goddi: dumps Active Directory domain information
goddi – Go dump domain info
dumps Active Directory domain information
Functionality
StartTLS and TLS (tls.Client func) connections supported. Connections over TLS are the default. All output goes to CSVs and is created in /csv/ in the current working directory. Dumps:
- Domain users. Also searches Description for keywords and prints to a seperate csv ex. “Password” was found in the domain user description.
- Users in privileged user groups (DA, EA, FA).
- Users with passwords not set to expire.
- User accounts that have been locked or disabled.
- Machine accounts with passwords older than 45 days.
- Domain Computers.
- Domain Controllers.
- Sites and Subnets.
- SPNs and includes csv flag if domain admin (a flag to note SPNs that are DAs in the SPN CSV output).
- Trusted domain relationships.
- Domain Groups.
- Domain OUs.
- Domain Account Policy.
- Domain delegation users.
- Domain GPOs.
- Domain FSMO roles.
- LAPS passwords.
- GPP passwords. On Windows, defaults to mapping Q. If used, will try another mapping until success R, S, etc… On Linux, /mnt/goddi is used.
Download
Run
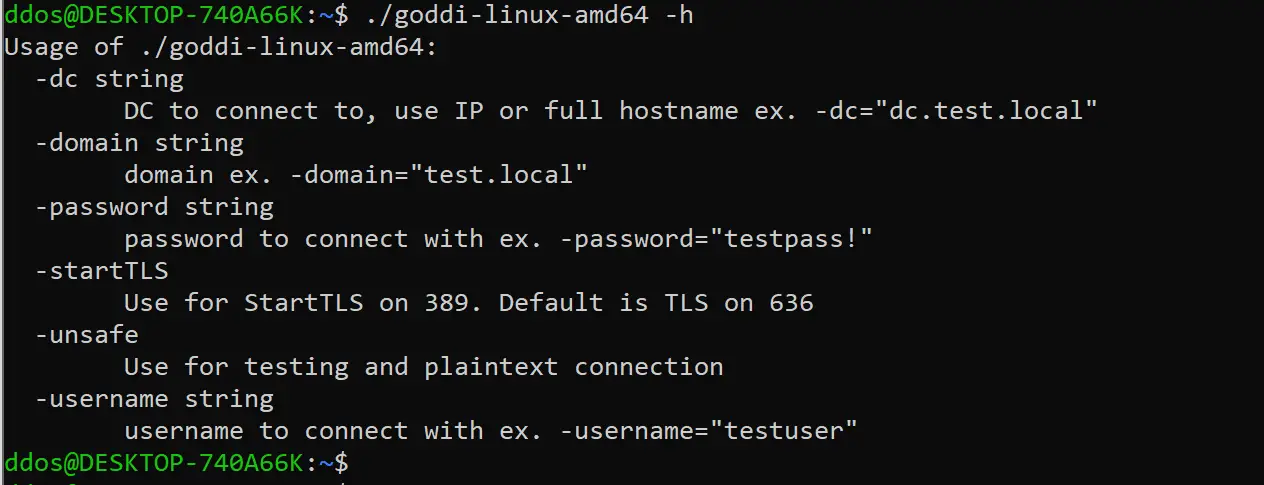
When run, will default to using TLS (tls.Client method) over 636. On Linux, make sure to run with sudo
- username: Target user. Required parameter.
- password: Target user’s password. Required parameter.
- domain: Full domain name. Required parameter.
- dc: DC to target. Can be either an IP or full hostname. Required parameter.
- startTLS: Use to StartTLS over 389.
- unsafe: Use for a plaintext connection.
Copyright (c) 2018, NetSPI
All rights reserved.
Source: https://github.com/NetSPI/