
Global Socket
Moving data from here to there. Securely, Fast, and through NAT/Firewalls.
Global Socket allows two users behind NAT/Firewall to establish a TCP connection with each other. Securely.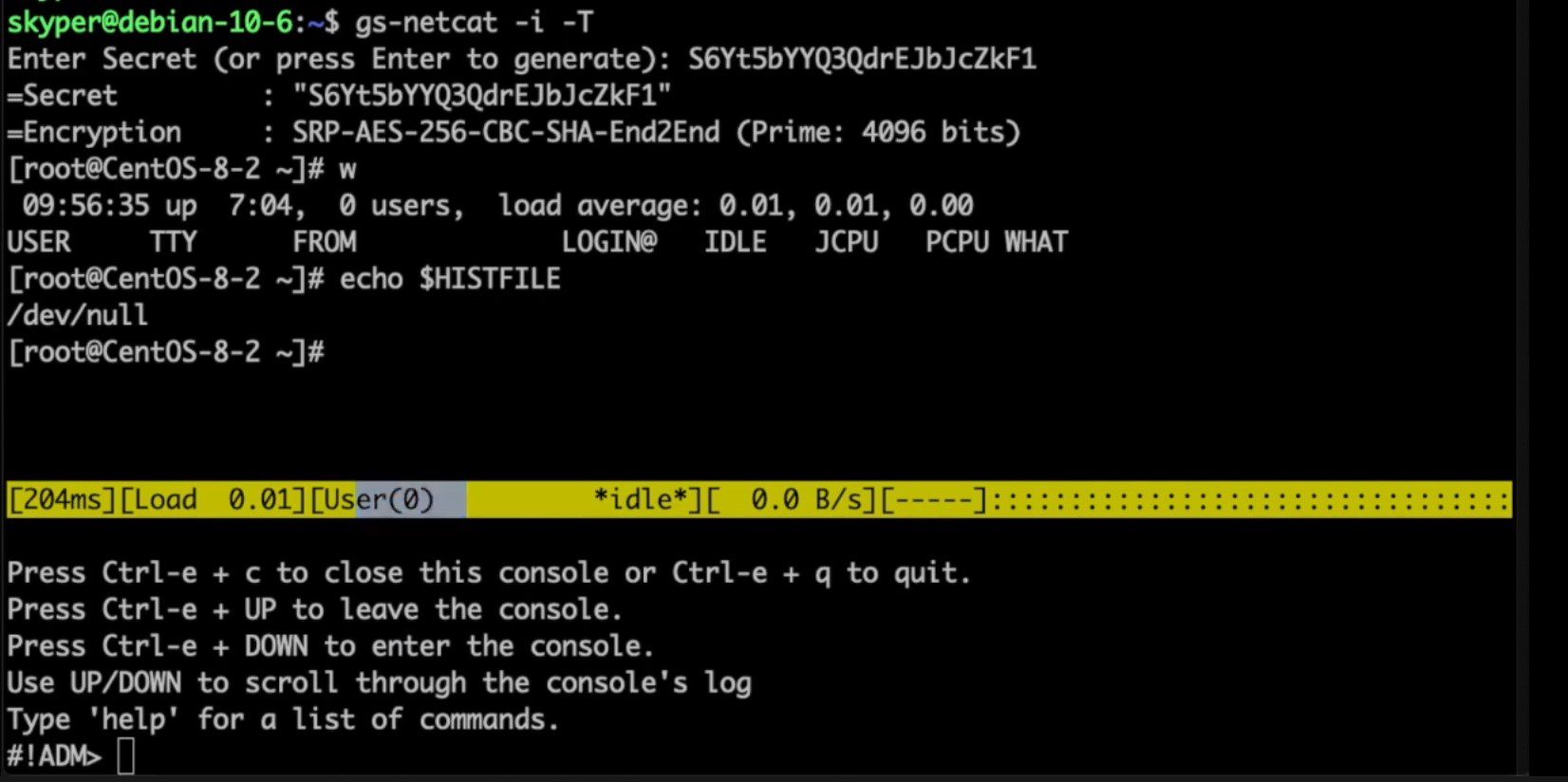
Features:
- Uses the Global Socket Relay Network to connect TCP pipes
- End-2-End encryption (using OpenSSL’s SRP / RFC 5054)
- AES-256 & key exchange using 4096-bit Prime
- No PKI required.
- Perfect Forward Secrecy
- TOR support (optional)
Abandon the thought of IP Addresses and Port Numbers. Instead start thinking that two programs should be able to communicate with each other as long as they know the same secret (rather than each other’s IP Address and Port Number). The Global Socket library facilitates this: It locally derives temporary session keys and IDs and connects two programs through the Global Socket Relay Network (GSRN) regardless and independent of the local IP Address or geographical location. Once connected the library then negotiates a secure TLS connection(End-2-End). The secret never leaves your workstation. The GSRN sees only the encrypted traffic.
The GSRN is a free cloud service and is free to use by anyone.
The Global Socket Toolkit comes with a set of tools:
- gsocket – Makes an existing program (behind firewall or NAT) accessible from anywhere in the world. It does so by analyzing the program and replacing the IP-Layer with its own Gsocket-Layer. A client connection to a hostname ending in ‘*.gsocket’ then gets automatically redirected (via the GSRN) to this program.
- gs-netcat – Netcat on steroids. Turn gs-netcat into an AES-256 encrypted reverse backdoor via TOR (optional) with a true PTY/interactive command shell (
gs-netcat -s MySecret -i), integrated file-transfer, spawn a Socks4/4a/5 proxy or forward TCP connections or give somebody temporary shell access. - gs-sftp – sftp server & client between two firewalled workstations (
gs-sftp -s MySecret) - gs-mount – Access and mount a remote file system (
gs-mount -s MySecret ~/mnt/warez) - blitz – Copy data from workstation to workstation (
blitz -s MySecret /usr/share/*) - …many more examples and tools.
Crypto / Security Mumble Jumble
- The security is end-2-end. This means from User-2-User (and not just to the Relay Network). The Relay Network relays only (encrypted) data to and from the Users.
- The session key is 256 bit and ephemeral. It is freshly generated for every session and generated randomly (and is not based on the password).
- The password can be ‘weak’ without weakening the security of the session. A brute force attack against a weak password requires a new TCP connection for every guess.
- Do not use stupid passwords like ‘password123’. Malice might pick the same (stupid) password by chance and connect. If in doubt use gs-netcat -g to generate a strong one. Alice’s and Bob’s password should at least be strong enough so that Malice can not guess it by chance while Alice is waiting for Bob to connect.
- If Alice shares the same password with Bob and Charlie and either one of them connects then Alice can not tell if it is Bob or Charlie who connected.
- If Alice shares the same password with Bob and Malice and Alice stops listening for a connection then Malice could start to listen for the connection instead. Bob (when opening a new connection) could not tell if he is connecting to Alice or to Malice. Use -a <token> if you worry about this. TL;DR: When sharing the same password with a group larger than 2 then it is assumed that everyone in that group plays nicely. Otherwise use SSH over the GS/TLS connection.
- SRP has Perfect Forward Secrecy. This means that past sessions can not be decrypted even if the password becomes known.
- I did not invent SRP. It’s part of OpenSSL :>
Changelog v1.4.41
- * Transparent proxy detection
- * muslcc localtime() bug work around
Install & Use
Copyright (C) 2002-2020 skyper@thc.org