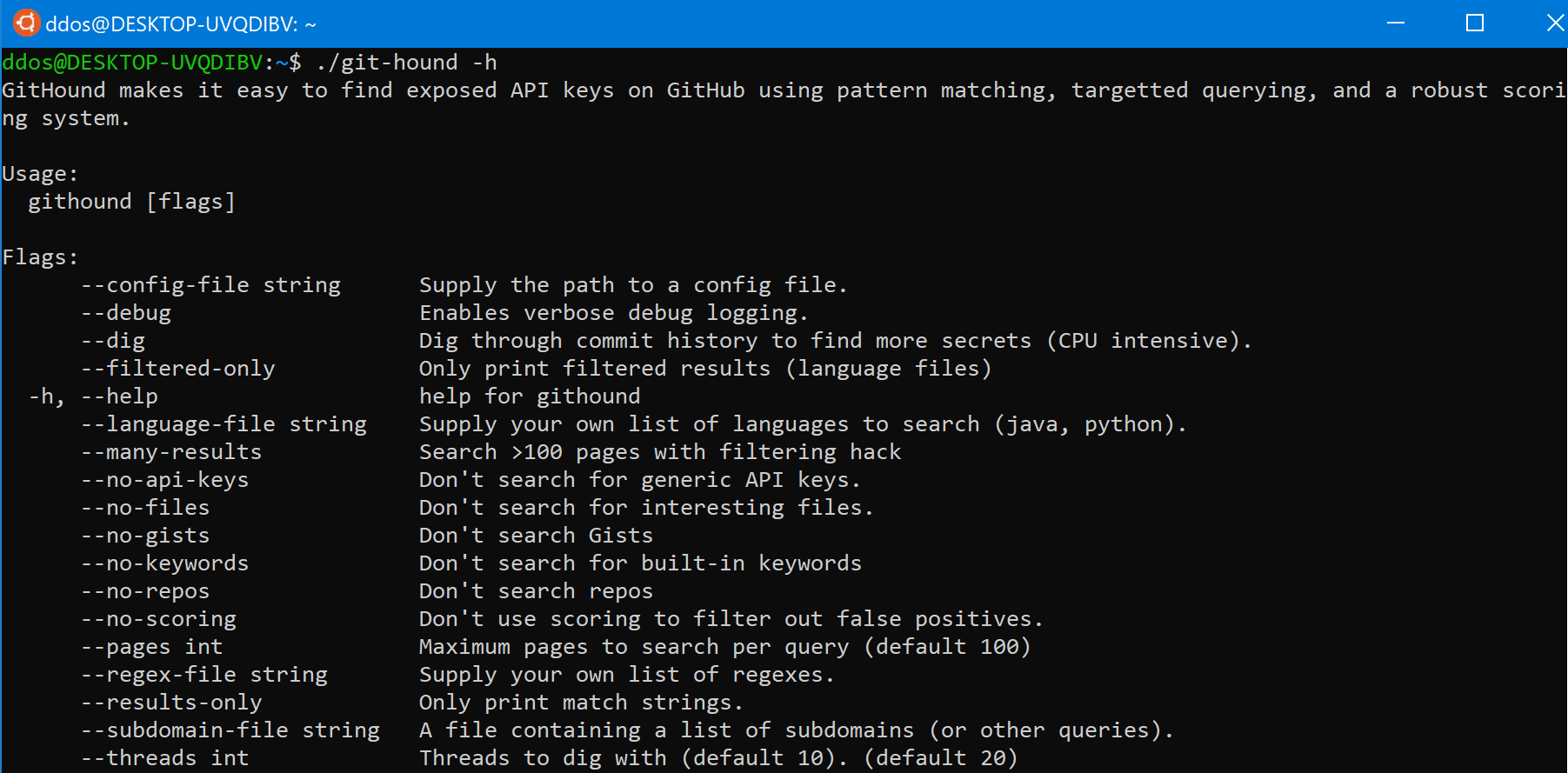
GitHound
GitHound pinpoints exposed API keys on GitHub using pattern matching, commit history searching, and a unique result scoring system. It has earned me over $4000 applied to Bug Bounty research. Corporate and Bug Bounty Hunter use cases are outlined below.
Features
- GitHub/Gist code searching. This enables GitHound to locate sensitive information exposed across all of GitHub, uploaded by any user.
- Generic API key detection using pattern matching, context, and Shannon entropy.
- Commit history digging to find improperly deleted sensitive information (for repositories with <6 stars)..
- Unique scoring system to emphasize confident results, filter out common false positives, and to optimize intensive repo digging.
- Options to build GitHound into your workflow, like custom regexes and results-only output mode.
Use cases
Corporate: Searching for exposed customer API keys
Knowing the pattern for a specific service’s API keys enables you to search GitHub for these keys. You can then pipe matches for your custom key regex into your own script to test the API key against the service and to identify the at-risk account.
echo “api.halcorp.biz” | githound –dig –many-results –regex-file halcorp-api-regexes.txt –results-only | python halapitester.py
For detecting future API key leaks, GitHub offers Push Token Scanning to immediately detect API keys as they are posted.
Bug Bounty Hunters: Searching for leaked employee API tokens
My primary use for GitHound is for finding sensitive information for Bug Bounty programs. For high-profile targets, the –many-results hack and –languages flag are useful for scraping >100 pages of results.
echo “uberinternal.com” | githound –dig –many-results –languages common-languages.txt –threads 100
Changelog v1.7.1
- 9f753b8 fix go error
- 8b0db00 Merge branch ‘main’ of https://github.com/tillson/git-hound
- b8f373c Fix bug with json output and regex
- 45f7695 Update README.md
Download && Use
Copyright (c) 2019 Tillson Galloway