gitoops
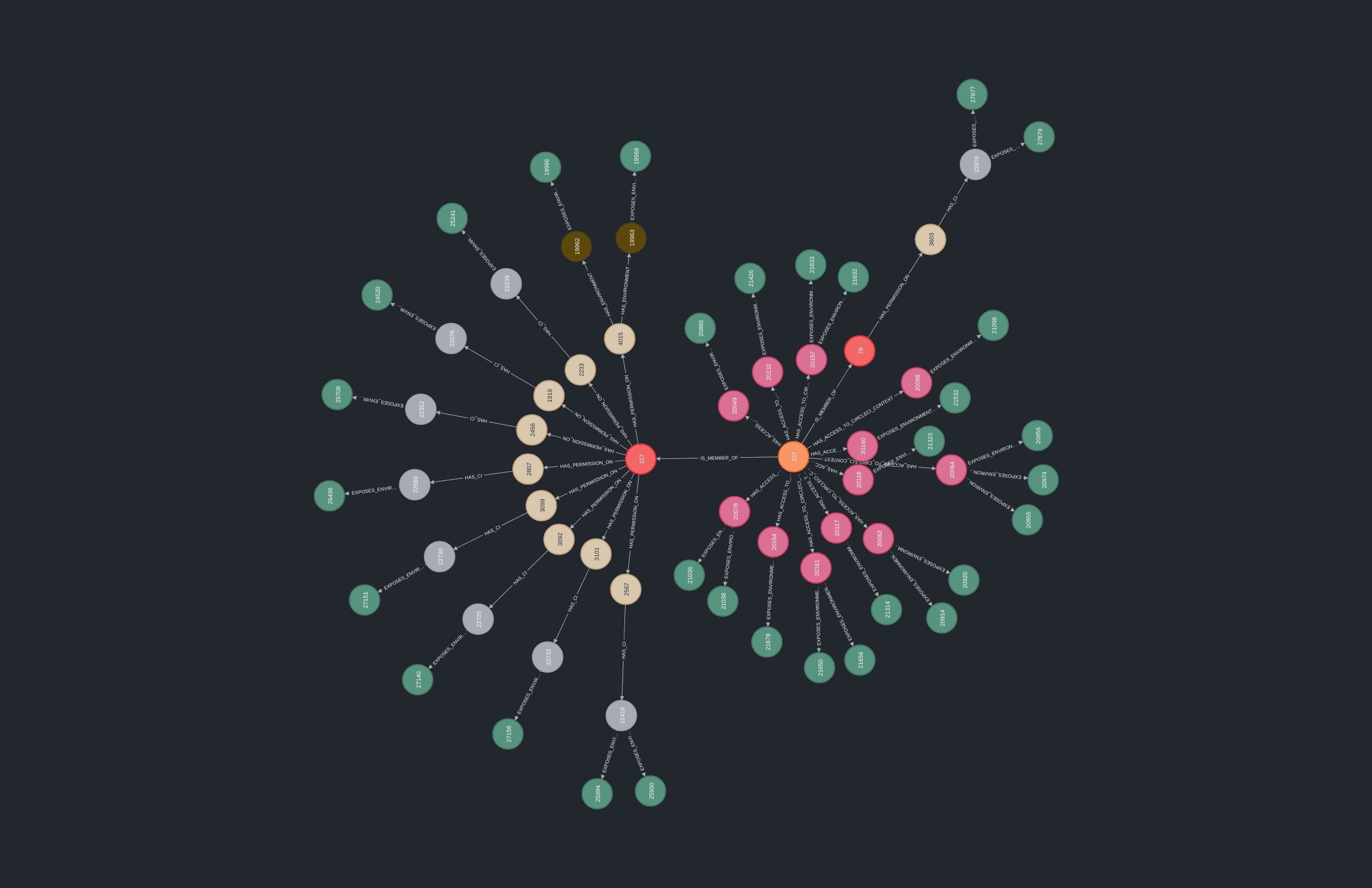
GitOops is a tool to help attackers and defenders identify lateral movement and privilege escalation paths in GitHub organizations by abusing CI/CD pipelines and GitHub access controls.
It works by mapping relationships between a GitHub organization and environment variables in its CI/CD systems. It’ll use any Bolt-compatible graph database as backend, so you can query your attack paths with openCypher:
MATCH p=(:User{login:”alice”})-[*..5]->(v:EnvironmentVariable)
WHERE v.name =~ “.*SECRET.*”
RETURN p

In addition to mapping relationships between your users, teams, and repositories, GitOops maps relationships between those and environment variables in your CI/CD systems.
The following CI/CD systems are currently supported:
- GitHub Actions
- CircleCI
On top of this, GitOops ingests CI/CD configuration files from repositories for other popular CI/CD systems, enabling less refined queries on those.
Finally, GitOops will also map webhooks and status checks from commits to a repository’s pull requests and default branch. These allow you to find integrations that are typically configured server-side (e.g. AWS CodeBuild).
Install & Use
Copyright (c) 2021 OVO Technology