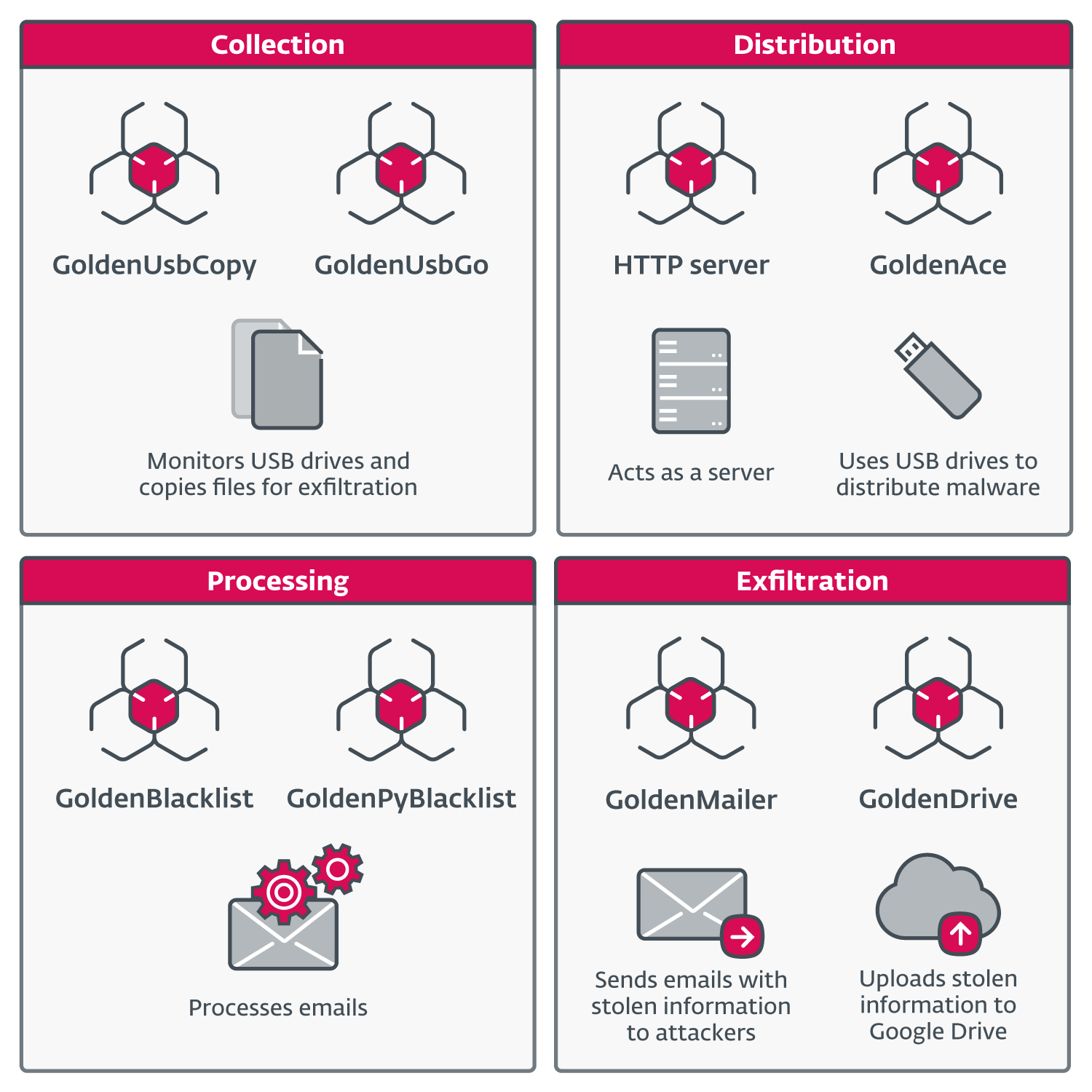
Components in GoldenJackal’s latest toolset | Image: ESET
A new report by Matías Porolli, a malware researcher at ESET, has revealed a series of cyberespionage campaigns executed by the elusive Advanced Persistent Threat (APT) group known as GoldenJackal. Targeting governmental entities across Europe, the Middle East, and South Asia, this threat actor has developed a unique ability to breach even air-gapped systems—networks deliberately isolated from the internet to secure highly sensitive data.
GoldenJackal, first reported by Kaspersky in 2023, has been active since at least 2019. The group is notorious for targeting government and diplomatic organizations. Their toolset, primarily written in C#, includes several implants such as JackalControl, JackalSteal, and JackalWorm, all designed to facilitate espionage activities. Most notably, they have designed not one, but two toolsets capable of compromising air-gapped systems.
In attacks spanning from May 2022 to March 2024, GoldenJackal breached a European governmental organization’s air-gapped systems. The tools they used, though previously undocumented, were linked to GoldenJackal due to their similarities with known malicious programs.
Air-gapped networks are often deployed to protect the most critical systems, such as those running power grids or processing election data. According to the report, “compromising an air-gapped network is much more resource-intensive than breaching an internet-connected system,” meaning that only the most sophisticated groups, such as nation-state actors, can pull it off.
GoldenJackal, however, has achieved this feat not once but twice, indicating its advanced capabilities. In one instance, the group used a custom toolset that included GoldenDealer, a program that delivers executables via USB drives, and GoldenHowl, a modular backdoor that facilitates data exfiltration from these isolated systems. Another tool, GoldenRobo, was designed to collect and steal files from the compromised systems.
In their most recent campaigns, GoldenJackal has shifted towards a highly modular approach, reflecting their adaptability. The malicious components they use have been designed for different tasks. Some modules focus on exfiltrating sensitive data, while others deliver files or updates to various hosts in the network. The group has shown its capacity to leverage specific machines within the network to act as local servers, distributing files or instructions to other compromised devices.
GoldenUsbCopy, for instance, monitors the insertion of USB drives and copies files of interest to an encrypted container on the system for later exfiltration. This tool exemplifies the group’s ability to utilize removable drives to bridge the gap between air-gapped systems and internet-connected devices.
While GoldenJackal’s toolset and tactics have been scrutinized, the report stops short of definitively attributing their activities to a specific nation-state. However, a curious connection exists between the group’s Command-and-Control (C&C) protocol, referred to as “transport_http,” and techniques used by Russian-speaking APT groups like Turla and MoustachedBouncer. Despite this clue, the report concludes that the origin of GoldenJackal remains unclear.
GoldenJackal represents a sophisticated and persistent threat to government entities. Their ability to compromise air-gapped systems, adapt their toolsets, and operate across a wide geographic area makes them a dangerous adversary. As Matías Porolli of ESET concludes, “Managing to deploy two separate toolsets for breaching air-gapped networks in only five years shows that GoldenJackal is a sophisticated threat actor aware of network segmentation used by its targets.”
Related Posts:
- Researcher found a new attack vector, MOSQUITO that can allows Air-Gapped Computers to masked Exchange Data
- Reseachers show how to steal the encrypted currency wallet private key from the air gap PC
- North Korean Hackers Exploit Old Office Flaw to Deploy Keylogger