
Cisco has issued a critical warning about a widespread password spraying campaign targeting Remote Access VPN (RAVPN) systems used by businesses worldwide. This surge in attacks aims to overwhelm VPN logins with common passwords, potentially locking out legitimate users and disrupting remote work.

What is Password Spraying?
- Low and Slow: Unlike brute force attacks that focus on single accounts, password spraying targets many accounts with a list of common passwords. This slow, stealthy approach helps evade many detection systems.
- Lockout Danger: Successful attempts can flood systems with failed logins, triggering account lockouts and creating a denial of service for legitimate users.
Key Cisco Warning Signs
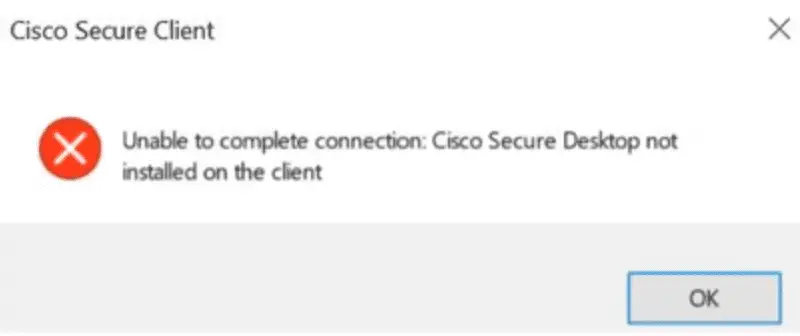
- VPN Connection Failures: Users may be unable to connect to their VPN, receiving errors like “Cisco Secure Desktop not installed” even when it is.
- Authentication Log Spike: System administrators should check the ASA/FTD syslog for unusual spikes in denied login attempts.
It’s Not Just Cisco
Security researchers emphasize that the password spraying campaign impacts various VPN providers, not just Cisco. Businesses relying on remote access need to be on high alert. The ramifications of these attacks extend beyond mere unauthorized access; they have the potential to lock accounts and induce Denial of Service (DoS)-like conditions, disrupting the seamless flow of digital operations and compromising the integrity of secure communications.
What You Can Do
Cisco recommends several urgent measures:
- Enable Robust Logging: Detailed logs are essential for investigating and mitigating the attacks. Log to a remote syslog server for better security.
- Rethink Default VPN Settings: Secure or disable default VPN connection profiles to block attacks that may exploit common settings.
- Consider TCP Shun (Manual): While requiring manual intervention, this function can block malicious IP addresses.
- Control-Plane ACLs: Implement Access Control Lists to filter out unauthorized IP addresses attempting to connect to the VPN.
- Upgrade to Certificate Authentication: Certificates offer much stronger protection than simple passwords.
The Bigger Picture
This campaign highlights the ongoing threat to remote access solutions, a cornerstone of modern business operations. Organizations must prioritize strong authentication, vigilant monitoring, and robust incident response plans to stay ahead of evolving attack methods.