, just:
$ ruby ./git_hunter.rb run user Interfish [some_nickname]
or
$ ruby ./git_hunter.rn run user https://github.com/Interfish [some_nickname]
# nickname is optional
One repo:
$ ruby ./git_hunter.rb run user Interfish git-hunter [some_nickname]
or
$ ruby ./git_hunter.rb run user https://github.com/Interfish/git-hunter [some_nickname]
# nickname is optional
2. Keep findings and ignore false positive
All findings are stored in a local SQLite database. Of course, there are lots of ‘false positive’. So CLI provide ways to mark them as false positive and they will not show up in your next generated HTML report.
For example, if you have already watched the HTML report of https://github.com/Interfish/git-hunter and you are very sure it does not contain sensitive words and possible key leaks, you can:
$ ruby ./git_hunter.rb mark repo Interfish git-hunter
Or, if you are sure all findings of Interfish are false positive:
$ ruby ./git_hunter.rb mark user Interfish
more, if all findings in DB are false positive:
$ ruby ./git_hunter.rn mark all
3.Generate report
You can manually generate an HTML report. It will fetch in-DB findings which have not been marked as false positive. All report will be located in dir reports.
Generate for a single repo:
$ ruby ./git_hunter.rb report repo Interfish git_hunter
For a single user
$ ruby ./git_hunter.rb report user Interfish
For all findings in DB:
$ ruby ./git_hunter.rb report all

More…
Copyright (c) 2018 Interfish
Source: https://github.com/Interfish/